(ISC)² ® CSSLP Domain 2: Secure Software Requirements (14%)

Domains of (ISC)² ® CSSLP
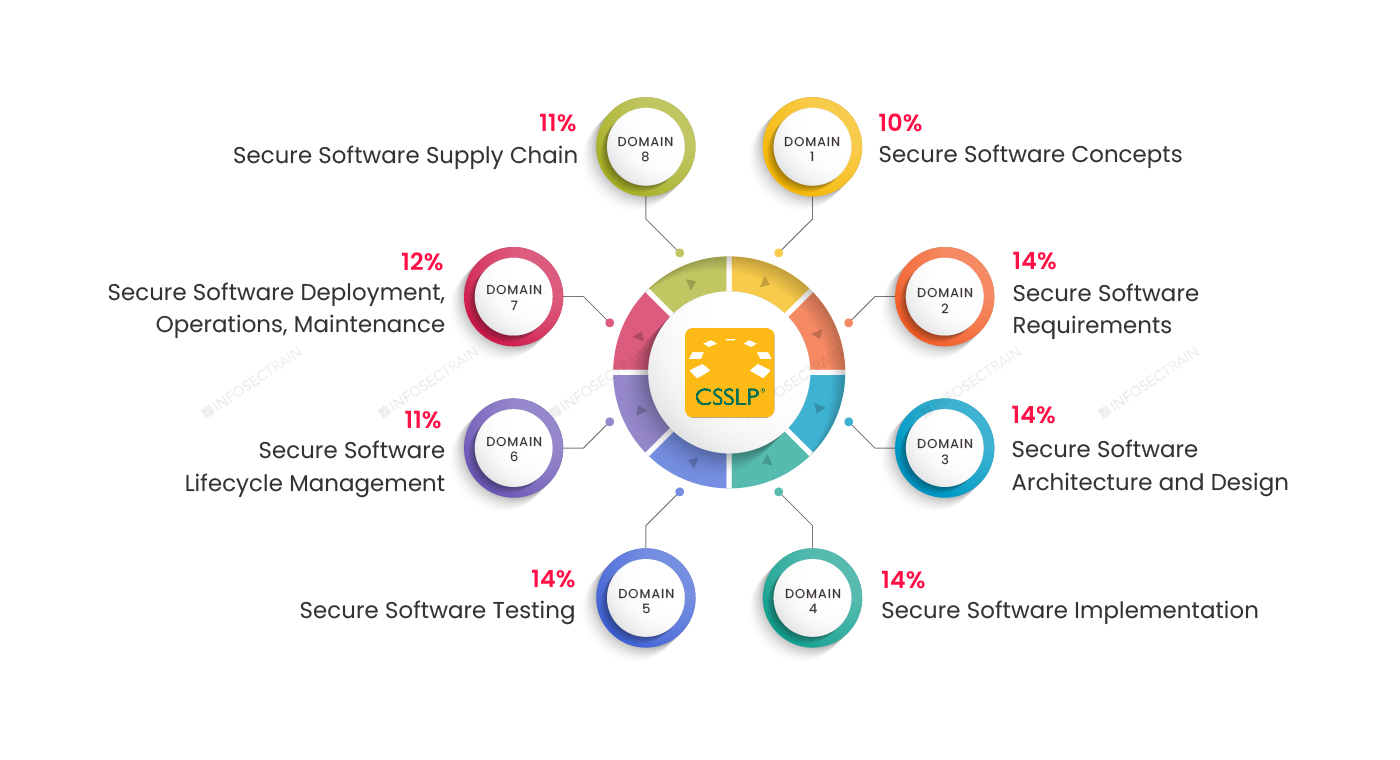
Domain 1: Secure Software Concepts (10%)
Domain 2: Secure Software Requirements (14%)
Domain 3: Secure Software Architecture and Design (14%)
Domain 4: Secure Software Implementation (14%)
Domain 5: Secure Software Testing (14%)
Domain 6: Secure Software Lifecycle Management (11%)
Domain 7: Secure Software Deployment, Operations, Maintenance (12%)
Domain 8: Secure Software Supply Chain (11%)
This article provides an overview of (ISC)² ® CSSLP Domain 2: Secure Software Requirements (14%).
Domain 2: Secure Software Requirements (14%)
Secure software requirements is the second domain of the CSSLP certification exam, which holds 14% exam weightage. In the second domain of CSSLP certification, you will learn how to determine software security requirements using internal and external sources and various security requirements for the software. It focuses on the development of secure software requirements.
Every software program has needs that specify what it should be able to perform. Software security requirements are similar to other requirements, but they are essential to ensure that software performs exactly what it intends. Professionals ensure that software adheres to all relevant regulations and is protected against possible misuse and abuse.
This second domain of the CSSLP certification exam covers the following subtopics:
- Define software security requirements
- Identify and analyze compliance requirements
- Identify and analyze data classification requirements
- Identify and analyze privacy requirements
- Develop misuse and abuse cases
- Develop security requirements traceability matrix (STRM)
- Ensure security requirements flow down to suppliers/providers
1. Define software security requirements
This subsection will discuss the software security requirements, whether functional (based on business requirements) or non-functional (operational, deployment, systematic qualities). It covers all requirements of security software.
2. Identify and analyze compliance requirements
In any business or organization, compliance refers to adhering to the standards and regulations to recognize and avoid potential red flags. This section identifies and analyzes compliance requirements such as the General Data Protection Regulation (GDPR), HIPAA, the Payment Card Industry Data Security Standard (PCI-DSS), and other defined requirements for protecting specific software data.
3. Identify and analyze data classification requirements
Any structure or organization can benefit from data classification. It aids a corporation in estimating its data’s value, determining whether it is in danger, and implementing measures to prevent risks. This section discusses data ownership (data owner, custodian), labeling, and security (sensitivity, impact). It also discusses data types such as structured and unstructured data. You will learn that each data category has various security requirements and that data classification is critical to ensure that data is safeguarded at appropriate levels.
4. Identify and analyze privacy requirements
When discussing privacy requirements that refer to regulations like GDPR, CCPA defines the data subject’s rights. This subsection introduces you to privacy requirements which means every software is designed to be able to comply with these and other privacy requirements. Here in this section, you will discover data anonymization, user consent, disposition, data retention, and cross borders.
5. Develop misuse and abuse cases
One of the primary aspects of software development is security, which means that software must run safely even in the presence of malicious people. This section addresses the software security requirements, including examining how the software can be misused and abused and the safeguards that will be put in place to avoid this.
6. Develop security requirements traceability matrix (STRM)
This section discusses the security requirements traceability matrix (STRM), which keeps track of all software security requirements and their implementation details, timeline, and resources needed. This assures that all security standards are met and that nothing is missed throughout the deployment and deployment process.
7. Ensure security requirements flow down to suppliers/providers
Software security depends on third-party partners’ security, such as suppliers, providers, and others. This section includes all security standards imposed by the supply chain or contracts to third-party vendors or suppliers.
CSSLP with InfosecTrain
It’s no longer only coding regarding software development; it also entails writing secure code to eliminate flaws. The CSSLP certification demonstrates that you have the advanced abilities necessary to design, develop, and execute security processes throughout the SDLC. InfoSec Train’s CSSLP course is spaced out and covers all eight domains of the CSSLP certification. So check out InfosecTrain for your preparation.







 1800-843-7890 (India)
1800-843-7890 (India) 
