Career opportunities after earning CEH certification
The Certified Ethical Hacker (CEH) certification, hosted by the EC-Council, is one of the most sought-after cybersecurity credentials that validate candidates’ skills to assess and exploit the vulnerabilities to prevent possible cyber-attacks. The CEH certification covers the latest tools and methodologies to invade the modern-day security infrastructures. It is one of the foundation courses that serve as a base for other advanced level certification programs. Many reputed organizations turn to CEH certification to hire professionals for cybersecurity job roles.

This article explores the career opportunities and options you have after earning the CEH certifications.
Career opportunities after earning the CEH certification
There are many career opportunities after earning the CEH certification. Some of the job roles mentioned below require additional certifications and higher qualifications along with the CEH certification.
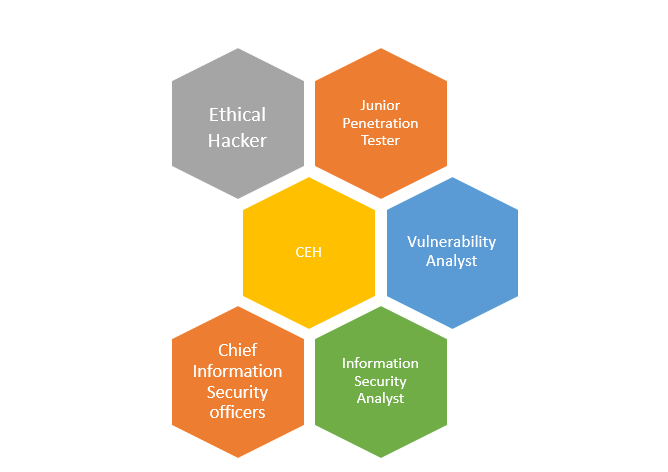
Ethical hacker
An ethical hacker is a professional who breaks into the systems and networks with the consent of the owner and identifies the exploitable vulnerabilities in the security posture. The certified ethical hackers are highly in demand today, as organizations face new sophisticated cyber-attacks at an alarming rate.
Career path
Roles and responsibilities of an Ethical hacker:
- Identifying the flaws in the security infrastructure
- Conducting penetration tests regularly
- Creating an actionable assessment report
- Ensuring the security tools are upgraded
- Raising awareness among employees of the latest social engineering attacks
Junior Penetration Tester
A junior penetration tester is an entry-level opportunity in the cybersecurity domain. Junior penetration tester conducts pen testing to identify and exploit weaknesses in the organization’s systems or networks lawfully and legitimately. After performing the penetration test, a penetration tester documents an assessment report citing the potential mitigating risks.
Career path
Roles and responsibilities of the Junior Penetration Tester
- Determining the goals and scope of the penetration test
- Planning and creating methods to conduct a penetration test
- Perform remote or on-site testing of the client’s network or the systems
- Meeting external or internal users to evaluate the output of the test
- Analyzing the impact of the vulnerabilities on the business
- Gathering your findings and outcomes of the test and generate the report
Vulnerability Analyst
A vulnerability analyst is a professional hired by an organization to identify and fix the vulnerabilities in the network and software programs. It is an important position to protect the organization from external threats. The role of vulnerability analyst is different from the pentester. A pentester identifies the vulnerabilities and exploit them while a vulnerability analyst identifies and fix those vulnerabilities.
Career path
Roles and responsibilities of the Junior Penetration Tester
- Determining the goals and scope of the penetration test
- Planning and creating methods to conduct a penetration test
- Perform remote or on-site testing of the client’s network or the systems
- Meeting external or internal users to evaluate the output of the test
- Analyzing the impact of the vulnerabilities on the business
- Gathering your findings and outcomes of the test and generate the report
Information Security Auditor
The Information Security Auditor is a professional hired by the organizations to audit and investigates the effectiveness of an organization’s IT security posture. Auditors are responsible for generating a security report based on their assessment, which further helps the organization formulating strategies to protect valuable assets from adversaries.
Career path
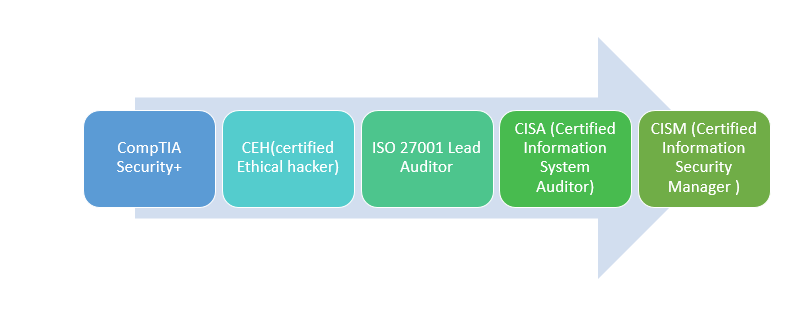
Responsibilities of an Information Security Auditor
- Planning, executing and leading the security audits for the organizations
- Interviewing employees to evaluate the ongoing security procedures
- Generate an auditing report
- Identifying vulnerabilities in the network and systems
- Review and assess the application controls
Information Security Analyst
An information security analyst is a professional employed by the organization that keeps track of an organization’s network and systems. He uses his strong analytical skills to identify and fix the exploitable vulnerabilities in the security infrastructure and generates a report based on assessment.
Career path
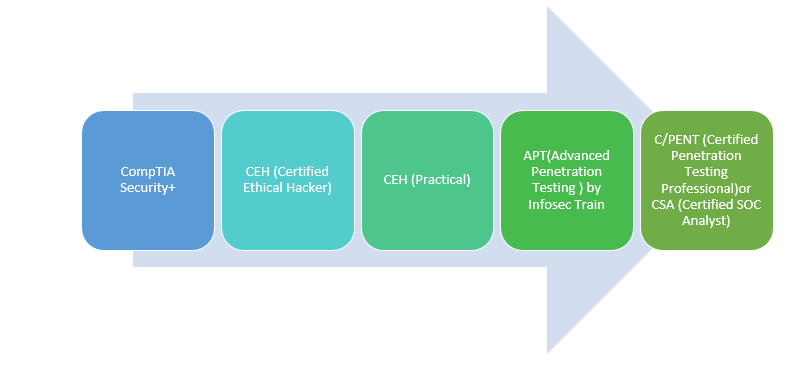
Responsibilities of an Information Security Analyst
- Installing firewalls and other security tools in the network to protect sensitive information
- To lead the organization to counter the attack, mitigate all the possible risks associated with it
- Making incident response & post-recovery plans
- To train employees and users about essential security protocols
- Conducting internal as well as external audits to ensure the overall security of the organization
- Keeping themselves up-to-date with the latest security trends and standards
Chief Information Security Officer (CISO)
The chief information security is a C-level post in the organization. The CISO is responsible for managing the organization’s security infrastructure and ensuring the security of critical information assets and the IT environment of the organization.
The chief information security officer’s profile requires strong leadership, communication skills, and a thorough understanding of the IT infrastructure.
Career path
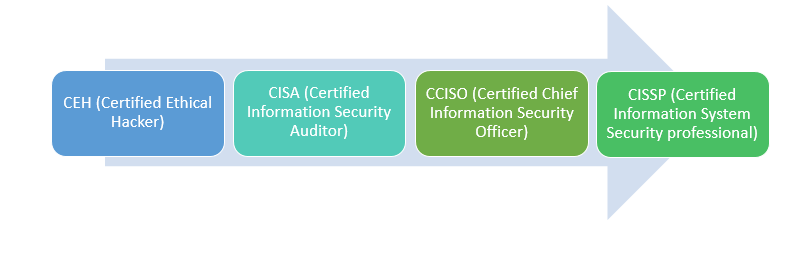
Roles and responsibilities of Chief Information Security Officer
- Hiring security professionals
- Ensuring the coordination at multiple levels of the organization’s structure
- Organizing campaigns to raise awareness among employees
- Determining the security budget for the organization
- Ensuring the security IOTs, managing enterprise risks, and establishing security analytics
Get certified with Infosec Train
Infosec Train is a leading IT security training providers worldwide. We offer training programs for the Certified Ethical Hacker (CEH) and all the certifications mentioned above. Our certified and qualified instructors are well-versed in the respective domains. They follow comprehensive teaching methodology and focus more on practical knowledge to transform individuals into highly skilled professionals.
Key features of our CEH Training program
- 40 hours of instructor-led training
- Blended delivery model (emphasizing practical knowledge along with theory)
- Certified & Experienced Trainers
- 24/7 technical support
- Get access to recorded training sessions
Join us today to earn the Certified Ethical Hacker (CEH) and other reputed certifications to forge a promising career in the cybersecurity domain.







 1800-843-7890 (India)
1800-843-7890 (India)