CCSP Domain 5: Cloud Security Operations
The Certified Cloud Security Professional or CCSP certification is accreditation for executives who want to specialize in cloud security. In 2015, (ISC)2 and the Cloud Security Alliance (CSA) collaborated to create it in order to meet the future demands for qualified and knowledgeable cloud security experts.

The certifications verify the professionals’ knowledge, skills, and abilities to create, implement, architect, manage, control, and enforce regulatory frameworks with the education required to maintain security in cloud environments.
The CCSP Common Body of Knowledge (CBK) covers a wide range of topics that makes it applicable to all areas of cloud security. The CCSP exam has six domains. These are:
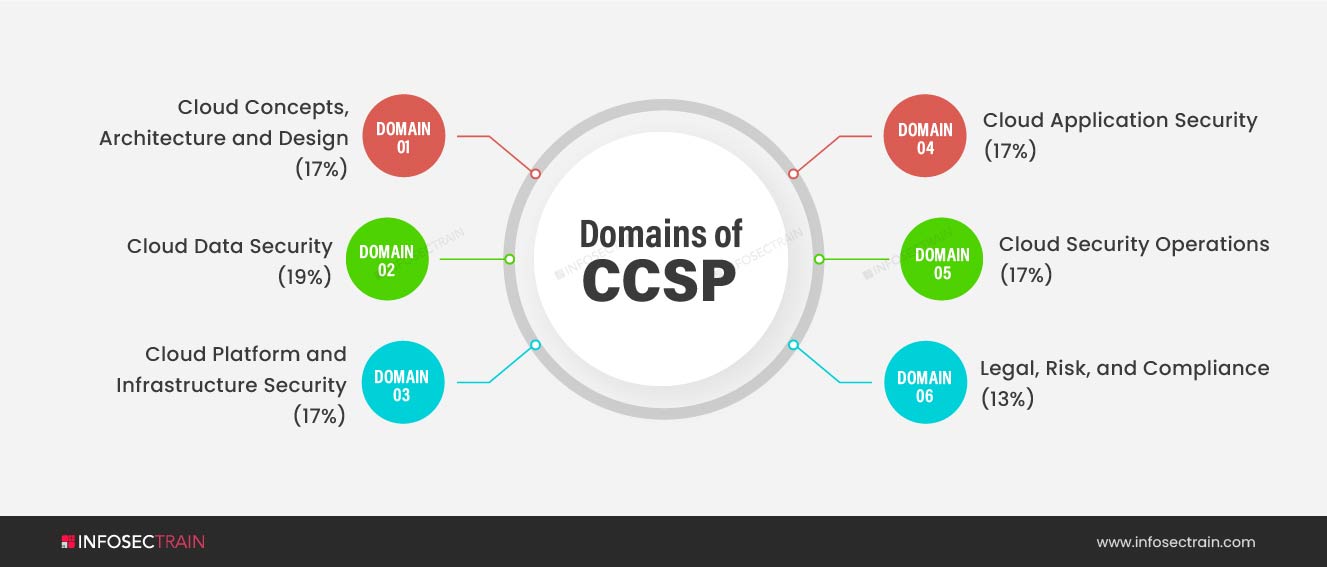
- Domain 1: Cloud Concepts, Architecture and Design (17%)
- Domain 2: Cloud Data Security (19%)
- Domain 3: Cloud Platform and Infrastructure Security (17%)
- Domain 4: Cloud Application Security (17%)
- Domain 5: Cloud Security Operations (17%)
- Domain 6: Legal, Risk, and Compliance (13%)
This article will look at CCSP Domain 5: Cloud Security Operations and what candidates should expect when they prepare for the exam.
Cloud Security Operations
The fifth domain of CCSP focuses on security operations in a cloud environment. Cloud security experts must have a thorough grasp of cloud operations, which involve a wide range of functions such as infrastructure and service design, development, deployment, management, monitoring, and auditing, all of which contribute to a secure cloud infrastructure.
The domain holds the 17% weightage and covers the following topics:
- Implement and Create Physical and Logical Infrastructure for Cloud Environments
- Operate the Physical and Logical Infrastructure for Cloud Environments
- Manage the Physical and Logical Infrastructure for Cloud Environments
- Implement Operational Controls and Standards
- Support Digital Forensics
- Manage Communication with Relevant Parties
- Manage Security Operations
You can refer to the video provided below to learn meticulously about the fifth domain of the CCSP certification exam.
The numerous subsections of the fifth domain of the CCSP certification are described below.
Implement and Build Physical and Logical Infrastructure for Cloud Environment
The domain discusses the creation and implementation of physical and logical infrastructure for cloud environments. The cloud security operations domain starts with a thorough discussion of data center planning, which includes physical and logical layers and the technologies used.
It has material on how environmental concerns and needs are met in addition to physical requirements, such as reliable and redundant cooling and electrical resources, as well as suitable protection from natural disasters and environmental challenges.
Operate Physical and Logical Infrastructure for Cloud Environment
Domain 5 delves into the operation of physical and logical infrastructure for cloud environments. Although cloud environments are mostly virtualized in the way that most think, they still have a traditional data center’s underlying physical environment and concerns, even if those burdens are handled and maintained by the cloud provider and are abstracted mainly from the users’ and cloud customers’ views and concerns.
The virtualized environment’s servers and storage and network components make up the physical layer. Firewalls, routing, and network-based intrusion protection and detection systems are all there from a network standpoint, as are all of the concerns of a traditional data center. Physical devices can also be used in a stand-alone or clustered configuration, depending on environmental considerations or requirements and expectations.
Patch management and versioning, access control, log collecting and preservation, and auditing requirements all apply to the physical environment in a cloud environment, just as they do in a traditional data center. The physical environment necessitates substantial planning and scheduling for maintenance and management activities since it directly impacts the virtualized environment.
Manage Physical and Logical Infrastructure for Cloud Environment
Domain 5 discusses the management of physical and logical infrastructure for cloud environments. For the most part, the logical environment bears the same burdens and requirements as the physical environment, but with a different focus on the cloud customer’s systems and applications, such as virtual machines and network appliances.
Patch management and versioning strategies are also required for these systems, albeit the approach varies greatly depending on the cloud model deployed. The logical environment will require robust performance monitoring as loads and demands constantly shift. The logical environment is linked to the physical environment’s performance, and how systems are dynamically balanced and resources are allocated across physical systems to maintain optimal performance. The topic of logical system backup and recovery is also explored.
Implement Operational Controls and Standards
This section of Domain 5 delves deeply into the components and concepts of Information Technology Infrastructure Library (ITIL). The ITIL is a collection of best practices for IT service management widely utilized in the IT industry. They form a holistic approach to operations management that can be applied to any system or application. There are ten primary components covered, including change management, configuration management, and information security management, all familiar to anyone who works with IT systems and services.
Support Digital Forensics
Domain 5 deals with all facets of digital forensics. Collection and preservation of electronic records for use as digital evidence is another crucial aspect of operations. These systems and programs must be a permanent element of an operating strategy, not something that is addressed only when a problem emerges. This section of Domain 5 provides an overview of these subjects from a practical perspective.
Manage Communication with Relevant Parties
Domain 5 deals with effective communication with key stakeholders, which is an integral part of operations. Vendors, customers, partners, regulators, and any other prospective stakeholders based on the specifics of the data, application, or system are all included as stakeholders at various levels of an engagement or contract. Proper and efficient communication is necessary to build and maintain healthy relationships. It may be mandated by contracts, SLAs, or regulations in terms of both frequency and amount of detail.
Manage Security Operations
Domain 5 is concerned with the management of an organization’s security operations. This includes the establishment of a security operations center to manage the organization’s technological and operational security needs. It is critical to build systems to monitor security controls and ensure that they are not changed outside official protocols and consent and perform as designed and intended. Logging data is collected and preserved in a centralized manner to enable incident correlation and monitoring.
CCSP with InfosecTrain
For information security professionals who desire to further their careers in cloud computing security, the CCSP is an excellent accreditation to get. CCSP certification training course at InfosecTrain will guide you to realize your dream. We are a globally leading IT security certification and training provider. Our highly skilled instructors will help you update your knowledge and expertise as a CCSP certified professional throughout your training course. The CCSP training course will educate you on how to thoroughly comprehend cloud security operations as well as safeguard assets developed and maintained in cloud settings.






 1800-843-7890 (India)
1800-843-7890 (India)