Domain 5 of the CEH: Web Application Hacking

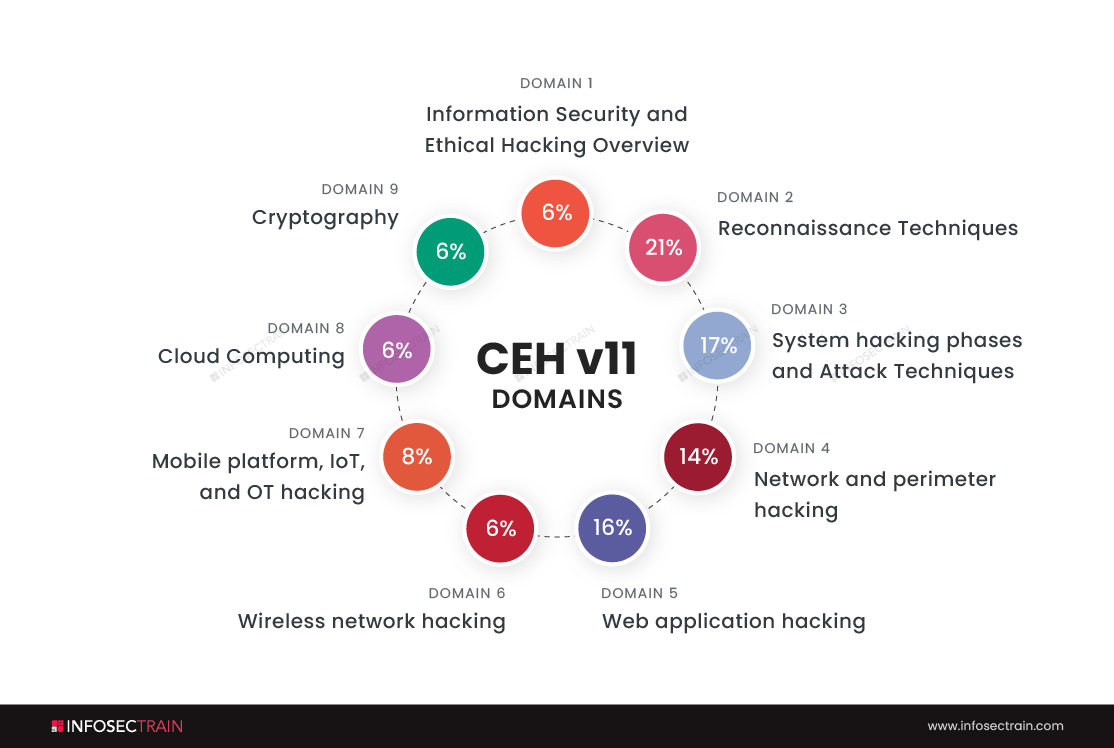
Domains of CEH
- Information Security and Ethical Hacking Overview-6%
- Reconnaissance Techniques-21%
- System hacking phases and Attack Techniques-17%
- Network and perimeter hacking-14%
- Web application hacking-16%
- Wireless network hacking-6%
- Mobile platform, IoT, and OT hacking-8%
- Cloud Computing-6%
- Cryptography-6%
We will discuss the fifth domain of CEH, which is ‘web application hacking.’
What is a Web Application?
Considering that most people have used mobile applications like PUB-G, Instagram, and WhatsApp. I will give you an example of a web application that is also a mobile app. Now assume you’ve lost your mobile or your mobile is switched off, and you are willing to scroll the insta feed. What will you do? Login to your account through Google Chrome. Right? And that’s it, as you can use your Instagram by using a web browser. It is called a web application. A few famous examples of web applications are Facebook, MakeMyTrip, Flipboard, and the 2048 Game.
The technical definition of a web application: A web application is a software or a program that performs particular tasks by running on any web browser like Google Chrome, Mozilla Firefox, Internet Explorer, etc.
One of the coolest things about using web applications is you don’t need to download them. Hence, devices will have space for more important data.
Hacking of Web Applications:
Web hacking refers to exploiting HTTP applications by manipulating graphics, altering the Uniform Resource Identifier (URI), or altering HTTP elements outside the URI.
Different methods to hack web applications are:
SQL Injection attacks: We can use Structured Query Language to operate, query, and administrate the data systems. The SQL injection attack is one of the prevalent SQL attacks that attackers use to read, change, or delete data. SQL injections can also command the operating systems to perform particular tasks.
Cross-site scripting: Attacks using cross-site scripting, also called XSS, involve injecting malicious code into websites that would otherwise be safe. Using a target web application vulnerability, an attacker can send malicious code to a user.
Fuzzing: In software, operating systems, or networks, developers can employ fuzz testing to identify code mistakes and security gaps. Attackers may also apply the same method on our sites or servers to locate weaknesses.
It works by first entering a huge amount of random data (fuzz) to crash it. Furthermore, attackers use a fuzzer software tool that is used to detect weak areas. If the security of the target fails, the attacker might exploit it further.
Types of vulnerabilities that cause web application hacking
Unvalidated Inputs: Web applications accept input from the user, as queries are built on top of that input. The attacker can launch attacks like cross-site scripting (XSS), SQL injection attacks, and directory traversal attacks if these inputs are not properly sanitized. This attack can also lead to identity theft and data theft.
Directory traversal attack: As a result of this vulnerability, the attacker can access restricted directories on the web server in addition to the webroot directory. This would allow the attacker to access system files, run OS commands, and find out details about the configuration.
Defense Mechanisms
There are various defense mechanisms to control web application hacking. Some of them are:
Authentication: Authentication is a defense mechanism that checks the user ID and password to verify the users. But with the increasing social engineering techniques, attackers can easily get your login credentials. Hence, the two-step verification came into existence.
Two-step verification is nothing but sending a “One Time Password” to your mobile so that only you can have the authority to login into your account.
Handling data safely: Most vulnerabilities in Web applications are caused by the improper processing of user data. Vulnerabilities can frequently be overlooked, not by verifying the input itself but by assuring safe processing. Secure Coding approach that prevents typical issues. For example, the proper use of parameterized database access queries can avoid attacks from SQL by injecting.
Conducting audits: Effective audit logs should enable the application’s owners to understand precisely what has happened, what vulnerability was exploited by attackers, whether attackers got unwanted data access, or whether attackers conducted any unauthorized actions. Audits can also provide the attacker’s identity.
CEH with InfosecTrain
InfosecTrain is one of the leading training providers with a pocket-friendly budget. We invite you to join us for an unforgettable journey with industry experts to gain a better understanding of the Certified Ethical Hacker course. Courses can be taken as live instructor-led sessions or as self-paced courses, allowing you to complete your training journey at your convenience.







 1800-843-7890 (India)
1800-843-7890 (India)