Cyber Attack vs. Data Breach
Cyber attacks and data breaches are constantly surging due to our increasing dependence on technology and the widespread use of interconnected devices. This expanding landscape creates numerous opportunities for cybercriminals to exploit vulnerabilities and compromise sensitive information. Regrettably, many companies or individuals fail to implement sufficient security measures, leaving their systems vulnerable to compromise and increasing the likelihood of cyber attacks and data breaches. In this article, we will talk about cyberattacks, data breaches, and the differences between the two.
Table of Contents
What is a Cyber Attack?
What is a Data Breach?
Difference between a Cyber Attack and a Data Breach
What is a Cyber Attack?
A cyber attack is an intended and malicious attempt to compromise the security, integrity, or availability of a system, network, or data by an external or internal threat actor or hacker. It can take various types and have diverse objectives, such as stealing sensitive information, financial gain, disrupting operations, spreading malware, revenge, espionage, or reputational damage. It poses severe risks to businesses, the nation, and individuals, requiring a strong cybersecurity strategy to prevent, discover, and address them.
What is a Data Breach?
A data breach is a cyber incident in which an unauthorized person gains access to or steals sensitive data stored, processed, or transmitted by a system or network. The data may consist of Personally Identifiable Information (PII), financial data, medical records, or other private details. Numerous factors, such as a cyber attack, configuration error, human error, or physical theft, can cause it. It can have adverse effects on individuals and organizations, such as identity theft, financial losses, reputational damage, legal liabilities, or regulatory fines.
Difference between a Cyber Attack and a Data Breach:
Cyber attack and data breach are two different terms in the realm of cybersecurity; they refer to different types of security incidents, and understanding them is crucial for anyone to protect sensitive information.
Here are the differences between a cyber attack and a data breach:
1. Objective: The primary objective of a cyber attack is to compromise the target system or network to steal data, cause damage, or disrupt operations. In contrast, a data breach’s objective is to gain unauthorized access to valuable and confidential data or information stored in an IT system or network for theft, extortion, espionage, or other malicious activities.
2. Target: Cyber attacks can target any system, network, or device connected to the internet, including servers, computers, and mobile devices. On the other hand, data breaches generally target specific businesses or organizations that hold sensitive data or information.
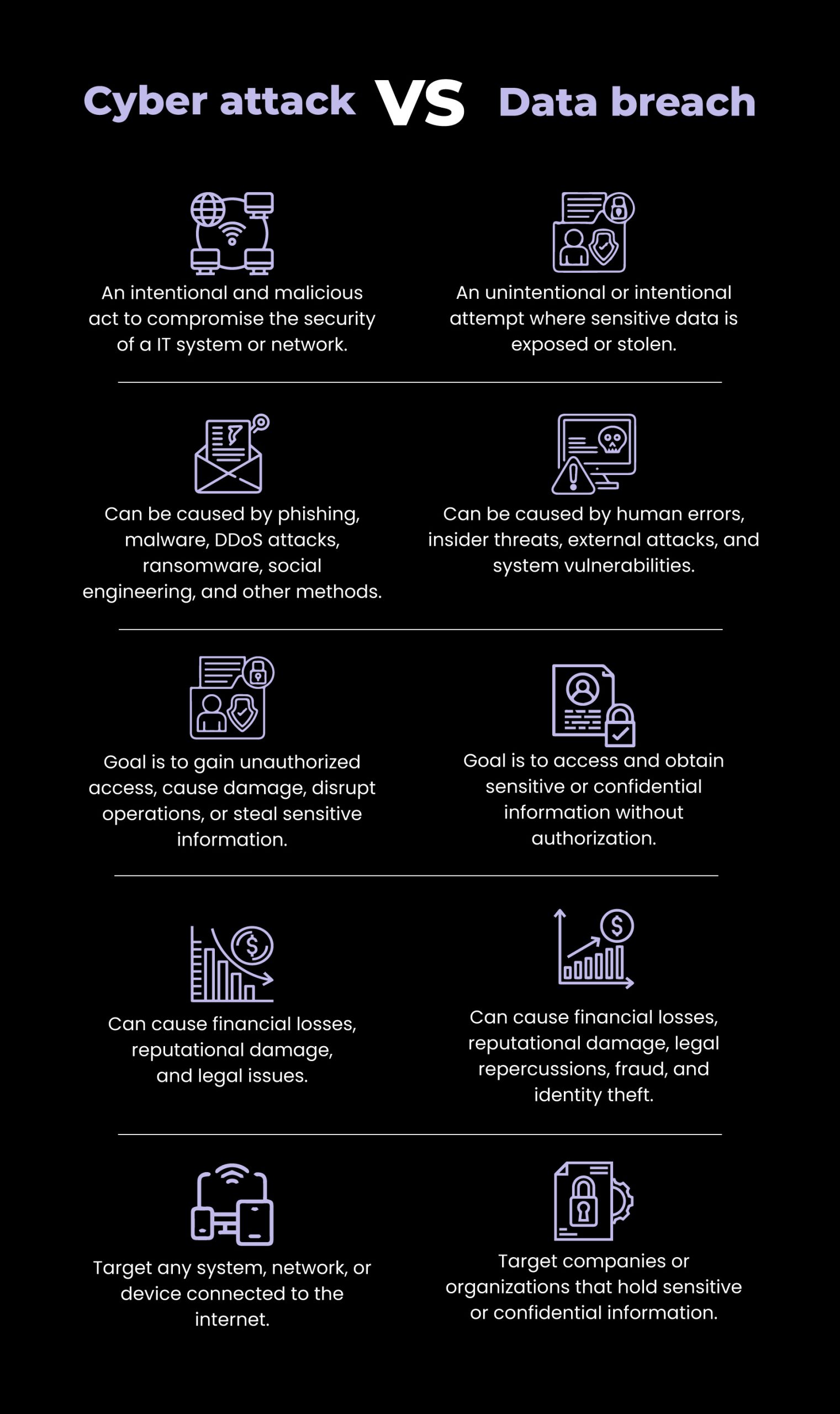
3. Methods: Cyber attacks can come in different forms, including malware, ransomware, phishing emails, DDoS attacks, social engineering, botnets, exploit kits, and SQL injection attacks. In contrast, data breaches are often caused by human error, insider threats, external attacks, misconfiguration, and system vulnerabilities, such as failing to encrypt data adequately or exposing critical information. Attackers may use various tools to carry out a data breach, including malware, phishing emails, brute-force attacks, or social engineering tactics.
4. Impact: A successful cyber attack can have significant consequences, including financial losses, reputational damage, and legal repercussions. It can cause damage to the target system, disrupt operations, and compromise sensitive information. Data breaches can also have severe consequences, including losing sensitive information, identity theft, and damaging an organization’s reputation. It can expose sensitive data to unauthorized individuals, leading to potential legal and financial consequences.
5. Timing: A cyber attack can occur anytime, even if it does not result in a data breach. In contrast, a data breach occurs only after a successful cyber attack.
6. Detection: Cyber attacks can be detected using various methods, such as intrusion detection systems, log analysis, network traffic analysis, and anomaly detection. Data breaches can be detected through monitoring tools, intrusion detection systems, penetration testing, vulnerability scanning, or user reporting.
7. Prevention: Preventing cyber-attacks requires proactive measures such as firewalls, intrusion detection systems, antivirus software, and regular software updates. In contrast, preventing data breaches requires a focus on data protection and encryption, regular data backups, access control, employee training, and incident response planning.
Conclusion:
Cyber-attacks and data breaches are two different incidents with different objectives, impacts, and detection methods that require different approaches for prevention and response. Both incidents can result in substantial harm to an organization. Therefore, it is crucial to comprehend their distinctions to safeguard against them. We hope that now the distinctions between the two are clearer to you.
Check out related blogs:
- How to Respond to a Data Breach?
- How to Protect Organizations from Cyberattacks?
- Top 5 Ways To Defeat Cyberattacks
- Career Path For Cybersecurity
- Gaps and cyber attacks, how can we defend ourselves?
How can InfosecTrain help?
To safeguard against cyber attacks and data breaches, organizations and individuals can implement security measures such as strong passwords, encryption, firewalls, and security awareness training. InfosecTrain conducts various information security certification training courses. We provide various cybersecurity, data security, and data privacy training courses by certified and experienced experts who can help you develop your skills and pave the route to becoming a security professional. Check it out, sign up, get certified, and become a competent security professional.






 1800-843-7890 (India)
1800-843-7890 (India)