How to Become a Threat Analyst?
Today, the Cybersecurity industry faces various challenges, including increasingly determined threat actors, data full of irrelevant information and false alarms, unconnected security systems, and a serious shortage of skilled professionals. Although around $124 billion will be spent worldwide on Cybersecurity products and services in 2021, throwing money at these problems won’t be enough. Right now:
- Three-quarters of security organizations are experiencing skills shortages
- 44 % of security alerts go uninvestigated
- 66% of companies are breached at least once

What is Threat Intelligence?
Cyber Threat Intelligence (CTI) is gathered information that an organization uses to understand the structure of the damage that the industry is experiencing. This data is also utilized to predict and either avoid cyber attacks. With its capacity to understand data, risk intelligence offers you a context that enables you to generate informed decisions regarding your safety by responding to issues. It also gives a blueprint for the motives of the robbers and their ability to hurt the organization.
Why Do Organizations Need Threat Analysts?
Cyber Threat Analysts are security professionals that monitor and investigates external data threat and produce actionable intelligence. Furthermore, Cyber Threat Analysts will analyze data of security events to provide threat intelligence feeds and create a report that will help make decisions about organizational security.
Who takes benefits from Threat Intelligence?
Security operations teams are routinely unable to process the strong flow of alerts they receive. Threat intelligence can be integrated with the security resolutions they already use, helping them automatically prioritize and filter alerts.
Vulnerability management teams need to prioritize the most significant vulnerabilities correctly. Threat intelligence gives access to external insights that helps them differentiate immediate threats to their particular enterprise.
Fraud prevention, risk analysis, and other high-level security staff are challenged to learn the current threat landscape. Threat intelligence gives key insights on threat actors, plans, targets, and tactics, techniques, and procedures (TTPs).
What is a Threat Intelligence LifeCycle?
Traditional intelligence concentrates on six different phases that are called the “Intelligence Cycle”: Threat Intelligence provides a solution to many problems. It can filter out false alarms, speed up triage, and simplify incident analysis.
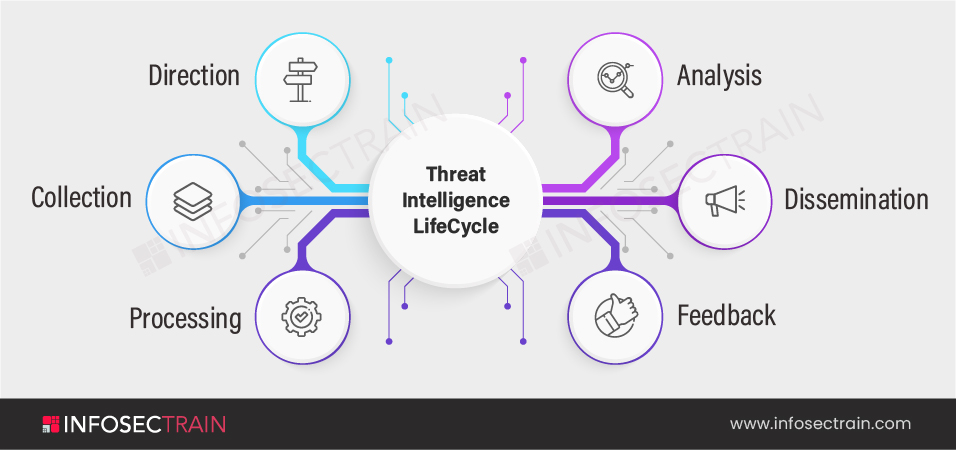
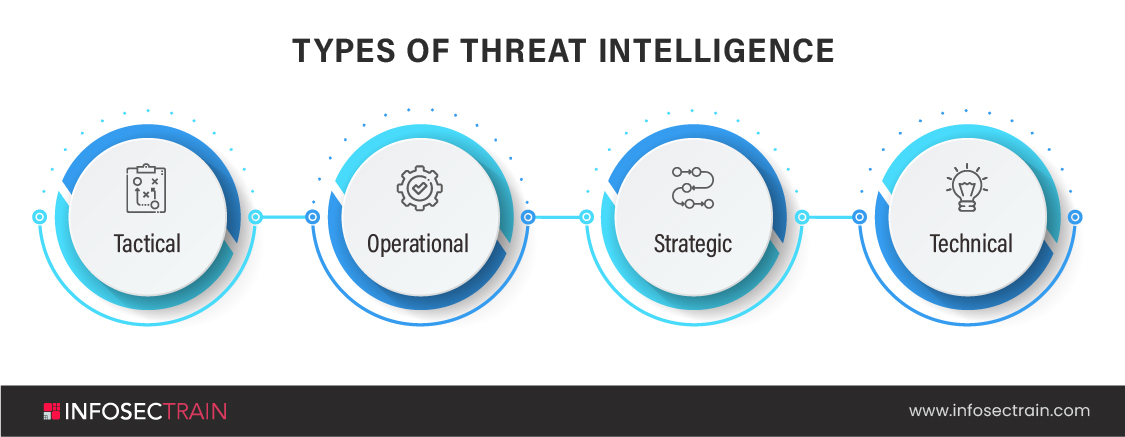
How to become a Threat Analyst?
Certified Threat Intelligence Analyst Certification is a beneficial certification for security professionals. It is very much in demand at present in the industry. This program is developed by Threat Intelligence experts from all over the world to ensure that the candidate is exposed to the latest advances in the field of Threat Intelligence. This certification course covers all the stages involved in the Threat Intelligence lifecycle. This Certification will help you to gain in-depth knowledge and skill in planning a threat intelligence project, performing threat data collection from various sources, and feeds, performing bulk data collection, and data normalization.
How to get CTIA certification?
Infosec Train is one of the leading IT security training providers. We offer a comprehensive training program for Certified Threat Intelligence Analyst (CTIA) certification. If you want to take the expert’s help in getting through the CTIA certification exam, check this CTIA certification training course offered by Infosec Train:






 1800-843-7890 (India)
1800-843-7890 (India)