(ISC)² ® CSSLP Domain 7: Secure Software Deployment, Operations, Maintenance (12%)

Domains of (ISC)² ® CSSLP
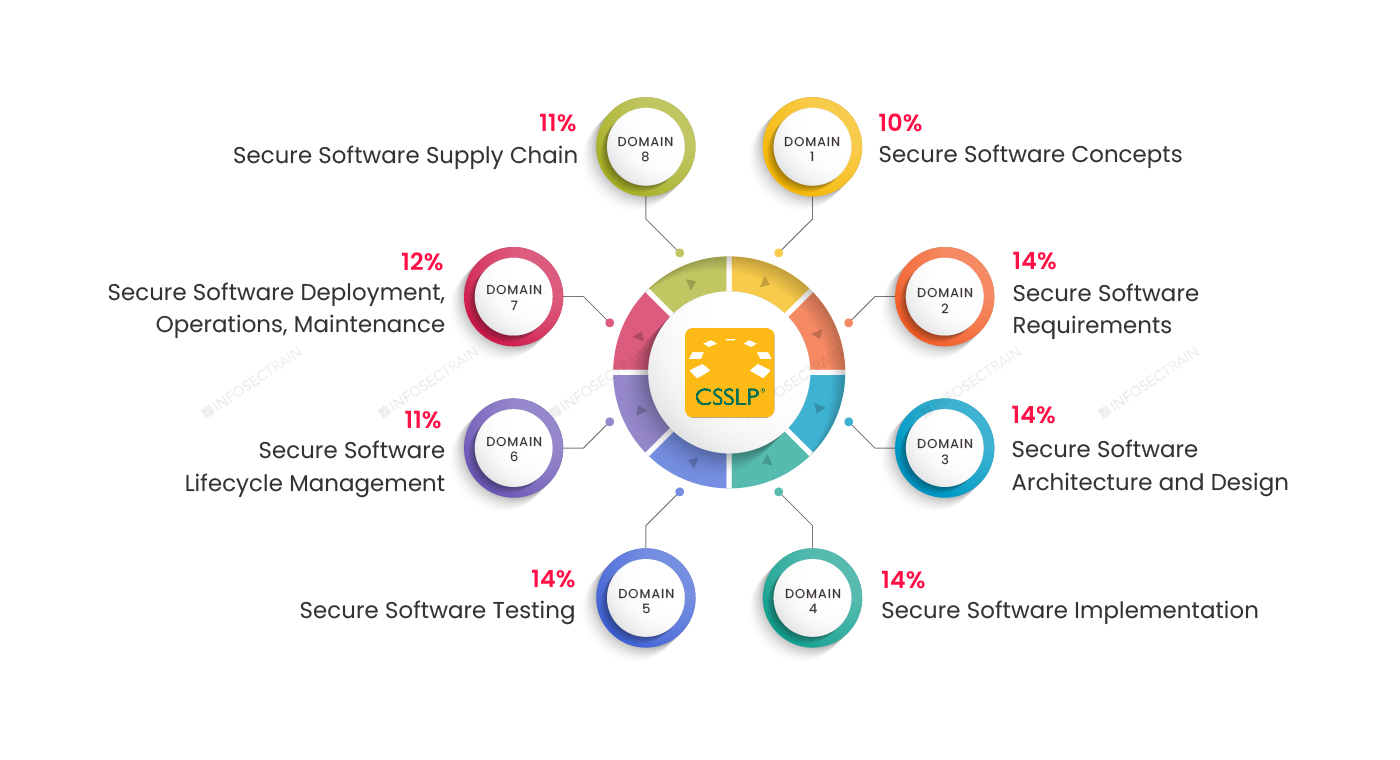
Domain 1: Secure Software Concepts (10%)
Domain 2: Secure Software Requirements (14%)
Domain 3: Secure Software Architecture and Design (14%)
Domain 4: Secure Software Implementation (14%)
Domain 5: Secure Software Testing (14%)
Domain 6: Secure Software Lifecycle Management (11%)
Domain 7: Secure Software Deployment, Operations, Maintenance (12%)
Domain 8: Secure Software Supply Chain (11%)
This article provides an overview of (ISC)² ® CSSLP Domain 7: Secure Software Deployment, Operations, Maintenance (12%).
(ISC)² ® CSSLP Domain 7: Secure Software Deployment, Operations, Maintenance (12%)
CSSLP’s seventh domain accounts for 12% of the exam weightage. This domain explores the deployment process. When an application is developed, the next step is to arrange its deployment, which requires a safe environment in which the deployment process is accomplished. This domain covers continuous integration & continuous delivery (CI/CD) pipeline, secret codes that manage the application, disaster recovery, resiliency, and information security continuous monitoring (ISCM). It explains how to do patch management (e.g., secure release, testing) and vulnerability management (e.g., scanning, tracking, triaging).
This domain is further divided into:
- Perform operational risk analysis
- Release software securely
- Securely store and manage security data
- Ensure secure installation
- Perform post-deployment security testing
- Obtain security approval to operate
- Perform information security continuous monitoring (ISCM)
- Support incident response
- Perform patch management
- Perform vulnerability management
- Runtime protection
- Support continuity of operations
- Integrate Service Level Objectives (SLO) and Service Level Agreements (SLA)
1. Perform operational risk analysis
This section of domain seven performs risk analysis in the software development process. Here you will check the deployment environment, and personal training to users or administrators will find safety criticality and safety integration.
2. Release software securely
This section describes continuous delivery and integration (CD/CI), a stage in a traditional software development process that starts with continuous integration and finishes with continuous deployment. These steps aim to make small variations to code while creating, testing continuously, and delivering more frequently, rapidly, and efficiently. It also covers secure software toolchains and builds artifact verification (e.g., code singing, checksums, hashes).
3. Securely store and manage security data
This section explores how to store and manage security data like credentials, secrets, key/certificates, and configurations.
4. Ensure secure installation
This section will understand the parameters required for secure installation during the software development lifecycle. This section explores bootstrapping (e.g., access, management, key generation), least privilege, environment hardening, security policy implementation, etc.
5. Perform post-deployment security testing
Performing post-deployment security testing is a process where software is tested after it is deployed to production. This method helps to detect errors that you were not detected before its deployment in production.
6. Obtain security approval to operate
Obtaining security approval to function during the software development process is one of the most significant processes in ensuring that the program satisfies all requirements and passes all elements of any application development.
7. Perform information security continuous monitoring (ISCM)
Performing information security continuous monitoring provides visibility into software development activities and the effectiveness of deployed security controls. This section explains how to analyze observable security data (e.g., logs, events, trace data, and telemetry), threat intel, intrusion/detection response, secure configuration, and regulation changes.
8. Support incident response
Responding to any danger in an organization is known as incident response. As a result, this part helps with incident response, including root cause investigation, incident triage, and forensics.
9. Perform patch management
The process of finding and implementing software updates is known as patch management. So this section offeres you an idea of how to manage patches.
10. Perform vulnerability management
In this part, you will manage vulnerabilities. Vulnerability management is the routine practice of finding, assessing, reporting, and correcting security flaws in the software development process. This section covers scanning, tracking, and triaging.
11. Runtime protection
This section covers Web Application Firewall (WAF), Runtime Application Self-Protection (RASP), and Address Space Layout Randomization (ASLR). Runtime protection provides personalized protection to applications.
12. Support continuity of operations
Supporting operational continuity entails continuing the software development process with the support of backup, archiving, retention, disaster recovery, and resiliency (e.g., functional redundancy, erasure code, survivability).
13. Integrate Service Level Objectives (SLO) and Service Level Agreements (SLA)
Integrating service level objectives serves as a baseline for indicators, parameters, or measurements specified with specific service level management.
CSSLP with InfosecTrain
InfoSecTrain’s CSSLP certification course is spaced out and covers all eight domains of the CSSLP certification. CSSLP training from InfoSecTrain stands out in the market, with 40 hours of specialized training by licensed and experienced trainers and access to recorded sessions.







 1800-843-7890 (India)
1800-843-7890 (India) 