Top ECSA Tools with Infosec Train

EC-council certified security analyst (ECSA) program offers comprehensive methodologies of advanced pen testing and their implementation on modern security infrastructure, operating systems, and application environment. ECSA training program focuses on how real-life penetration testing takes place. ECSA is a step forward to CEH (Certified ethical hacker) course and complements it in every sense. ECSA Certification program upskills a candidate’s knowledge about various advanced penetration methodologies. Also, it prepares an individual as per industry requirements by emphasizing areas such as drafting a useful assessment report for the different target audiences in the organization.
In this section, we have discussed some of the best-implemented tools to detect and exploit vulnerabilities during the ECSA training program at Infosec Train.
SHODAN
Shodan is a search engine that is used to detect everything that is connected to the internet, such as webcams, home security systems, traffic light, etc. Shodan command-line interface (CLI) is packaged with the python library. It is more efficient than the original website of Shodan. Penetration testing teams utilize the Shodan CLI to identify vulnerable devices in the network.
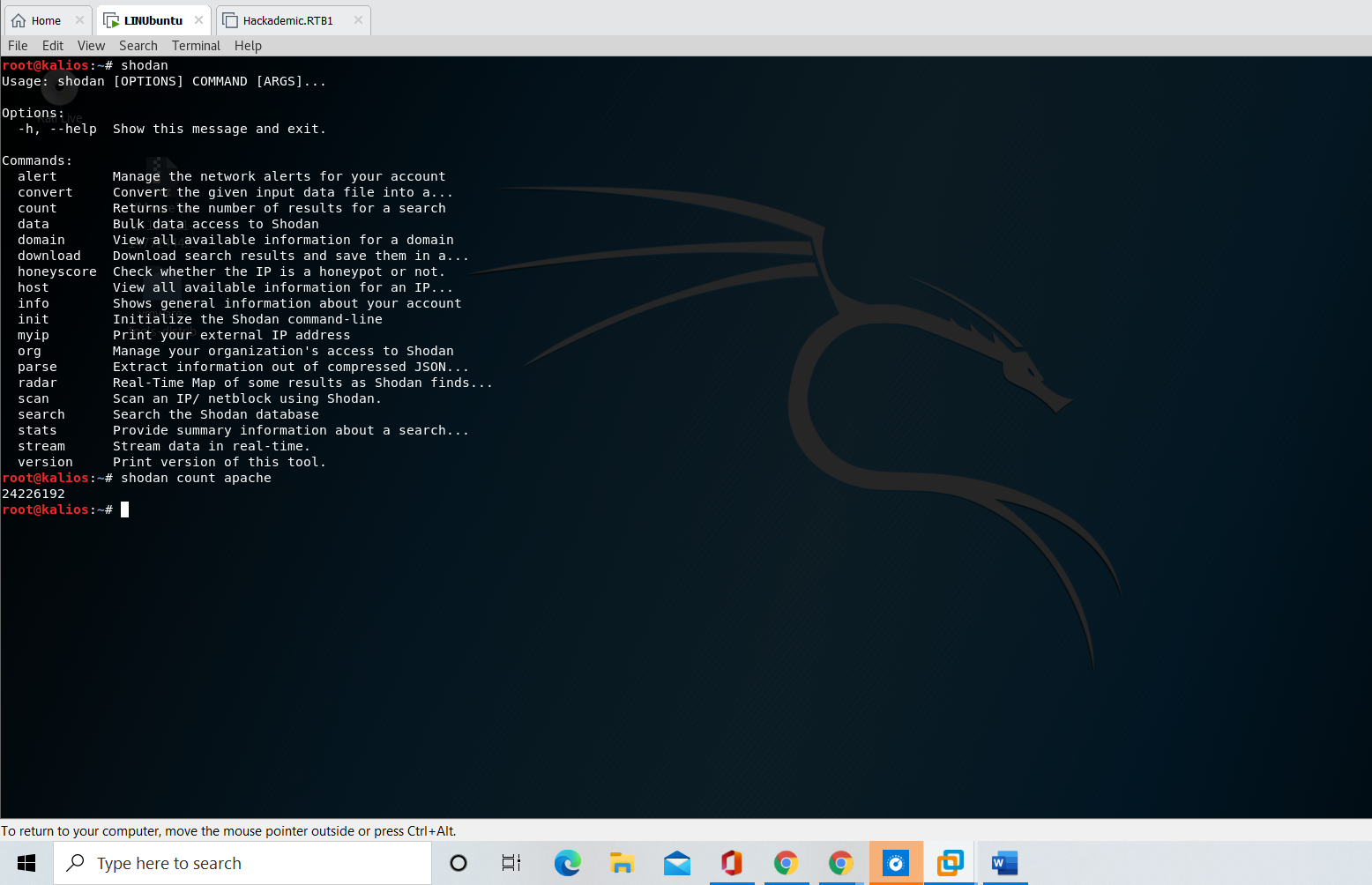
Maltego
Maltego is an open-sourced intelligence gathering tool to analyze information online. It connects the dots and presents the collected data into directed graphs for analysis. Information gathering with the help of manual techniques can be time-consuming. Maltego saves the time of the penetration testing team as it automates the process.
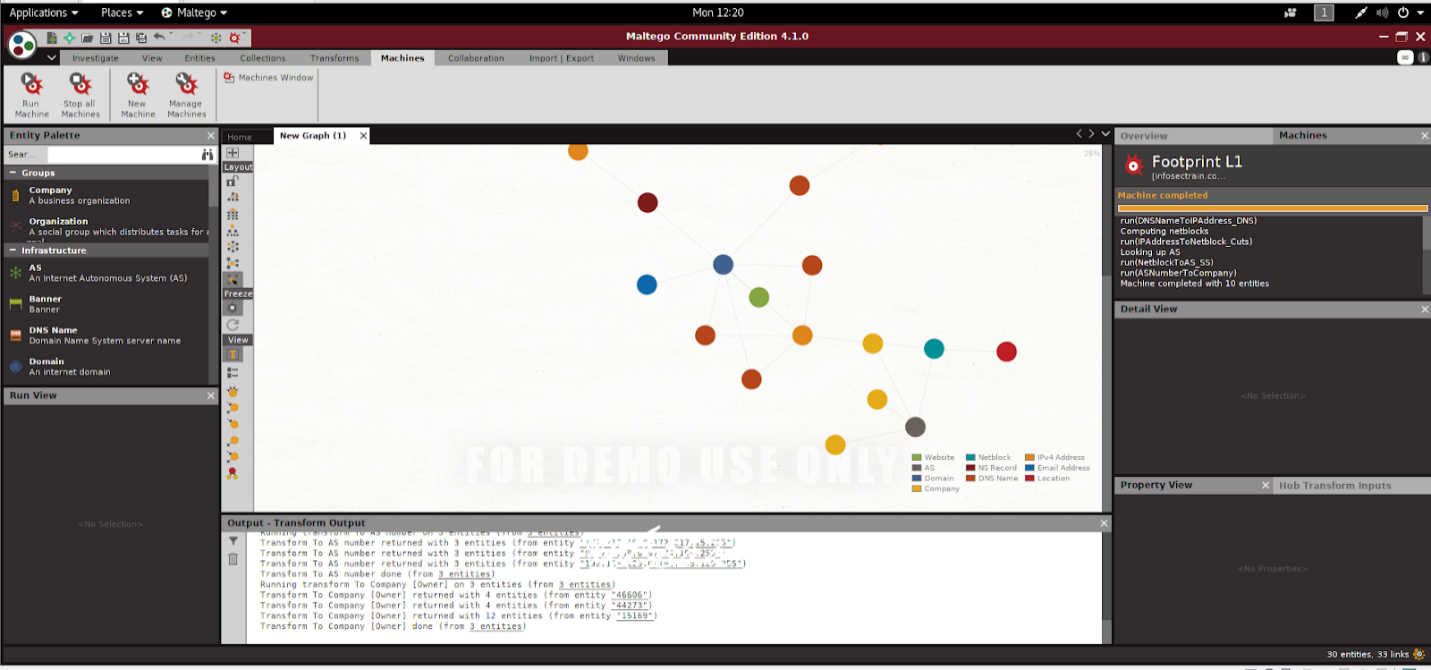
Nikto
Nikto is a powerful tool that scans web servers to identify potential security issues and vulnerabilities such as dangerous files, outdated program versions, vulnerable servers, and many more against the items on the web. It supports Windows and Linux platforms.
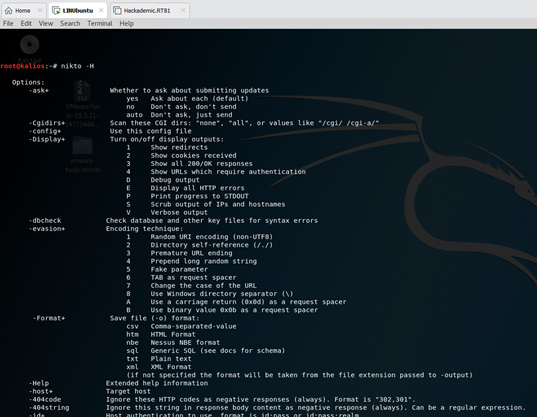
Owasp ZAP
ZAP (Zed Attack Proxy) is a free and open-source tool to scan vulnerabilities in web applications or websites. It is developed by OWASP (open web application security project). ZAP creates a proxy server and lets all the data of your site pass through it. Data is filtered by a scanner that detects vulnerabilities in websites.
Gophish
Gophish is a powerful tool to check the susceptibility of an organization against the phishing attacks. This tool enables us to launch and schedule a phishing campaign at large scale. It monitors the emails sent to the target organization and updates the results and provides you all the information such as email opens, link clicks, and submitted credentials.
Mimikatz
Mimikatz is an open-source tool used for obtaining the credentials and escalating privileges. Pen testers use this tool to exploit vulnerabilities in Windows authentication systems. mimikatz uses various methods to obtain credentials such as pass-the-hash, pass-the-ticket, and golden-Kerberos-tickets and pass-the-cache
Wifiphisher
Wifiphisher is a powerful tool that facilitates red teams to test Wi-Fi security. With the help of this tool, a Penetration tester can obtain the man in the middle position against wireless clients. Wifiphisher can be utilized to organize phishing attacks against the client connected to the wireless network. It is easier to use and provides more flexibility.
NetworkMiner
NetworkMiner is a free, open-source network forensic analysis tool used to analyze the network traffic. It can monitor the traffic in real-time and save the captured data in pcap format, which can be quickly investigated offline in the future. NetworkMiner can extract the files in network traffic to detect the files that contain malicious content. This is a powerful tool that can perform advanced network analysis and also identify operating systems, sessions, hostnames, and open ports.
CHERRYtree
CHERRYtree is a free and open-source application that is used to take hierarchical notes. The application can store text, files, images, tables, and executable snippets of code in a single XML or SQLite file. Cherrytree application is used in the report writing phase of the ECSA.
It supports rich text formatting, advanced search options, keyboard shortcuts, syncing with the cloud services, exporting notes to HTML, and provides password protection to secure your notes.
For customized instructor-led ECSA Course, experts can get registered to Infosec Train. Learning and refreshing the skill is the best way to remain steady in cybersecurity, and ECSA preparing at Infosec Train is a brilliant chance to put resources into the occupation. For more details, please visit www.infosectrain.com






 1800-843-7890 (India)
1800-843-7890 (India) 
