What’s new in CND v2.0
Overview
With the wake of COVID-19, organizations have enabled workplace flexibility for their employees by promoting work from home culture. Thus, providing hackers an opportunity to exploit the vulnerable points and take advantage of the human factor. According to Tessian, 45% of respondents mentioned distraction as the reason for falling for a phishing scam while working from home. In the 2020 Data Breach Investigations Report by Verizon, web application attacks have increased twice as compared to 2019. While we are now comfortable with work from home environment, initially, not everyone was prepared; thus, many employees were working with personal laptops with inadequate security controls. Data flowing through these settings expose the entire network to risk. To control these kinds of situations, companies are now moving to a segmented network instead of a flat network and similar new requirements are arising for defending the organization’s network.
With security in mind and the aim of empowering the defenders, EC-council has announced CNDv2. Instead of a linear approach, a continuous adaptive security cycle is the need of the hour. CNDv2 provides a comprehensive approach to deal with modern network security issues.
Moving from the traditional cybersecurity approach of “protect and detect,” CNDv2 moves a step ahead towards “Predict, Protect, Detect, Respond.”
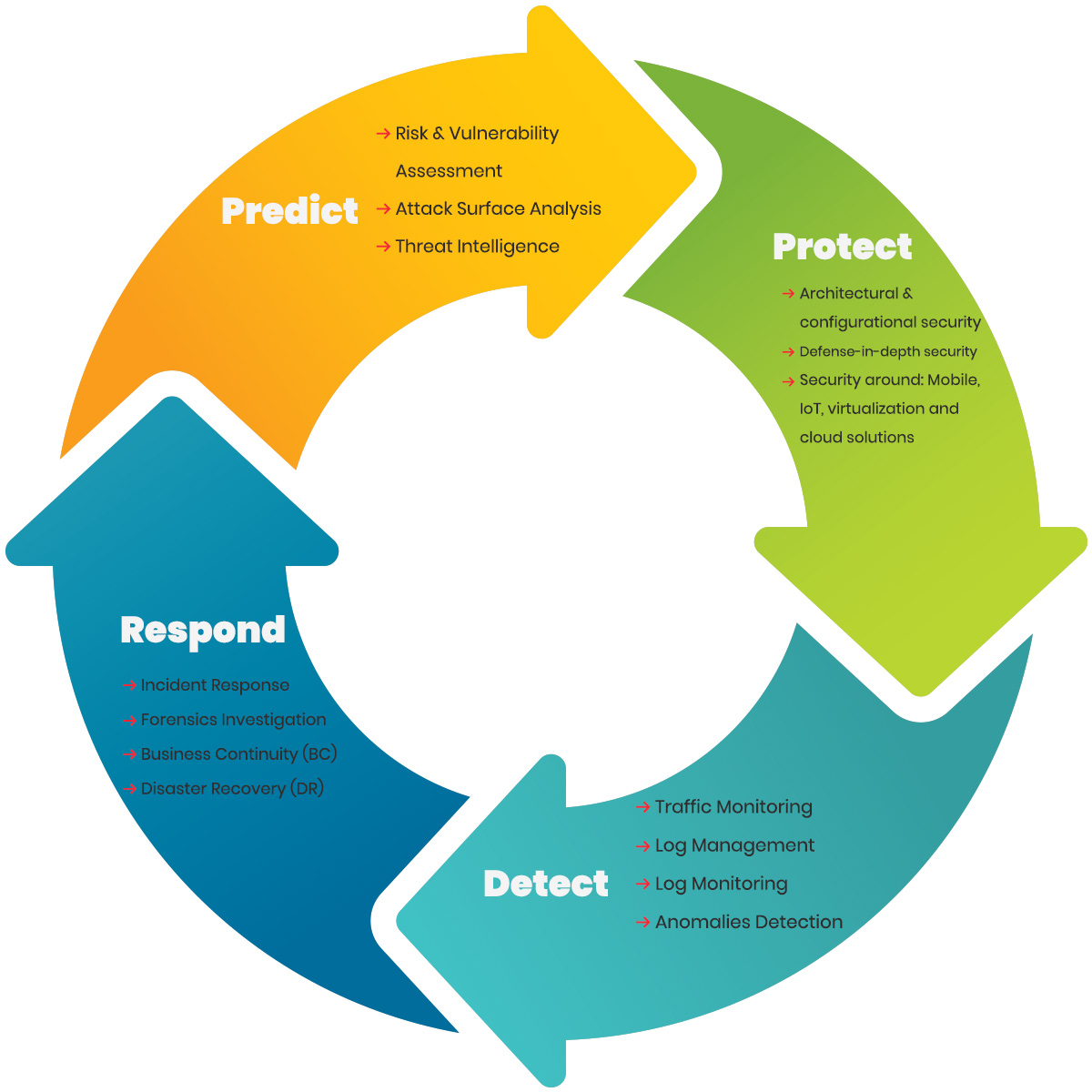
Course Objectives for CNDv2
CNDv2 has added and removed domains based on the current cybersecurity market analysis and requirement. The new version is based on the cybersecurity education framework and work role task analysis presented by the National Initiative of Cybersecurity Education (NICE). As compared to 14 domains in CNDv1, CNDv2 consists of 20 domains. The new CNDv2 certification exam validates the candidate on all critical aspects of the information and network security and helps them gain an in-depth understanding of:
- Modern network attacks and their defense strategies
- Various aspects of network security controls, including technical, administrative and perimeter security
- Securing entry points or end-user devices by ensuring endpoint security of Windows, Linux, IoT and mobile devices.
- Concept of data storage, data classification, data masking, retention and destruction
- Administrative application security and its role in minimizing the security vulnerabilities in the application
- IoT concepts, threats and countermeasures
- Core essentials of virtualization and its security in an enterprise environment, software defined network (SDN) security, network function virtualization (NFV) security
- Cloud computing, threats, challenges and security across cloud platforms (AWS, Azure, Google Cloud), container security, docker security, and Kubernetes security
- Wireless network security
- Monitoring and analysis of network traffic for anomaly detection
- Analysis and monitoring of logs and events for identification of any suspicious activity or a potential incident
- Incident management response process to deal with security incidents and understanding of forensics investigation techniques
- Risk anticipation and management, risk assessment, techniques of risk avoidance, prevention, mitigation and acceptance
- Business continuity planning and disaster recovery concepts and essentials
- Performing threat assessment and analysis of the attack surface, identification of vulnerable areas and their testing
- Threat intelligence fundamentals and its utilization in moving towards a better and proactive security approach
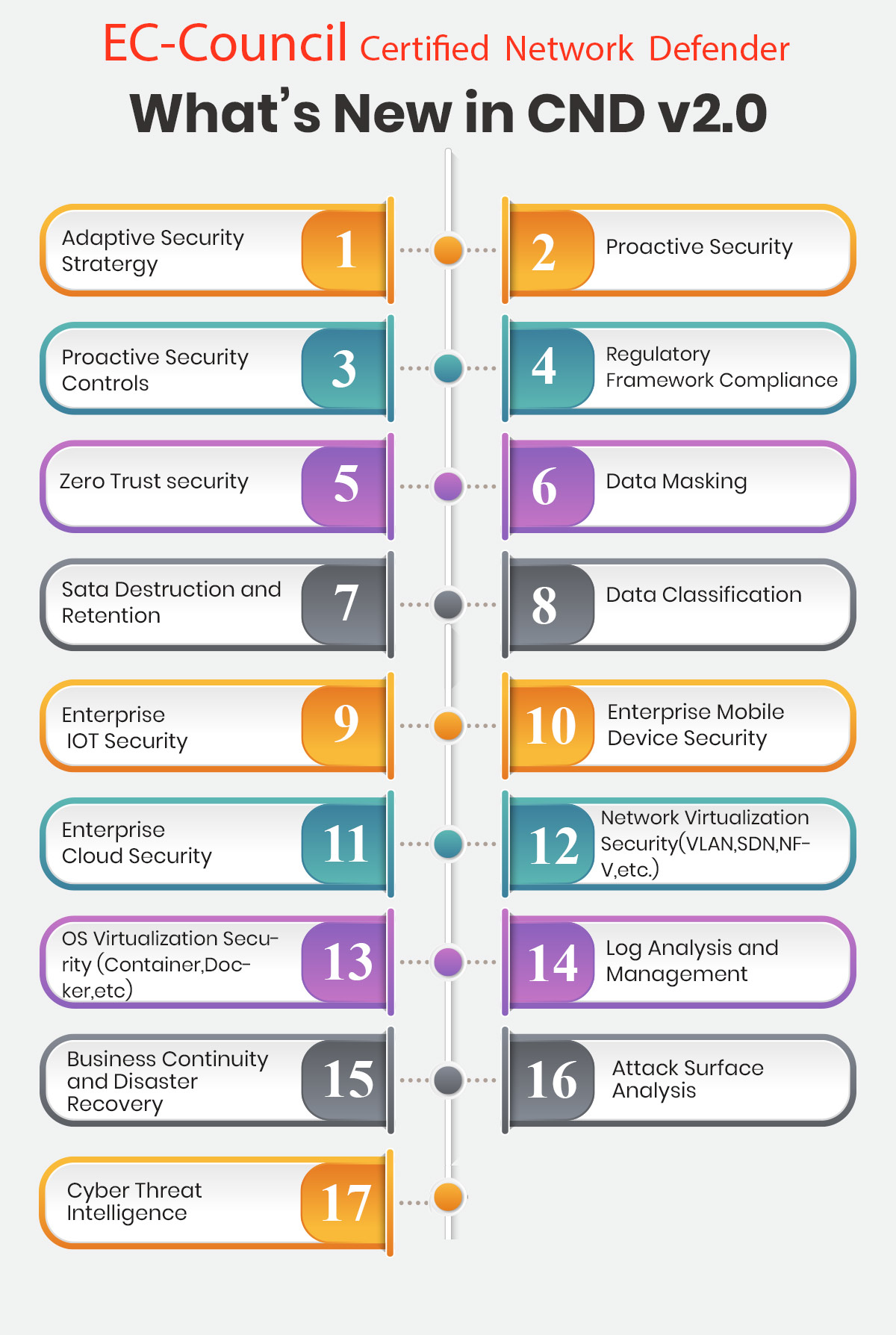
Compared to CNDv1, CNDv2 has almost double the number of labs, which gives candidates a chance to get extensive hands-on on various tools and clear their concepts about the underlying technologies.
The exam format and other aspects such as the eligibility criteria, duration of the exam remain the same. However, CNDv2 offers a much wider range of topics to provide a better understanding of network security in the current cybersecurity environment.







 1800-843-7890 (India)
1800-843-7890 (India)