Infosec Train’s SOC Analyst Training Program
The security operation center is a facility in an organization that houses Cybersecurity professionals to analyze, monitor, architect and manage an organization’s security posture. A SOC team comprises Security managers, security engineers, and SOC analysts. The team is responsible for monitoring the overall organizational infrastructure and protect it from potential Cyberthreats. .

The recent reports have shown the increment in data breach incidents and cyberattacks. These incidents have caused substantial financial and reputational damage to the businesses. Therefore, Organizations need human experts’ involvement to monitor the security infrastructure and identify potential or ongoing security threats more than ever.
This section will discuss everything about the newly launched Infosec Train’s SOC Analyst training course. But before moving ahead, let’s understand the SOC Analyst job description.
What is a SOC Analyst?
SOC Analysts are the first line of defenders as they monitor the systems, detect, respond, and investigate the ongoing security incidents. There are three levels of SOC analysts: Tier 1, Tier 2, and Tier 3.
Tier 1: The Tier 1 or L1 SOC analysts are triage specialist. Tier 1 SOC analysts are responsible for monitoring the incidents and determining their urgency and severity. They alert the Tier 2 SOC analyst by raising the trouble tickets and manages the security tools.
Tier 2: The Tier 2 or L2 SOC analysts respond to the security threats. They identify the infected systems and determine the scope of the attack. Their responsibilities include collecting data for the investigation and formulate remediation and recovery plans.
Tier 3: A tier 3 or L3 SOC analysts review the vulnerability assessment report. They use advanced threat intelligence methods to find out the security threats present in the system. Tier 3 SOC analysts are also capable of conducting penetration tests to detect vulnerable endpoints in the network.
About Infosec Train’s SOC Analyst training program
SOC Analyst training program is carefully designed by the experts and industry veteran at InfoSec Train. It aims to provide Tier 1, Tier 2, and Tier 3 SOC analysts with skills and knowledge to successfully perform SOC operations. It starts from the intermediate level and takes you through advanced digital forensics and incidence response concepts. You will be getting hands-on exposure to the latest tools and technologies used by the SOC analysts to combat advanced cyber threats.
This extensive training program will enable you to:
- Understand the SOC operations, workflows, and processes of building a successful SOC team
- Get your hands on a range of SOC tools, including ELS Stack, IBM QRadar, Splunk AlienVault OSSIM, and many more
- Strengthen your digital forensics concepts, including the live forensics and post-investigation
- Interpret operational threat intelligence, strategical threat intelligence, and tactical threat intelligence
- Understand the advanced persistent threats and how to respond to these threats
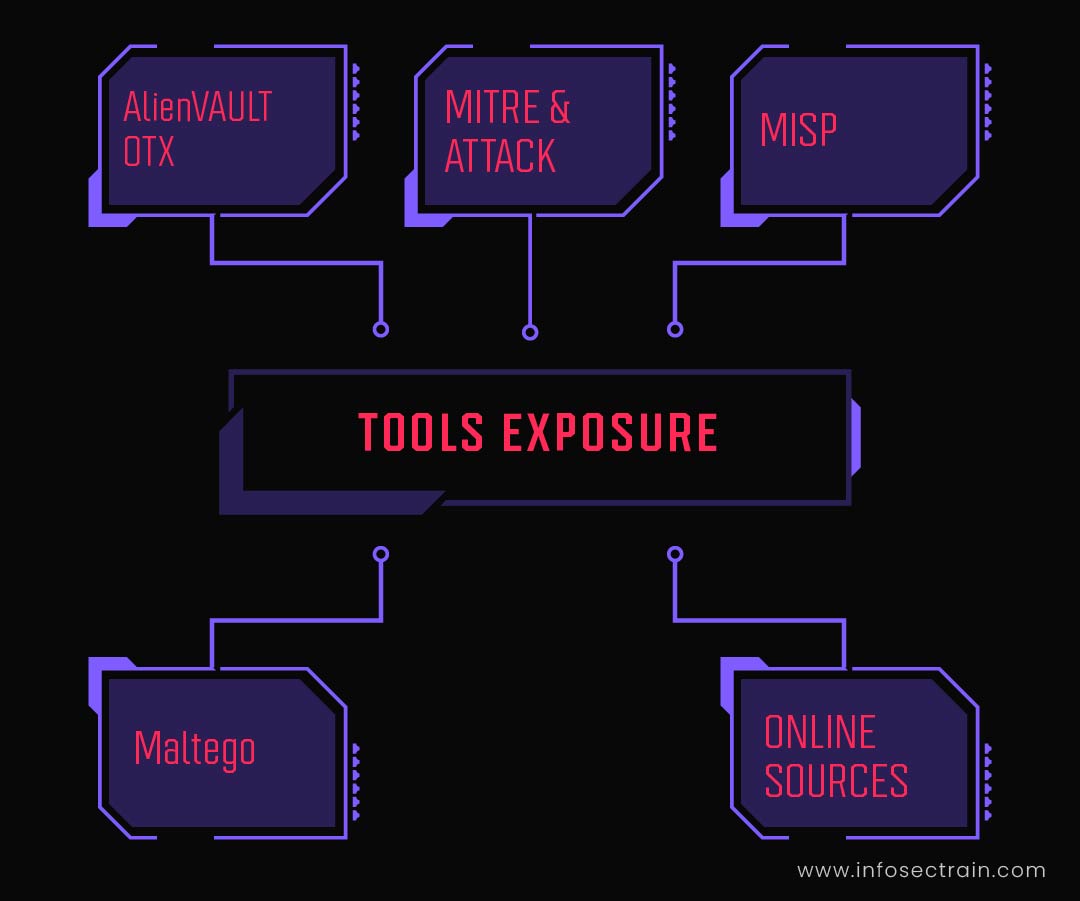
Major tools covered in the course
The following infographic shows the widely used SOC analyst tools that you will get your hands on while advancing in the training course.
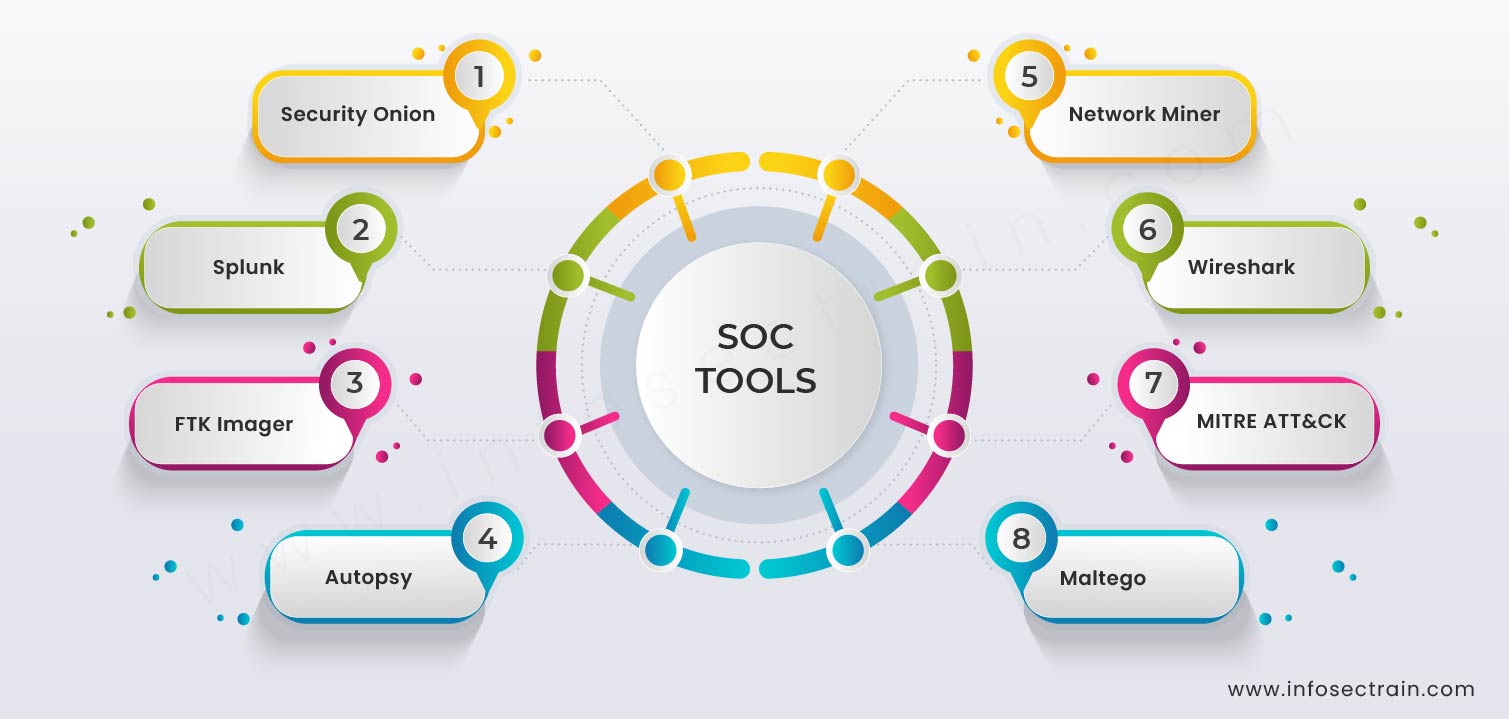
Domains of the training course
Here are the four domains that you will learn in this training course:
1. SOC Operation Center
2. Digital Forensics
3. Incidence Response
4. Threat Intelligence
The details of each domain and tools exposure provided in the domains are as follows:
Domain1: Security Operations Center
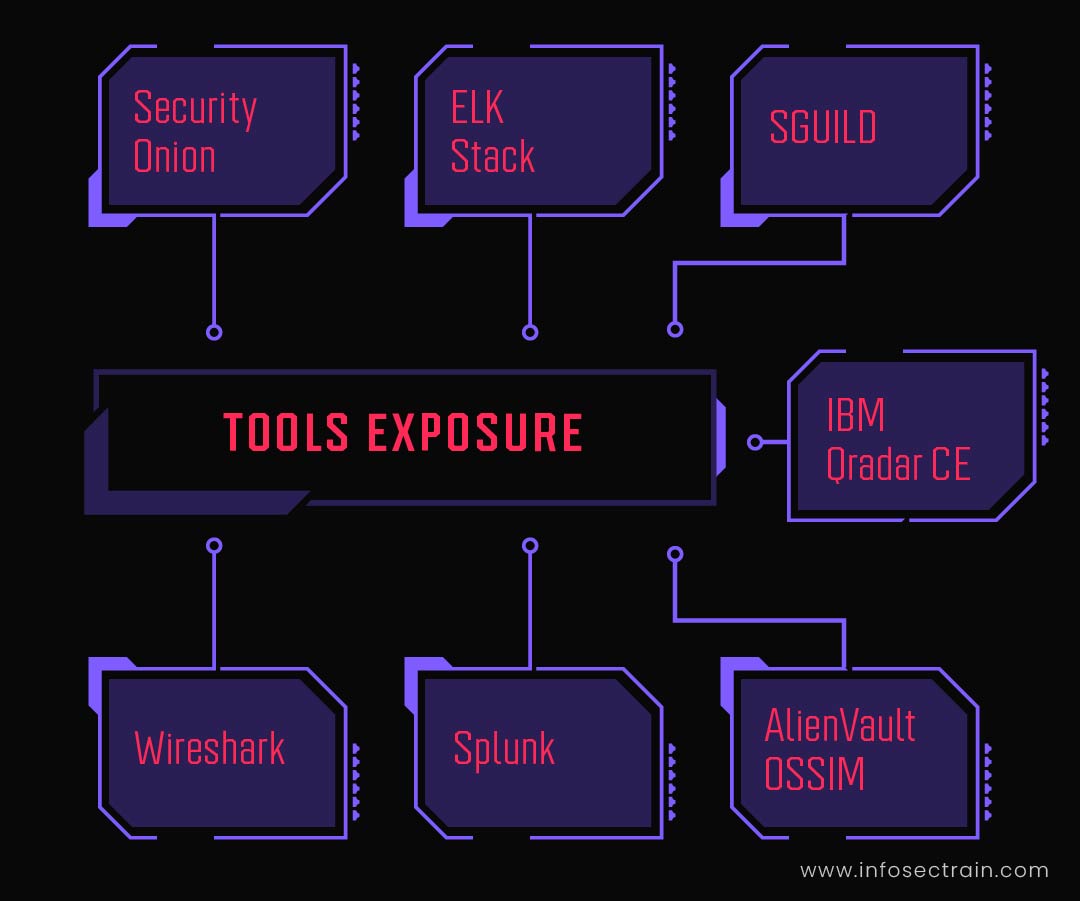
The domain gives a deep insight into the security operation center, its functions, and how to build a successful SOC team. You will be able to interpret the Security Information and Event Management (SIEM) known as the heart of a SOC team. The domain will let you know the SIEM guidelines and architecture in detail. The other subtopics include:
- Introduction to QRadar
- Splunk in depth
- Monitoring
- Fun with logs
- AlienVault OSSIM Fundamentals
Domain 2: Digital Forensics
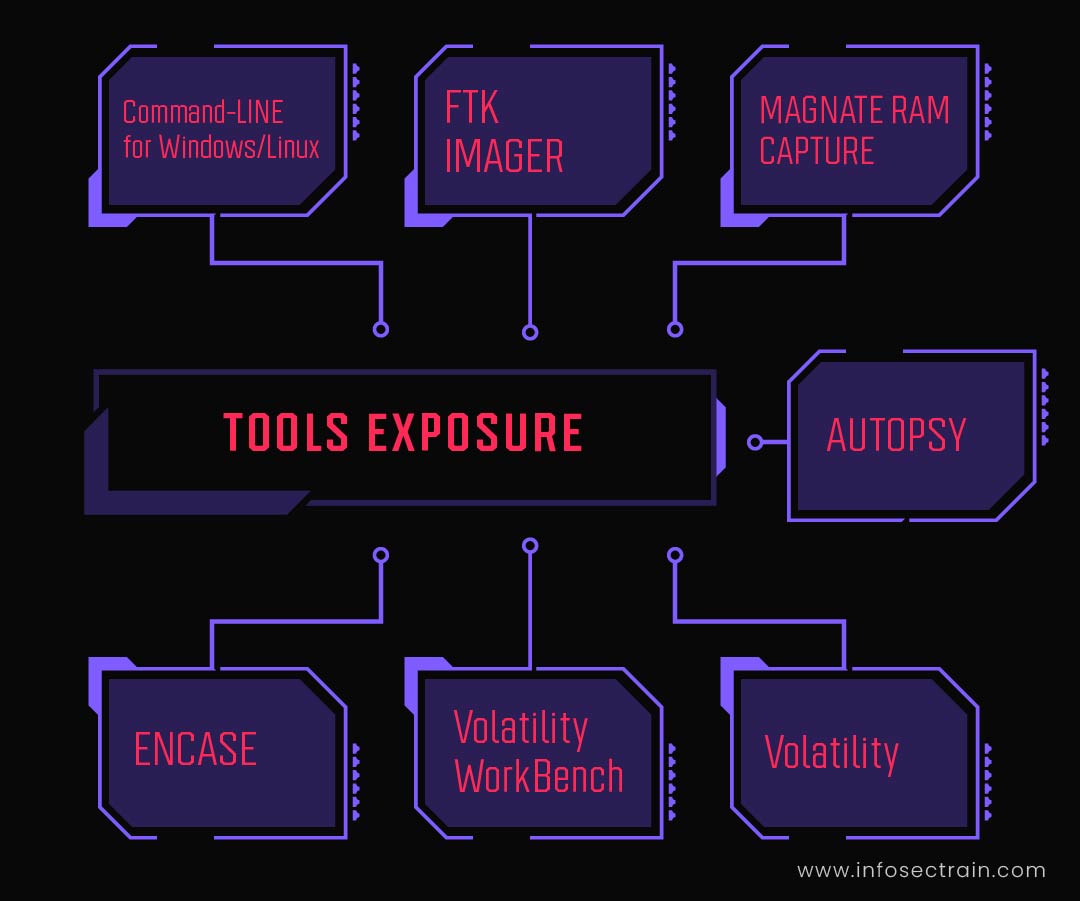
To prevent the Cyberattack successfully, a SOC analyst must be well-versed in digital forensics techniques. Understanding of digital forensics help SOC analyst to analyze, collect, and report the crucial data. They can gather the pieces of evidence of data breach and utilize them to prevent further breaches. You will learn an introduction to digital forensics, forensic fundamentals, evidence forms, the chain of custody, windows investigations, *nix investigations, and live forensics in this domain. The domain will also take you through the post-investigation processes such as:
- Post-investigation processes
- Report writing
- Lessons learned
Domain 3: Incident Response Domain
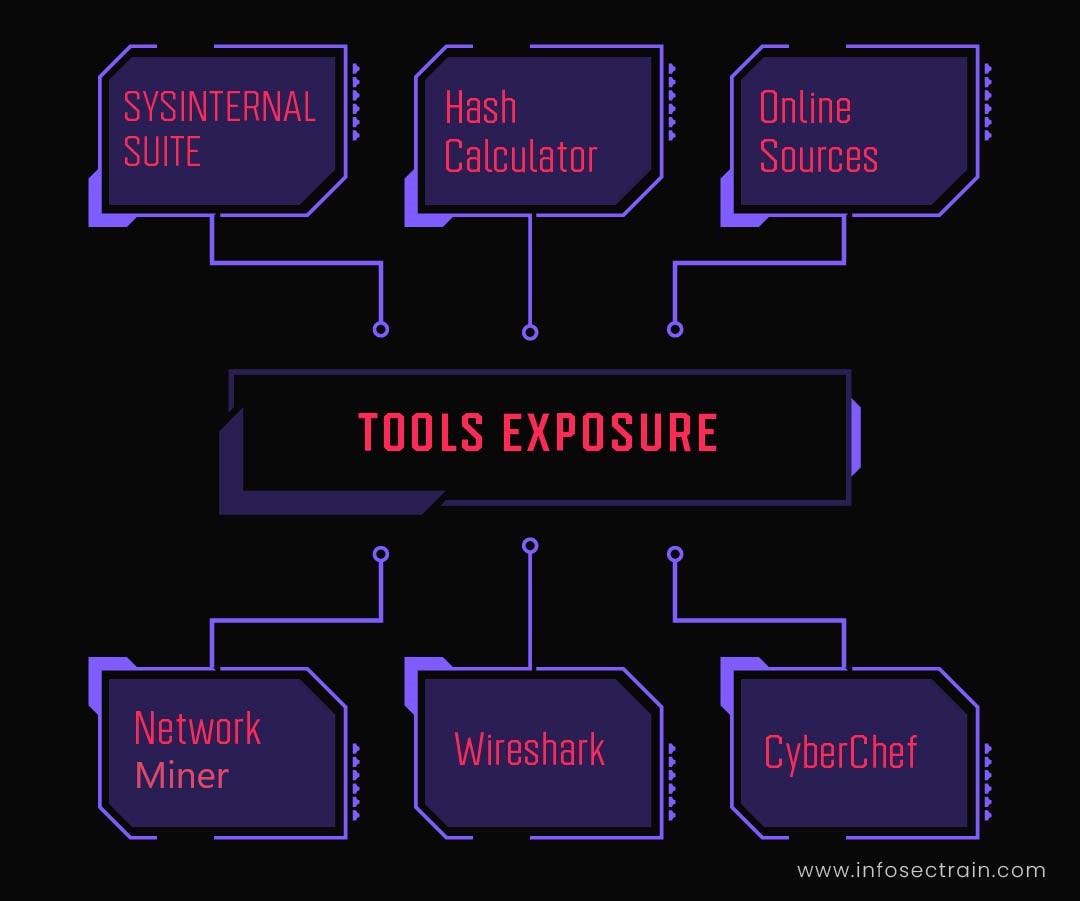
Incidence response skills are crucial for SOC analysts to manage and mitigate the risks of cyberattacks. An incidence response’s objective is to reduce the damage caused by the cyberattacks and recover from them as early as possible. The SOC analyst must be efficient in responding to the incidents and improving the existing security controls to prevent future data breaches.
The domain will enable you to:
- Differentiate between security events vs. security incidents
- Understand Incidence response lifecycle
- Learn the MITRE ATT&CK framework
- Detection and analysis
- Understand containment, eradication, and recovery
- Know the importance of documentation
Domain 4: Threat Intelligence Domain
Cyber threat intelligence is vital for the modern-day organization. Collecting useful threat intelligence help SOC analyst to outsmart the malicious attackers. The threat intelligence domain begins with explaining threat intelligence and its value in the present time. Besides this, you will learn the following:
- Threat actors
- Advanced persistent threats
- Operational intelligence
- Tactical threat intelligence
- Strategic threat intelligence
Check out the detailed course content of the SOC Analyst training course here: Detailed Course outline of Infosec Train’s SOC Analyst training
Salient features of the training
- Meticulously designed course content
The course content is carefully designed by the industry veteran and thought leaders of Infosec Train. Each section of the course content is developed to hone the necessary skillset of aspiring SOC analysts at each level. The course curriculum addresses some of the most vital areas in designing and creating a successful SOC team.
- Level up your existing skills
The training course provides a comprehensive understanding of various SOC operations, workflows, technologies, and tools used by the SOC analysts. The topics and tools coverage are added to fulfill the current industry or corporate requirements. The participants will learn the advanced concepts of monitoring, determining the severity of the incidents, threat intelligence techniques, digital forensics to investigate the breaches.
- A practically driven training program
Infosec Train’s SOC Analyst training course provides hands-on learning experience of implementing various SIEM solutions, performing log analysis, and getting their hands on the cyber threat intelligence and digital forensics tools. Infosec Train provides its trainees access to the well-constructed cloud-based labs to practice the concepts learned in the training sessions. We provide all the technical support to the participants even after the completion of the training.
- Learn from industry veterans
The instructors at Infosec Train are certified and highly skilled. They have given their valuable contribution to the information security community. Their years of training experience help individuals turn into elite Cybersecurity professionals. The training sessions are quite interactive that enables participants to clear the doubts enhance their analytical skills.
- Job interview preparation
At the end of the training, instructors ensure that you have obtained every skill to become an integral part of a SOC team. They review and evaluate your skillsets and make sure you are a perfect fit for the corporate. The expert guidance will put you in the right spot for getting hired by employers.Check out this blog to know the frequently asked SOC Analyst interview questions: 20 Most common SOC interview questions
- Get a certification of participation
Earning the certifications is an excellent way to validate your SOC Analyst skills and demonstrate how committed you are towards your professional growth. At the end of our SOC training, a certificate of participation will be provided by the Infosec Train, validating your skills to perform complex SOC functions.
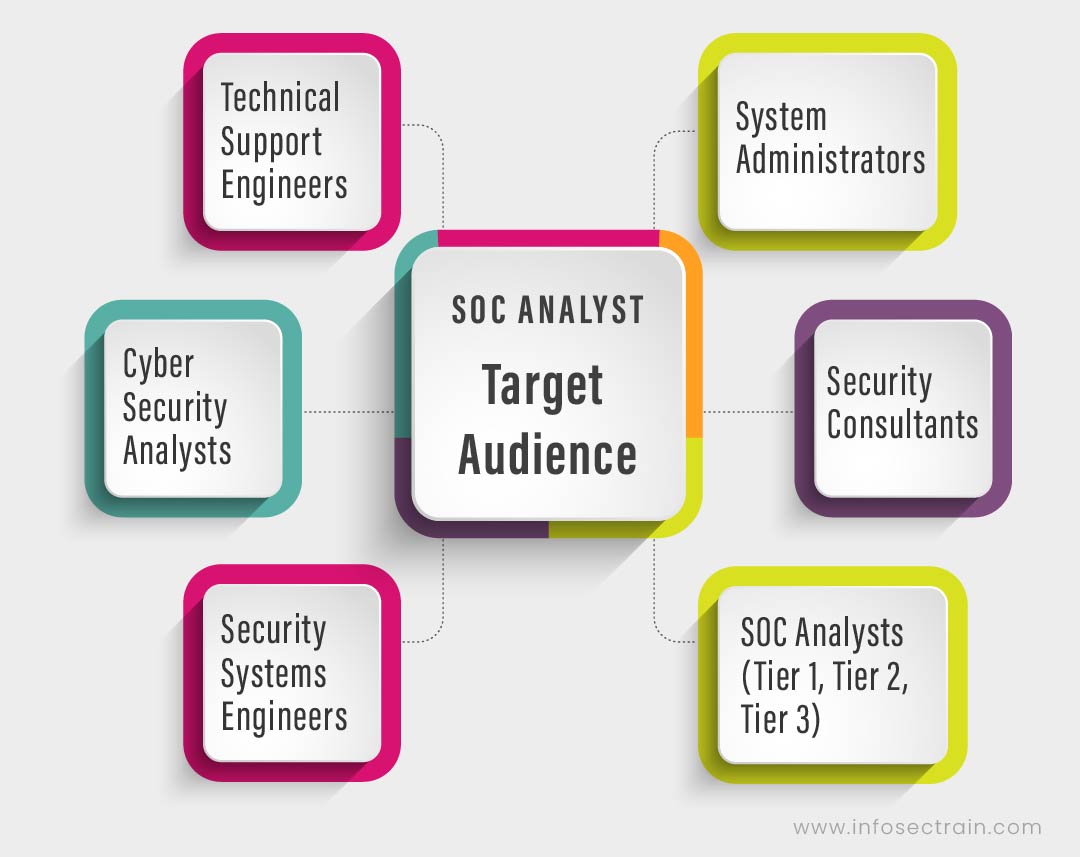
Target Audience
The SOC Analyst training may aid the following job roles:
Pre-Requisites
- Knowledge of Basic Networking, OS, and Troubleshooting is recommended
- Experience as an entry-level SOC Analyst, Cyber Security Analyst role is a plus
Wrap up
SOC Analyst is an emerging career opportunity in information. Many organizations nowadays are looking forward to hiring SOC analysts to protect their critical information assets from Cybercriminals. The SOC analysts can work with many crucial industries such as Healthcare, Finance, Education, and Manufacturing. The SOC Analyst training program is an excellent opportunity to level up your skills and expertise to work efficiently within a SOC team. Infosec Train’s SOC Analyst training program







 1800-843-7890 (India)
1800-843-7890 (India)