CCSP Domain 1: Cloud Concepts, Architecture and Design
The Certified Cloud Security Professional Certification or CCSP, is a credential offered by (ISC)2 and the Cloud Security Alliance (CSA) in collaboration. For information security practitioners who wish to specialise in cloud computing security, the CCSP is an excellent credential to obtain. It was created by (ISC)2 to ensure that cloud security professionals have the necessary expertise, skills, and abilities in cloud security design, implementation, architecture, operations, controls, and regulatory framework enforcement. A CCSP demonstrates excellence in cloud security architecture, design, operations, and service orchestration by applying information security expertise to a cloud computing environment. This professional expertise is assessed against a body of information that is universally accepted.

The topics covered by the CCSP Common Body of Knowledge (CBK) ensure its applicability across all cloud security disciplines. The CCSP exam comprises of six domains:
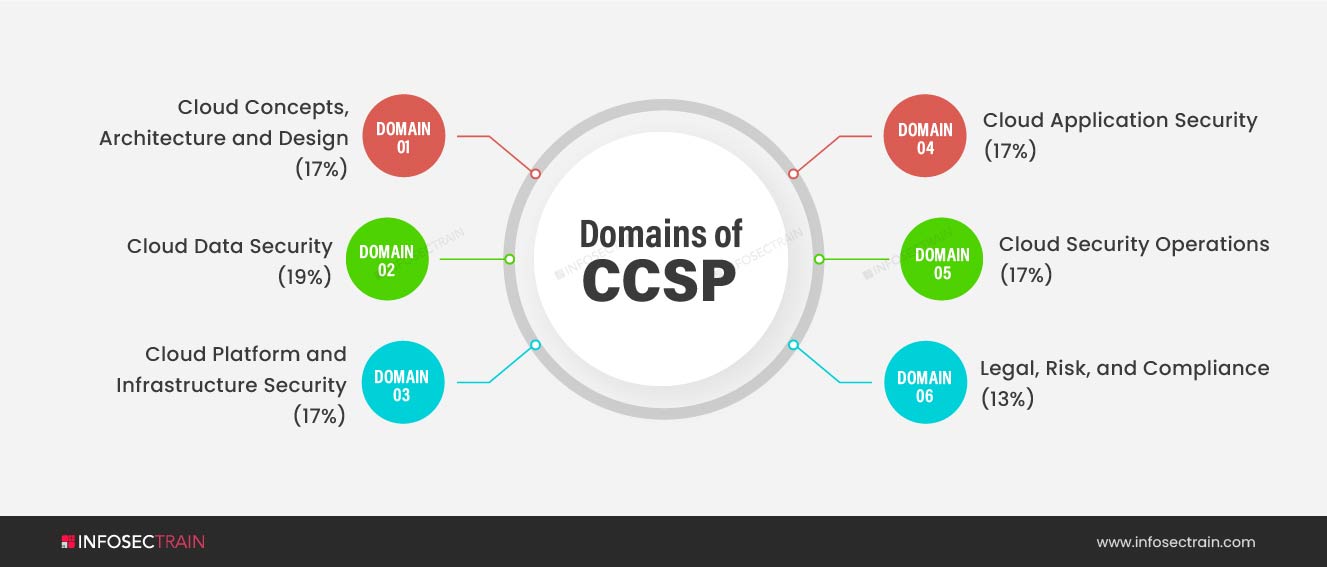
- Domain 1: Cloud Concepts, Architecture and Design (17%)
- Domain 2: Cloud Data Security (19%)
- Domain 3: Cloud Platform & Infrastructure Security (17%)
- Domain 4: Cloud Application Security (17%)
- Domain 5: Cloud Security Operations (17%)
- Domain 6: Legal, Risk and Compliance (13%)
This blog will cover the CCSP Domain 1: Cloud concepts, Cloud architecture and design; and what candidates preparing for this exam should expect in this domain.
Cloud Concepts, Architecture, and Design
The Cloud Concepts, Architecture, and Design domain lays the foundation for a strong understanding of cloud computing’s fundamentals. The ISO/IEC 17788 standard serves as the foundation for these building blocks. The domain defines various and significant roles that individuals and other organisations play within a cloud implementation, from the standpoint of both the cloud service provider and the cloud service customer. It holds 17% weightage and covers the following:
- Understand Basics of Cloud Computing
- Explain the Cloud Reference Architecture
- Understand Cloud Computing Security Concepts
- Understand Secure Cloud Computing Design Principles
- Evaluate Cloud Service Providers
Understand Basics of Cloud Computing
This subsection provides an overview of the basic cloud computing definitions and terminologies, and cloud computing roles. It covers the key characteristics of cloud computing, including on-demand self-service, broad network access, multitenancy, rapid elasticity and scalability, resource pooling, and measured service. It also covers the fundamentals of cloud computing, such as virtualization, storage, networks, and the underlying infrastructure that host and manage them. The primary goal of this domain is to see if the candidate understands the basic components of cloud computing.
Explain the Cloud Reference Architecture
The Cloud Computing Architecture is covered in this section, which introduces cloud computing operations, cloud service capabilities, cloud service types, cloud deployment models, and cross-cutting aspects of cloud computing that affect all aspects of cloud implementations and deployments. The main roles of the cloud service provider, cloud service customer, and cloud service partner, as well as the broad range of sub-roles encapsulated under each, are included in the ISO/IEC 17789 standard for cloud computing activities. The key cloud service capabilities are introduced and described, including application, infrastructure, and platform service capabilities, as they are the backbone of many of the widely used and understood cloud structures and models. Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) are among the major cloud service categories discussed in this section which are deployed on a public, private, hybrid and community cloud.
The final component is a set of cloud computing’s cross-cutting aspects that apply to all cloud environments, regardless of service category or deployment model. It includes interoperability, portability, reversibility, availability, security, privacy, resiliency, performance, governance, maintenance and versioning, service levels and Service Level Agreements (SLA), auditability, and regulatory. It also discusses the impact of related technologies such as machine learning, artificial intelligence, blockchain, containers, Internet of Things (IoT), and quantum computing.
Understand Cloud Computing Security Concepts
Cloud computing has its own set of security concepts. On the CCSP certification exam, the following security concepts are likely to be covered:
- Cryptography and Key Management
- Access Control
- Data and Media Sanitization
- Network Security
- Virtualization Security
- Common Threats
All of these are somewhat close to a traditional data centre model, except in a cloud environment with multi tenancy, the value of cryptography is substantially higher, since many customers share the same pool of resources, rather than being isolated in a traditional data centre. This is also true for the particular challenges of access control, data and media sanitization, network security, virtualization security, and common threats.
Understand Secure Cloud Computing Design Principles
This subsection describes the specific design requirements for secure cloud computing. Although certain aspects of a cloud environment are similar to those of a conventional data centre, some aspects of a cloud environment involve special requirements or methodologies. These includes:
- Cloud Secure Data Lifecycle
- Cloud based Disaster Recovery (DR) and Business Continuity (BC) planning
- Cost Benefit Analysis
- Functional Security Requirements
- Security Considerations for different Cloud categories
Evaluate Cloud Service Providers
Since cloud customers do not host and monitor the entire cloud environment, they must rely on other methods to verify a cloud provider’s security posture and operations. One simple and reliable method is to examine independently verified and confirmed certifications. These certifications are focused on universally available and well-understood criteria and specifications, and they serve as a way to trust a cloud provider’s security posture and controls, as well as to compare various providers. It includes:
- Verification Against Criteria (e.g., International Organization for Standardization/International Electrotechnical Commission (ISO/IEC) 27017, Payment Card Industry Data Security Standard (PCI DSS))
- System/subsystem Product Certifications (e.g., Common Criteria (CC), Federal Information Processing Standard (FIPS) 140-2)
CCSP with Infosec Train
Earning the internationally recognised CCSP cloud security certification is a proven way to advance your career while also enhancing the security of sensitive cloud resources. InfosecTrain’s Certified Cloud Security Professional (CCSP) training course will assist candidates in updating and refreshing their skills as well as recognizing areas in which they need to study while preparing for the CCSP exam. We are one of the most well-known training providers. Our accredited instructors have years of experience in the industry, which they impart during training. This course will provide you with in-depth knowledge of fundamentals of cloud architecture, cloud architecture design, types of cloud architecture, cloud computing security concepts, etc.






 1800-843-7890 (India)
1800-843-7890 (India)