Black Box vs. White Box vs. Grey Box Penetration Testing
With the rising prevalence of cybercrime, there is a growing need for penetration testing in organizations. This legitimate form of cyberattack allows organizations to proactively assess their network and system security, helping them avoid financial losses, comply with security laws, and address vulnerabilities in both their on-site and remote IT infrastructures. It is conducted more often in organizations with massive IT infrastructures that process vast business assets and financial data. The most common testing offered by information security vendors is black-box, white-box, and grey-box penetration testing. The level of access and knowledge provided to the Penetration Tester at the beginning of the project is used to categorize these penetration testing assignments.
Table of Contents
Black Box Penetration Testing
White Box Penetration Testing
Grey Box Penetration Testing
Difference Between a Black-Box, White-Box, or Grey-Box Penetration Testing
This article will help you determine the differences between black-box, white-box, and grey-box penetration testing.
Black Box Penetration Testing
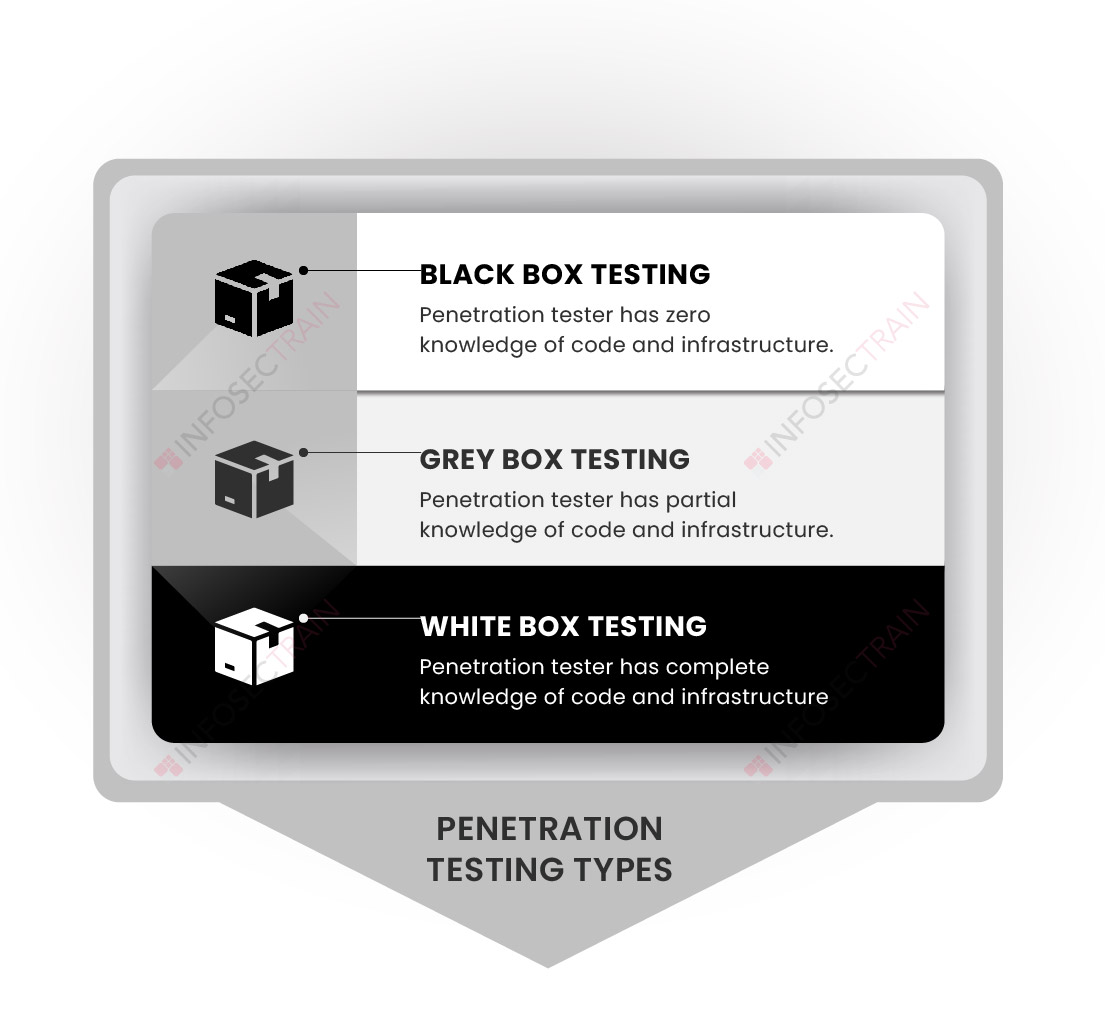
Black box penetration testing, also known as external penetration testing, is an approach where the Penetration Tester operates with no prior knowledge of the organization’s internal code, application structure, or architecture and is not granted access to the networks or applications. Throughout all stages of access, execution, and exploitation, they adopt the perspective of an unprivileged attacker. The main objective of this testing is to help businesses identify vulnerabilities that could be exploited by external threats. To accomplish this, the tester starts with reconnaissance, gathering the sensitive information necessary to progress. Proficiency in manual penetration testing techniques and automated scanning technologies is crucial for the tester to effectively uncover potential weaknesses and security gaps.
White Box Penetration Testing
White box penetration testing is also called internal, crystal box, or structural testing. In white box penetration testing, the Penetration Tester has complete knowledge of the target system. Also, they have access to the system, network, and applications, including source code, IP address schema, network maps, credentials, and more. They assist organizations in evaluating the resilience of the systems, networks, or applications against both privileged insiders and outsiders. It is the most time-consuming penetration testing because it sorts the enormous amount of data available to find possible sources of vulnerabilities. In this testing, the tester searches for significant vulnerabilities in various areas, including logical errors, security exposures, poor source code, and a lack of protective measures. It offers an in-depth analysis of both internal and external vulnerabilities. The testers can perform static code analysis, so they must be familiar with source code analyzers, debuggers, and related tools.
Grey Box Penetration Testing
Grey box penetration testing is also known as translucent box testing. It is a combination of black-box and white-box penetration testing. In grey box penetration testing, the Penetration Tester has access to or has partial knowledge of the systems, networks, and applications being tested, such as login information, system source code, architectural designs, and network infrastructure maps. They can simulate insider threats or external attacks that breach the network. By assessing privileged user access and potential harm, these tests expedite the reconnaissance phase. This approach lets consultants concentrate on uncovering high-risk system vulnerabilities instead of spending time on their discovery.
Difference Between a Black-Box, White-Box, or Grey-Box Penetration Testing
| Black Box Penetration Testing | White Box Penetration Testing | Grey Box Penetration Testing |
| It is conducted with zero knowledge of the target system. | It is conducted with full knowledge of the target system. | It is conducted with partial knowledge of the target system. |
| It is also known as closed-box testing. | It is also known as clear-box testing. | It is also known as translucent testing. |
| It only examines the open environment—no need to know the internal design of the code. | It is a comprehensive testing of all assets, including code, internal and external. | It tests both open vulnerabilities in external systems and closed vulnerabilities in internal systems. |
| It is performed by end-users, testers, and developers | It is performed by testers and developers. | It is mostly performed by professional testers and security consultants. |
| It takes unpredictable time to complete the testing. | It takes several months to finish the testing. | It takes a predetermined duration to finish the testing. |
| It is not necessary to be familiar with programming languages. | It is necessary to have an understanding of programming languages. | It requires some basic knowledge of programming languages. |
| It provides a lower number of vulnerabilities. | It provides the highest number of vulnerabilities. | It provides a considerable number of practical vulnerabilities. |
| It is most realistic. | It is more comprehensive, faster, and likely to find every vulnerability in a system or environment. | It is more effective and takes less time to enumerate and fuzz. |
| It is cost-effective. | It incurs substantial time and cost expenses, making it costly. | It falls in the middle range of cost. |
Conclusion:
Each of the three penetration testing techniques has some benefits and drawbacks. You can select one of the testing approaches depending on your needs and skill set. You can choose black box penetration testing if you want to mimic actual hacks on the perimeter of external networks. White box penetration testing is the best choice to verify that network systems are configured appropriately, and grey box penetration testing is a good option for those seeking a balance between the thoroughness of white box penetration testing and the realism of black box penetration testing.
How can InfosecTrain help you?
Penetration testing techniques such as black, grey, and white boxes simulate how a hacker might attack a network to find and resolve vulnerabilities. To become a good Penetration Tester, you can enroll in various Security Testing training courses InfosecTrain offers. With the help of our highly skilled trainers, we provide in-depth knowledge of penetration testing and help you understand how to defend against security threats and malicious attackers. We offer various online training certification courses for penetration testing, including CEH v12, CompTIA PenTest+, CPENT, Web Application Penetration Testing, Pentester Combo, etc.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 26-Apr-2025 | 01-Jun-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Close ] | |
| 11-May-2025 | 28-Jun-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 31-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 07-Jun-2025 | 13-Jul-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 21-Jun-2025 | 27-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |







 1800-843-7890 (India)
1800-843-7890 (India)