Role of an Ethical Hacker in Defending IoT Devices
The world is changing, and it is becoming increasingly technologically connected. This connectivity has been aided by the Internet of Things (IoT) devices. That obvious truth can sometimes bring wonderful things, such as medical breakthroughs and products that help people get more out of life. However, as technology advanced, so did cybercrime methods. One example is the hacking of IoT devices. Due to their fragile, sometimes non-existent, and disregarded security, malicious hackers are turning their attention to hacking the billions of gadgets connected to the Internet. The demand for cybersecurity professionals such as Ethical Hackers to protect IoT devices from malicious attackers has risen as a result.

Table of Contents
What is IoT hacking?
Why are IoT devices vulnerable to cyberattacks?
Role of an Ethical Hacker in defending IoT devices
Hence, in this article, we have discussed the role of Ethical Hackers in protecting IoT devices.
What is IoT hacking?
The Internet of Things (IoT) hacking is the hacking of IoT devices. IoT is a network of devices embedded with sensors, software, and other technologies to connect and exchange data and information with other devices and systems over the Internet. It primarily refers to the fast-expanding network of linked devices that use embedded sensors to collect and exchange data in real-time. Although IoT hacking is a relatively new phenomenon, it has already shown a vast capacity for destruction in a relatively short period.
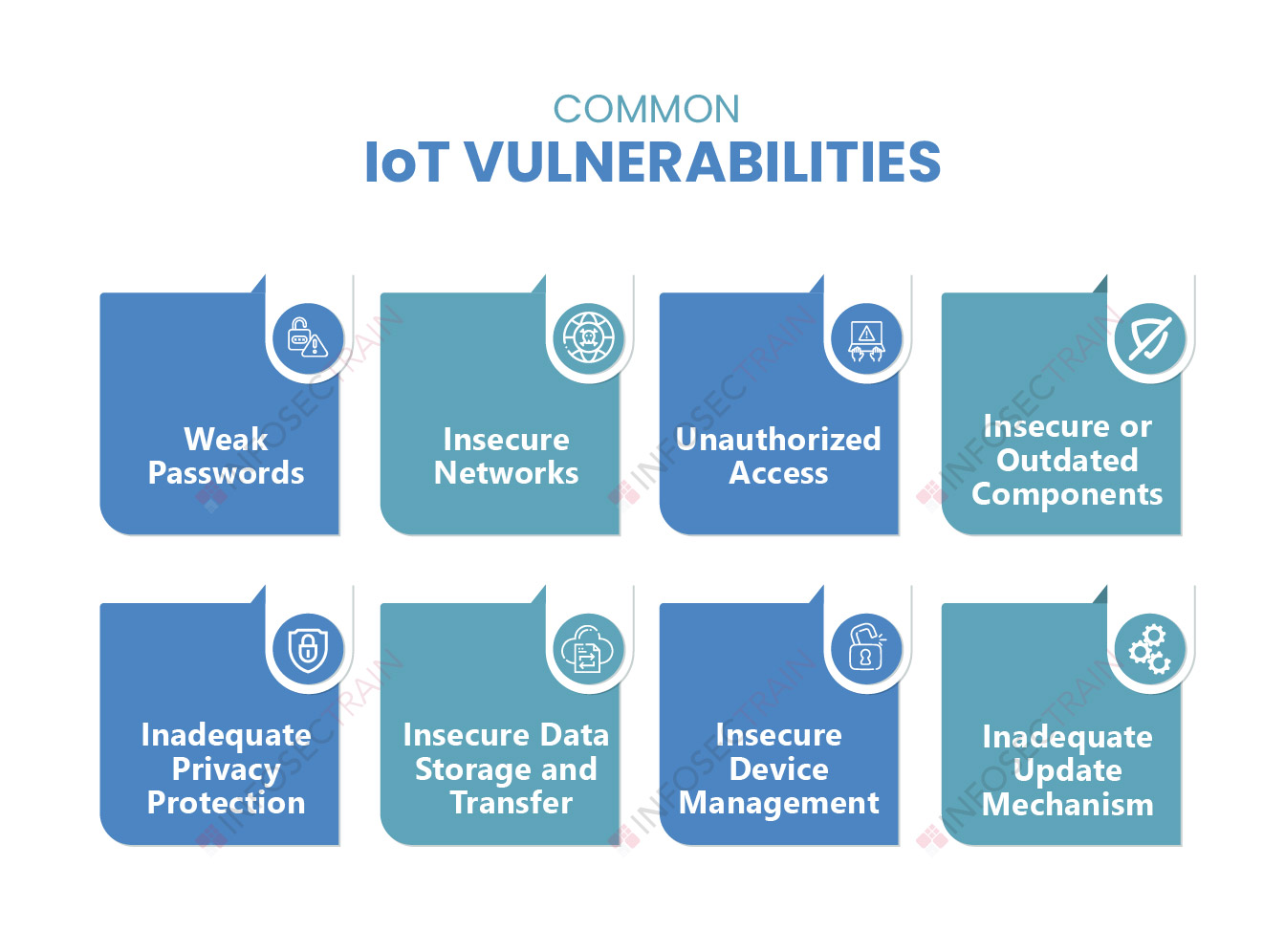
Why are IoT devices vulnerable to cyberattacks?
IoT devices are vulnerable primarily due to a lack of security controls built-in. Weak passwords, a lack of an update process or method, unsecured network services, ecosystem interfaces, unsecured data storage, transfer, and more are all weaknesses that put IoT devices in risk of being hacked. These flaws in IoT devices could allow cyber attackers to take control of them. Furthermore, hackers can use these devices to break into computers or other devices.
Role of an Ethical Hacker in defending IoT devices
Ethical Hackers are professionals who penetrate or break into an IT network to test or evaluate its security rather than with criminal or malicious intent. Ethical Hackers play a vital role in defending IoT devices. They gather information about their target IoT device, scan for weak points where they could break into a system, launch various attacks to obtain access, and then cover their traces once they have the information they need.
They perform vulnerability assessments to assess security threats. They identify security flaws in IoT devices using a variety of tools and approaches.
- Awareness of the attacker’s techniques: Malicious attackers use a variety of tactics to penetrate IoT devices, which Ethical Hackers must be aware of. Phishing attacks, brute-force attacks, social engineering attacks, ransomware attacks, DoS attacks, DDoS attacks, malware attacks, and more are some of the attacks carried out by malevolent hackers.
- Understand the threats and risks associated with IoT devices: Ethical Hackers gain knowledge of the most common vulnerabilities and risks related to IoT devices. They do threat modeling for this. Threat modeling can detect, assess, and prioritize potential IoT vulnerabilities, as well as recommend security measures to assure the IoT devices’ overall security. They rank risks according to their severity and consequences and take appropriate action.
- They perform simulated cyberattacks to uncover vulnerabilities: Ethical Hackers employ various tools and approaches to carry out a variety of tasks, including data collection on payloads, suspicious behavior, and so on. These are applications or software that aid in the exploitation of computer security or networks. They use phishing attacks, brute-force attacks, social engineering attacks, ransomware attacks, DoS attacks, DDoS attacks, malware attacks, and other simulated cyberattacks to find weaknesses in IoT devices and linked devices. They can secure the devices and infrastructure in the firm by deploying IoT hacking techniques.
- They develop strategies to improve the security posture of the IoT devices: Ethical Hackers create measures to safeguard enterprises by recognizing these threats and vulnerabilities, such as installing security measures such as firewalls, antivirus software, and password rules.
- They educate employees and other members of organizations: Ethical Hackers assist organizations in defending IoT devices from hacking by educating employees and senior executives. They teach them about the numerous vulnerabilities and risks associated with IoT devices, as well as how to defend themselves from cyberattacks and how to respond in the event of a malicious attack.
How can InfosecTrain help?
The risks presented by cybercrime will continue to rise as more devices become connected, and organizations must have procedures to safeguard against these hazards. Advanced training courses like CEH and CompTIA PenTest+ will help you understand how to defend IoT devices as cyberattacks get more complex. You can join InfosecTrain to obtain all of the necessary knowledge to pass these certification examinations under the guidance of professionals who are experts in the domain. Enroll in CEH, CompTIA PenTest+, Pentester combo training, and various other security testing training courses to learn more!






 1800-843-7890 (India)
1800-843-7890 (India)