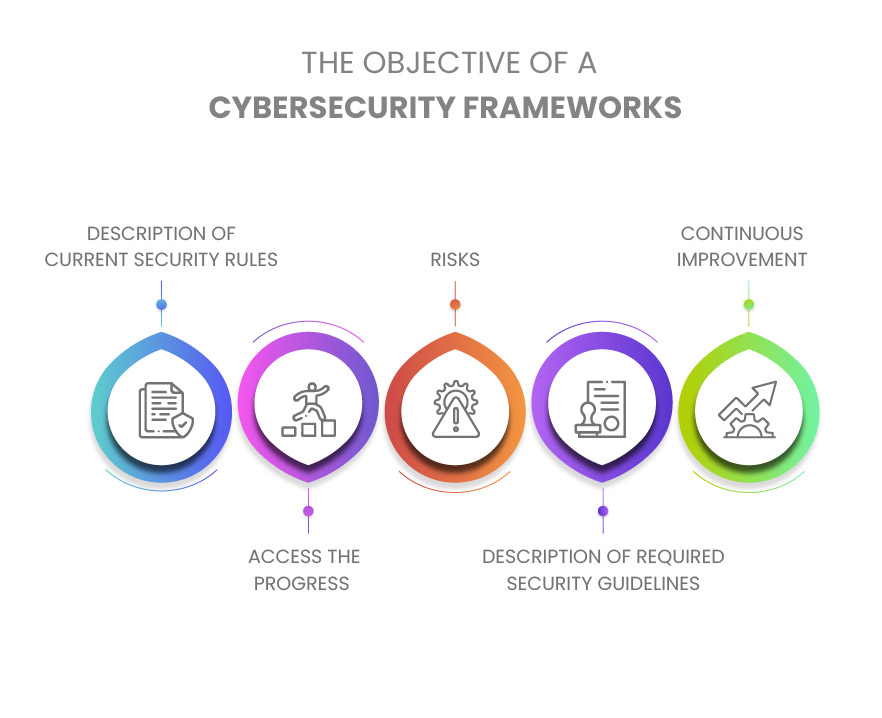
Introduction to Cybersecurity Framework
In this digital world, enterprises must protect their systems and implement frameworks that limit the risk of cyberattacks. An organization’s data is a valuable asset that must be secured from loss and damage, and here is where cybersecurity frameworks come into the scenario.

What is Cybersecurity Framework?
Cybersecurity frameworks are collections of documentation that describe principles, rules, and best practices for managing cybersecurity risks. The frameworks exist to decrease an organization’s exposure to threats and vulnerabilities that attackers and other cyber criminals may leverage. The cybersecurity framework is a structure that gives foundations, direction, and support to an organization’s security techniques and initiatives.
Components of Cybersecurity Framework
Every cybersecurity framework contains three main components, which are as follows:
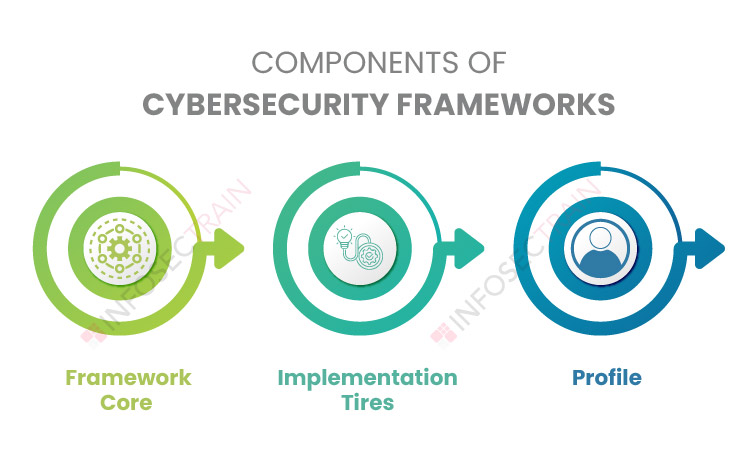
1. Framework Core: It is a collection of necessary methods and their effects on overall cybersecurity. It provides a layout of the required cybersecurity exercises and outcomes in simple language. The core assists organizations in monitoring and mitigating general cybersecurity risks in a way that complements an organization’s existing cybersecurity and risk management processes.
2. Implementation Tiers: It entails putting policies and standards into action. This component includes everything from the objective to the expense of the endeavor. It enables organizations to establish a framework for how they view cybersecurity risk management.
3. Profile: Profiles are simply records that are relevant to the organization and contain a list of cybersecurity goals, requirements, and resources.
Types of Cybersecurity Frameworks
Cybersecurity frameworks are classified into three types based on the function required.
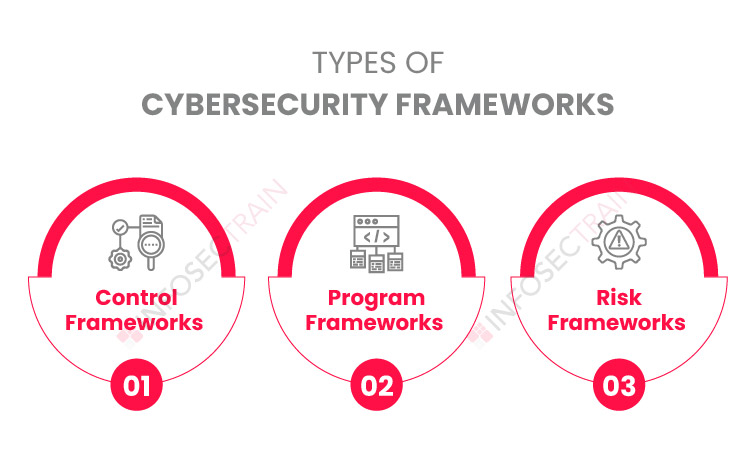
1.Control Frameworks
- Establishes a fundamental plan for the organization’s cybersecurity unit
- Provides a foundational set of security measures
- Evaluates the current level of infrastructure and technology
- Prioritize implementations of security control
2. Program Frameworks
- Analyzes the program’s security and competitiveness
- Facilitates and improves communication between the cybersecurity team and executives/managers
- Creates a comprehensive cybersecurity program
- Evaluates the present status of the organization’s security program
3. Risk frameworks
- Describes the procedures needed for risk assessment and management
- Develops a security scheme for risk management
- Puts the suitable security measures and activities first
- Identifies, evaluates, and assesses the security risks to the organization
Function of a Cybersecurity Framework
The functions have received the most thought and consideration in the cybersecurity framework. They serve as the framework core’s base, upon which all other components are built. The cybersecurity framework includes the following five functions:
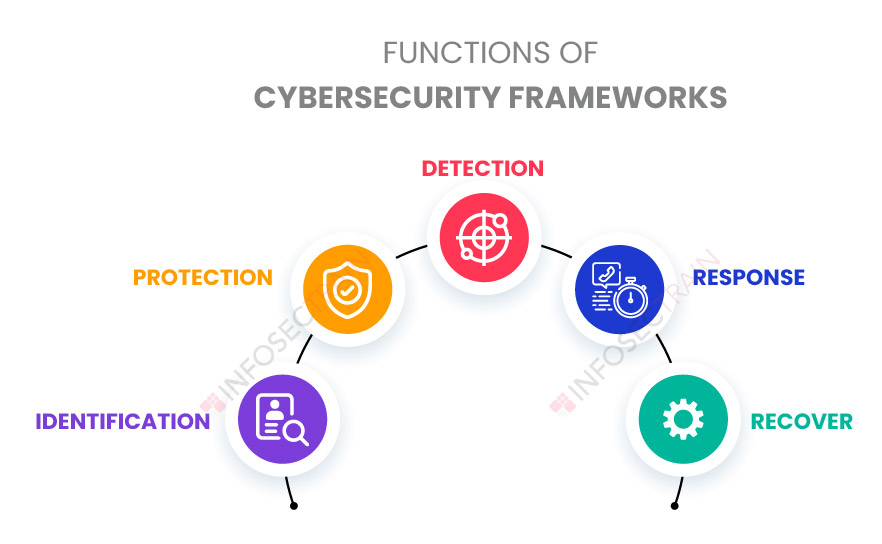
1.Identification: It entails the fundamental task of determining what needs to be protected and why. To determine the security concerns, this includes gathering system-specific data. An organization must have a thorough understanding of these settings and be able to see any potential weak points to manage the security threats to its assets, data, capabilities, and systems.
2. Protection: This function includes the essential recommendations required to protect the system based on the identified threats. Organizations must develop and implement adequate controls to mitigate or restrict the impact of potential cybersecurity incidents and threats.
3. Detection: It is a critical function since it assists in identifying a cybersecurity vulnerability before a significant loss happens. Organizations should initiate the measures required to detect cybersecurity issues as soon as possible.
4. Response: After identifying the threats and risks, the next stage is to respond appropriately. This stage involves providing information as needed. Organizations must be able to create proper response strategies to mitigate the effects of any cybersecurity incidents.
5.Recover: It entails compensating for earlier cyber risks and attacks. Organizations must design and implement effective methods for restoring any capabilities and services that cybersecurity threats have harmed.
Top Cybersecurity Frameworks
When it comes to choosing a cybersecurity framework, there are a lot of options. Here are some frameworks that are now regarded as some of the best. Naturally, the choice is determined by the security requirements of any organization. Some organizations are expected to use particular information security frameworks to adhere to industry or governmental laws; for example, an organization must comply with the Payment Card Industry Data Security Standards (PCI-DSS) framework if it accepts credit card payments. In this case, the organization must complete an audit demonstrating that they adhere to PCI-DSS framework criteria. So the following are some of the top cybersecurity frameworks:
- The NIST Framework : The NIST framework allows the public and private sectors to address cyber risks jointly. It was developed in response to Presidential Executive Order 13636 during the Obama Administration.
- The Center for Internet Security Critical Security Controls (CIS) : CIS uses standards based on shared norms such as NIST to map security standards and provide alternative options for enterprises not subject to legal security rules but seeking to improve cybersecurity.
- The International Standards Organization (ISO) Framework : This framework is also known as ISO 27k and is regarded as the globally accepted cybersecurity assessment standard for use internally and with other organizations. The framework suggests 4 types with 99 different controls. As a result, given the effort required to maintain the standards, ISO 27k might not suit everyone. It is worthwhile, though, if adopting ISO 27K is a selling point for attracting new clients.
- Health Insurance Portability and Accountability Act (HIPAA) : It was created specifically for healthcare organizations. Healthcare organizations are given rules and regulations by the Health Insurance Portability and Accountability Act (HIPAA) to support the protection of client data, specifically Protected Health Information (PHI).
Cybersecurity with InfosecTrain
A career in cybersecurity is rewarding, and experts with certification can obtain any job and pay they desire. First and foremost, selecting the appropriate qualification for one’s job description and assembling resources to achieve the goal is critical.
You can enroll in one of InfosecTain’s cybersecurity training courses that will provide a structured curriculum and expert guidance. These courses will enable learners to grasp and comprehend the intricacies of cybersecurity frameworks, equipping them with the necessary knowledge and skills for effective implementation.






 1800-843-7890 (India)
1800-843-7890 (India)