ISACA CRISC Domain 2: IT Risk Assessment
As businesses adapt to the digital age, banks are far from the only areas where cybercrime has taken hold. Businesses are like the Golden Goose, vulnerable to hackers and fraud because they own a substantial amount of data and information. With the increasing threats to the organization, the risk team requires experts who can protect them from the dreaded elements. CRISC is one of the most well-known certifications that confirms your ability to avoid security breaches. Because CRISC holders are in high demand all around the world, this confirmation provides you a specialty in your field with higher pay.

CRISC: The CRISC (Certified in Risk and Information Systems Control) certificate from ISACA (Information Systems Audit and Control Association) certifies experience in assessing and managing enterprise IT risk and implementing information systems controls. Risk management is a key topic for every company, hence a Risk Management specialist is always in demand. CRISC certification validates your knowledge and abilities in risk management in the workplace. It will also help you cope with any risks that your company may encounter. CRISC will help you earn reputation and recognition if you want to develop in your job.
Domains of CRISC
CRISC comprises the following four domains, which basically explains the entire Risk Management Life Cycle:
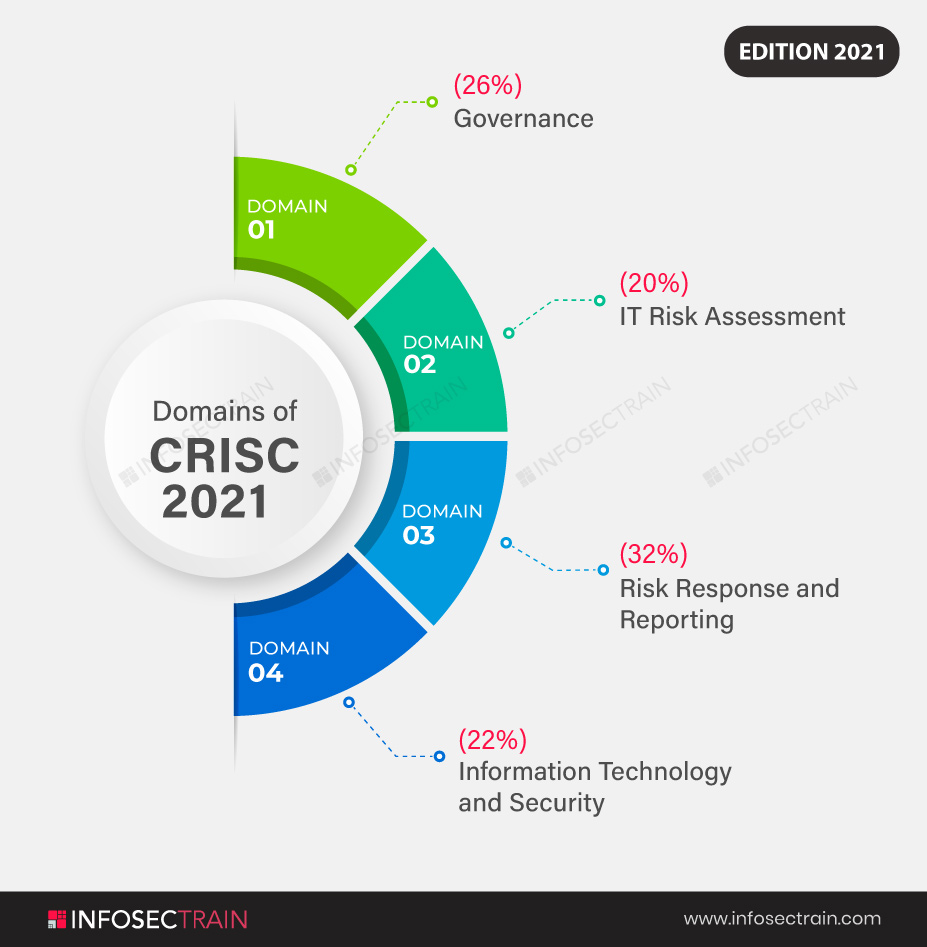
- Domain 1: Governance (26%)
- Domain 2: IT Risk Assessment (20%)
- Domain 3: Risk Response and Reporting (32%)
- Domain 4: Information Technology and Security(22%)
We are going to explain the second domain that is ‘IT Risk Assessment’.
Domain 2: IT Risk Assessment
The domain IT Risk Assessment holds a fair amount of weightage in the exam that is 20%. Although its the least weightage compared to the other domains, it still holds a major share in the certification. It is bifurcated into IT Risk Identification and IT Risk Analysis and Evaluation. It incorporates the following subject matters:
IT Risk Identification
- Risk Events
- Threat Modelling and Threat Landscape
- Vulnerability and Control Deficiency Analysis
- Risk Scenario Development
IT Risk Analysis and Evaluation
- Risk Assessment Concepts, Standards, and Frameworks
- Risk Register
- Risk Analysis Methodologies
- Business Impact Analysis
- Inherent and Residual Risk
The domain IT Risk Assessment, as the name implies, examines how to identify possible or present risks, threats, and vulnerabilities. It also focuses on the methods and standards for gaining access to an organization in order to assess these risks, threats, and vulnerabilities, as well as almost any other data that might aid in risk analysis. To estimate the genuine risks to which a business is exposed, we must first identify the threats and vulnerabilities. In order to establish the actual impact on the business, we must also understand the possibilities of organizations being abused and what information is truly available.
This assessment series then moves on to the development of risk scenarios in order to determine the potential impact of risks on an organization, who is a stakeholder in an event, and what the business risk tolerance is. Risk awareness efforts, which improve risk knowledge among all stakeholders, are also included in this category. Risk identification is impossible without risk scenarios. It explains in detail how risk scenarios may be developed to uncover specific flaws in a business process, an IT process, or a control system.
This domain ensures that the aspiring candidate possesses the required understanding of how to use risk identification techniques. The candidate is able to differentiate between threats and vulnerabilities. The person is able to identify relevant standards, frameworks, practices, and relevant stakeholders. It goes through the tools and procedures for developing risk scenarios. It qualifies a person to contribute to the development of a risk awareness program. It will define critical parts of a risk register as well as risk management concepts such as risk appetite and risk tolerance. The candidate must do both the qualitative and quantitative analysis of risk and hence proceed with risk ranking and risk prioritization.
Task Statements of Domain 2
A CRISC applicant must be able to do the following seven tasks within this domain:
1. Collect and analyze information, including existing documentation, about the organization’s internal and external business and IT environments in order to identify possible IT risk implications on the organization’s business objectives and operations.
2. To allow IT risk analysis, identify possible risks and vulnerabilities to the organization’s people, processes, and technology.
3. Create a thorough set of IT risk scenarios based on available data to assess the possible impact on company objectives and operations.
4. Identify important stakeholders for IT risk scenarios to aid in the establishment of responsibility.
5. Create an IT risk register to help ensure that recognized IT risk scenarios are accounted for and included in the overall risk profile.
6. Determine senior leadership’s and key stakeholders’ risk appetite and tolerance to ensure alignment with company objectives.
7. Collaborate in the establishment of a risk awareness program and provide training to ensure that stakeholders understand risk and foster a risk-aware culture.
CRISC with InfosecTrain
CRISC certification from InfosecTrain will expose you to the unique difficulties of IT and corporate risk management. Because we are a major training provider worldwide, our highly qualified trainers with knowledge in the subject build the full action plan. At InfoSecTrain, experienced specialists guide you through the process of creating a solid foundation of CRISC in order to upskill your risk management expertise to a skilled level.







 1800-843-7890 (India)
1800-843-7890 (India)