CompTIA PenTest+ Domain 3: Attacks and Exploits

Domains of CompTIA PenTest+:
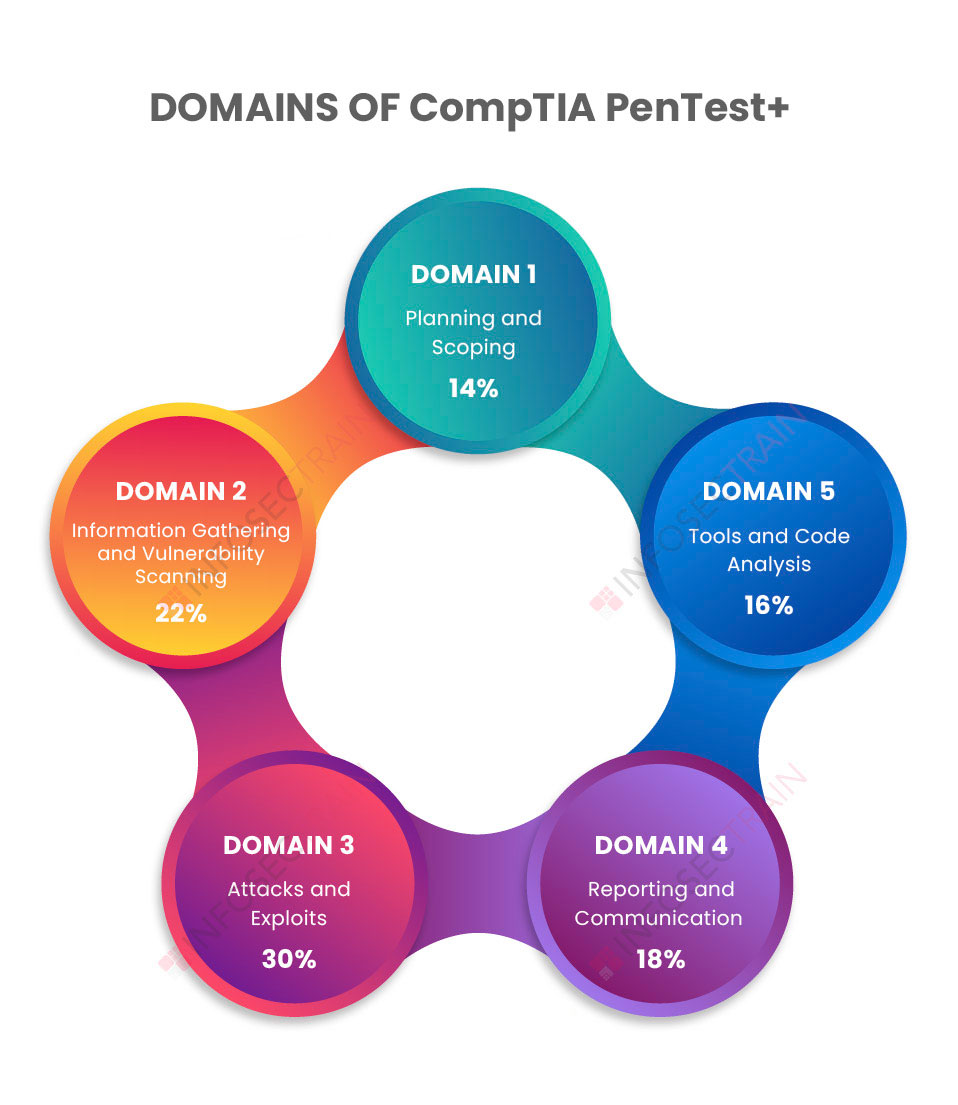
- Domain 1: Planning and Scoping (14%)
- Domain 2: Information Gathering and Vulnerability Scanning (22%)
- Domain 3: Attacks and Exploits (30%)
- Domain 4: Reporting and Communication (18%)
- Domain 5: Tools and Code Analysis (16%)
This article explores domain 3 of CompTIA PenTest+ certification, which is Attacks and Exploits.
CompTIA PenTest+ Domain 3: Attacks and Exploits
Attacks and Exploits is the largest domain of the CompTIA PenTest+ certification exam, covering a vast number of potential attack and exploitation techniques with a weightage of 30%. The domain focuses on the types of attacks and exploits that a Penetration Tester might use to acquire access to an organization’s IT environment and exploit vulnerabilities. The domain explains how to successfully attack the targeted organization’s systems, networks, and software. Social engineering attacks, exploitation of wired and wireless networks, application-based vulnerabilities, local host and physical security flaws, and post-exploitation tactics are all covered within this domain. Domain expertise can also assist in the development of efficient cybersecurity defenses.
The domain is further divided into seven subsections:
- Given a scenario, research attack vectors and perform network attacks
- Given a scenario, research attack vectors and perform wireless attacks
- Given a scenario, research attack vectors and perform application-based attacks
- Given a scenario, research attack vectors and perform attacks on cloud technologies
- Explain common attacks and vulnerabilities against specialized systems
- Given a scenario, perform a social engineering or physical attack
- Given a scenario, perform post-exploitation techniques
1. Given a scenario, research attack vectors and perform network attacks
This section looks at how a company’s network can be attacked. The company’s networks are vulnerable to potential cyber-attacks such as DDoS attacks, which can bring database servers down or restrict authorized user access to keep staff out. As a result, penetration tests on the organization’s networks are carried out in order to strengthen network security and safeguard the entire network and linked devices from future cyberattacks. Penetration Testers perform penetration testing on the systems that are available to do so. ARP poisoning, kerberoasting, exploit chaining, password attacks, DNS cache poisoning, Media Access Control (MAC) spoofing, Virtual Local Area Network (VLAN) hopping, and more are covered in this section, as well as network exploit tools like Metasploit, Netcat, and Nmap.
Some of the common network attacks carried out are:
- ARP poisoning: ARP is a protocol for mapping IP addresses to MAC addresses. In ARP poisoning, a Penetration Tester sends a malicious ARP packet to a default gateway over a LAN to modify the pairing in its IP to the MAC address table.
- Password attacks: One of the most common types of security breaches in organizations is password attacks. They are carried out by employing numerous methods to authenticate into password-protected accounts fraudulently. Password spraying, hash cracking, Brute-force attacks, and dictionary attacks are the most frequent types of password attacks.
- DNS cache poisoning: DNS cache poisoning occurs when misleading information is entered into a DNS cache, causing DNS queries to return an incorrect response and users to be led to the wrong domains.
- On-path (or man-in-the-middle): A Penetration Tester can view, manipulate, or stop traffic between two other hosts using a man-in-the-middle attack. It is typically used to steal credentials. Still, attackers can also modify or delete items from traffic to add a malicious link to a web page or remove a log entry going to a log server.
2. Given a scenario, research attack vectors and perform wireless attacks
This section looks at how wireless networks in an organization can be attacked. Because wireless networks are more easily accessible and a cybercriminal can hack from a remote location, they are more vulnerable to specific cyberattacks than wired networks. As a result, wireless network security is essential. The section delves into attack methodologies, techniques, and tools for assessing the security of wireless networks.
The domain discusses specific devices or software that can aid in wireless protocol attacks. Eavesdropping, data manipulation, data corruption, spoofing, relay attacks, deauthentication, jamming, capture handshakes, and on-path are some of the wireless attack methods mentioned.
Some of the attacks using different attack methods covered in this section are:
- Evil twin: It is meant to persuade users to join a rogue Wireless Access Point (WAP) so that wireless communications passing via that device can be eavesdropped on.
- Bluejacking: It is a type of attack that sends unwanted messages to Bluetooth-enabled devices in a specific area.
- Bluesnarfing: Bluesnarfing is a type of device attack that includes stealing data from a Bluetooth-enabled wireless device that has been set to “discoverable” mode.
3. Given a scenario, research attack vectors and perform application-based attacks
In a business, applications are frequently available over many networks or connected to the cloud, which increases their vulnerability to security risks and breaches. Therefore attackers can quickly gain access to organizations through web applications and APIs. This section discusses the OWASP top 10 vulnerabilities: Broken access control, cryptographic failures, injection, insecure design, security misconfiguration, vulnerable and outdated components, identification and authentication failures, software and data integrity failures, security logging and monitoring failures, and server-side request forgery. It also covers application vulnerabilities that are not listed in OWASP’s top 10. The section familiarizes Penetration Testers with the web application attacking tools like web proxies, SQLmap, and DirBuster, as well as common attacking resources such as word lists used in password attacks.
4. Given a scenario, research attack vectors and perform attacks on cloud technologies
Businesses have had significant success as a result of the rapid advancement and adoption of cloud technologies; yet, these systems are prone to a variety of security threats and vulnerabilities. A Penetration Tester conducts attacks on cloud technologies and uses tools to investigate various attack vectors in order to find security flaws. Credential harvesting, privilege escalation, account takeover, metadata service attack, misconfigured cloud assets, cloud malware injection attacks, denial-of-service attacks, side-channel attacks, and resource depletion are some of the frequent attacks on cloud technologies described in this section.
5. Explain common attacks and vulnerabilities against specialized systems
This section covers the vulnerabilities and exploits that a Penetration Tester might come across in an organization against specialized systems such as mobile devices, IoT devices, data storage devices, Intelligent Platform Management Interface (IPMI), virtual environments, containerized workloads, SCADA, IIoT, and ICS.
6. Given a scenario, perform a social engineering or physical attack
Cybercriminals frequently use social engineering to install malware or steal sensitive and confidential information. It is achieved through human interaction, which is the process of persuading someone to do something they would not typically do. The motive of a Penetration Tester is to get access to a system without being authorized. It can be accomplished in various ways. As a result, this domain will encompass performing social engineering attacks such as phishing, vishing, Universal Serial Bus (USB) drop key, watering hole attacks using various methods, as well as physical attacks such as tailgating, dumpster diving, shoulder surfing, and badge cloning using multiple techniques. It will also cover the tools used for social engineering attacks. This test is commonly used to investigate flaws in business processes or regulations, as well as their implications for corporate security.
7. Given a scenario, perform post-exploitation techniques
After a successful exploit, this section covers how a Penetration Tester can use their access to execute lateral movement or more discovery and enumeration. Empire, Mimikatz, and BloodHound are among the post-exploitation tools covered by the domain. It explains lateral movement techniques, such as passing the hash and examines methods for determining whether a target network is appropriately segmented to avoid lateral movement. It covers Trojans, Backdoors, Daemons, and Scheduled Tasks, as well as other ways for gaining a footing or maintaining persistence on a compromised system. It also explains how to enumerate users, groups, forests, sensitive data, and files that are not encrypted. It also covers living-off-the-land tactics/fileless malware, covering tracks, establishing a covert channel, steganography, and other techniques to evade discovery.
CompTIA PenTest+ with InfosecTrain
Testing the effectiveness of your organization’s security posture or identifying unintentional vulnerabilities allows a business to address issues before they become serious. The CompTIA PenTest+ certification trains you to conduct potential cyberattacks on any system of an organization that a Penetration Tester might come across to discover vulnerabilities. Enroll now in InfosecTrain’s CompTIA PenTest+ certification training course to learn all the techniques and tools required to perform attacks on an organization’s systems, networks, and softwares.






 1800-843-7890 (India)
1800-843-7890 (India)