Spear Phishing vs. Whaling
Since COVID-19, cyberattacks have increased at a faster rate than before. Cybercriminals are using different types of cyberattack techniques to gain access to organizations, which has disastrous effects such as unauthorized access, identity theft, money theft, etc., leading to a loss of reputation, depletion of customer trust, and financial losses for the organizations.

Social engineering attacks are among the most frequent kinds of cyberattacks. They occur when an attacker misleads a victim into opening an email, instant message, or text message and clicking on a malicious link that inserts malware as part of a ransomware attack or exposes sensitive data.
Table of Contents
What is Spear Phishing?
What is Whaling?
Spear Phishing vs. Whaling
This article will explore two prominent types of social engineering attacks in greater depth: spear-phishing and whaling, how these attacks are performed, how to spot such attacks, and steps that avoid being a target of such attacks, and so on.
What is Spear Phishing?
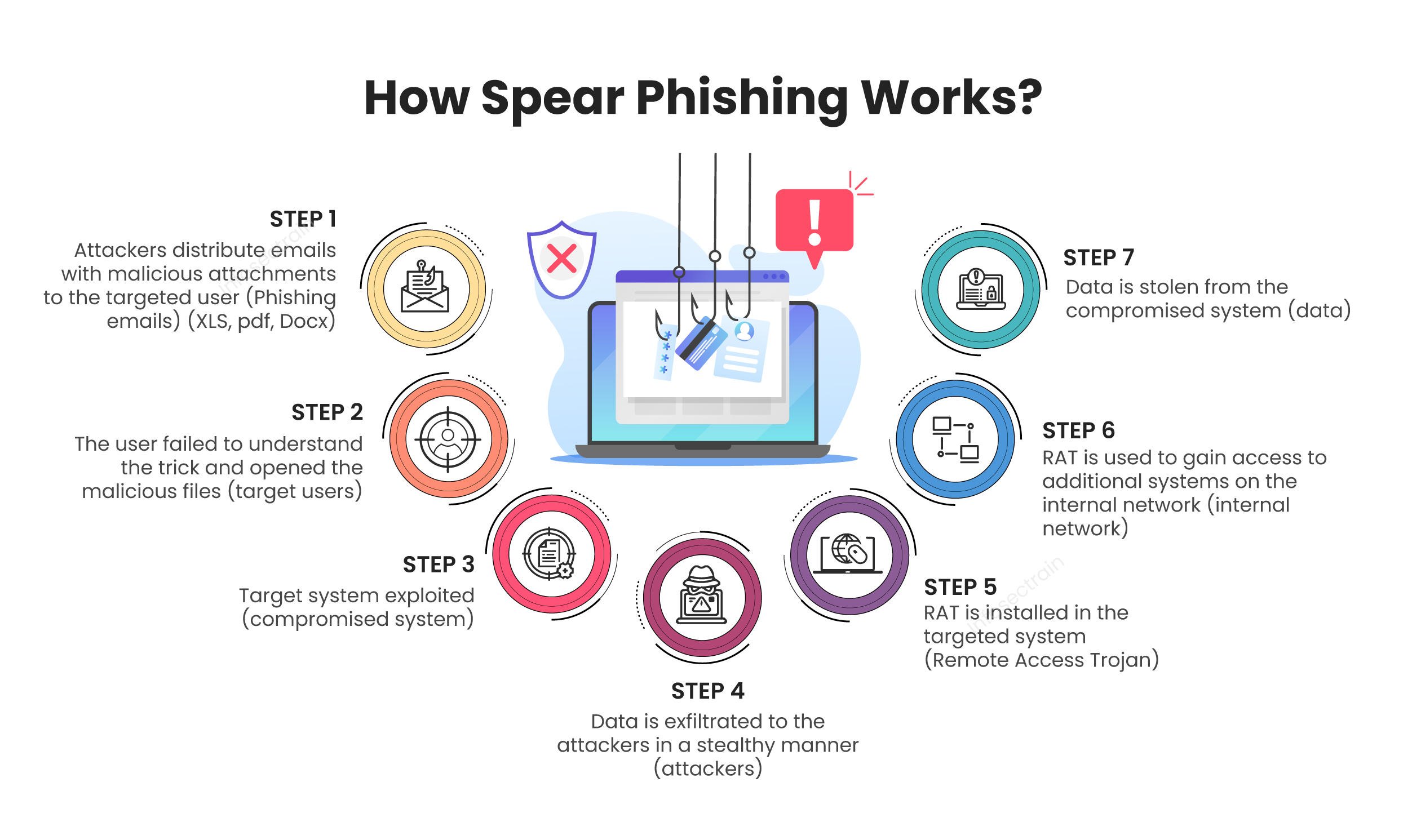
The spear phishing is a type of phishing attack that targets a specific person or organization. The attacker uses spear phishing to deceive the victim into clicking on malicious links, installing malicious programs, and allowing the attacker to retrieve all sensitive information from the target system or network.
In this type of attack, the attacker poses as a trusted individual and tricks the victim into clicking on a spoofed email or text message, which implements malicious code on the victim’s system and allows the attacker access to sensitive personal or professional information from the victim, such as names, contact numbers, mailing addresses, social security numbers, credit card numbers, and so on. The goal is to access classified information to assist future financial fraud or cybercrime.
What is Whaling?
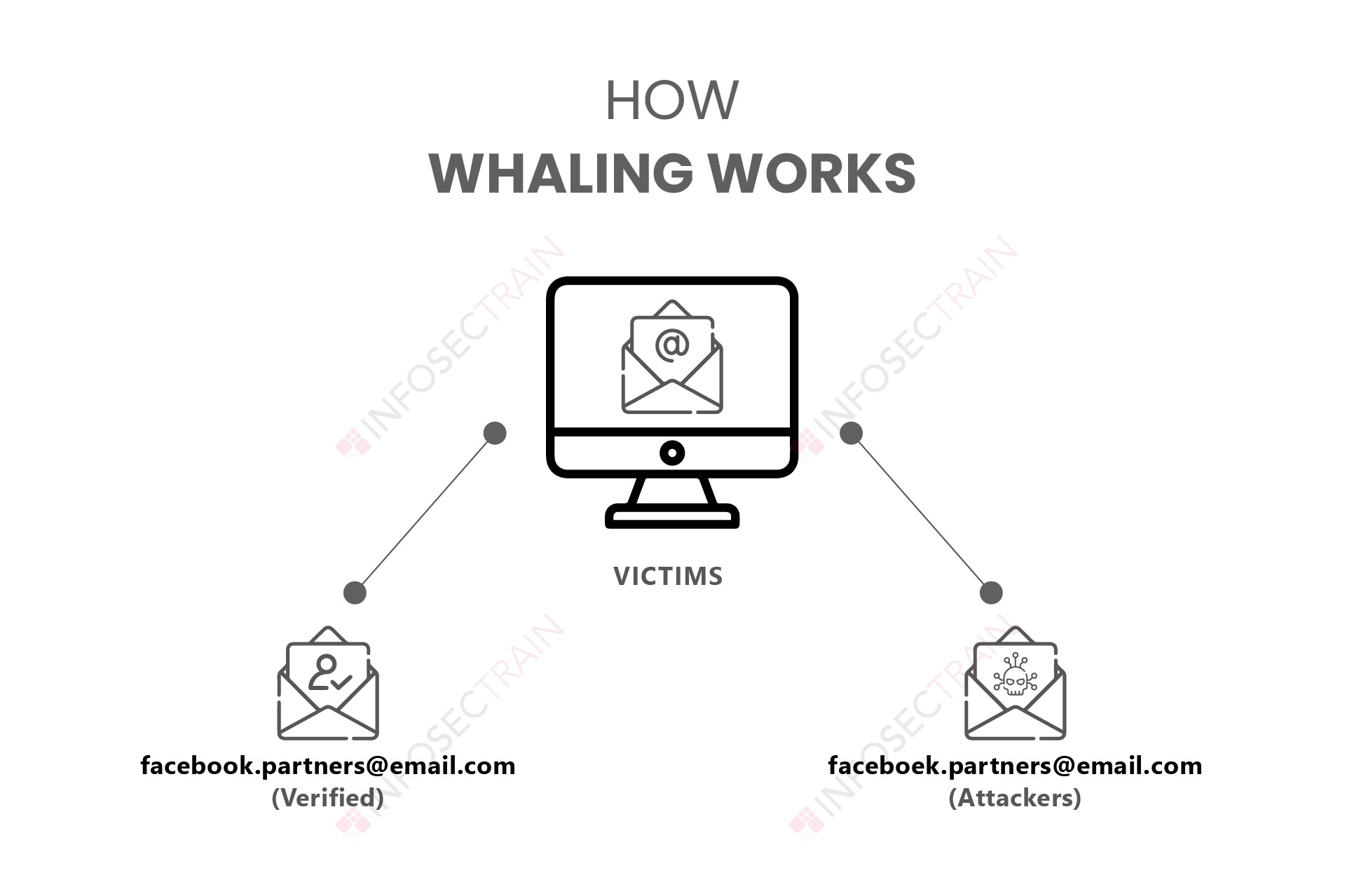
Whaling is a variant of spear phishing in which the perpetrator targets top executives, artists, public figures, and other high-level individuals to get information or finances. In other circumstances, the attacker may mimic C-level executives to obtain staff-sensitive information or finances. Whaling, like spear phishing, is directed, but as the name implies, it only reaches for the big fish.
Spear Phishing vs. Whaling
Spear phishing and whaling are types of email phishing tactics cybercriminals use to gain your personal information. Login credentials, credit and debit card information, and other sensitive data. So here, we will discuss the difference between spear phishing and whaling.
1. Knowledge of victim’s identity
In both attacks, the attackers are aware of the victim’s identity, but whaling attack offenders are specifically aware of who they seek. They employ this information to increase the threat’s effectiveness and deceive the target into thinking they are a reliable party.
2. The aim of attacks
The objectives of a spear phishing attack are distinct from those behind a hacker’s whaling attack. In spear phishing, the attacker typically wants to seize available assets from the victims’ team. This might be a data asset, similar to intellectual property. The risks associated with whaling, however, are considerable. The victim, typically a high-ranking executive or well-known person, is convinced to hand over a sizable sum of money and information. While the hacker may occasionally want the victim’s login information, whaling attacks almost always have a financial goal in mind.
3. Level of privilege and the number of primary targets
Spear phishing and whaling diverge significantly in this realm. While both aim at highly privileged users, whaling targets boast even greater authority. Spear phishing, with multiple victims, is often haphazard. While victims may offer sought-after data or funds, their privilege level remains relatively modest in contrast to whaling targets.
4. Business email utilization risk
Business Email Compromise (BEC), sometimes known as man-in-the-email schemes, deceive victims by using publicly available information on database administrator email IDs. Whaling campaigns (particularly CEO fraud, in which the fraudster poses as a C-level executive from the firm) frequently employ BEC as a phishing technique. Spear phishing depends on harmful email attachments, misleading hyperlinks, spoofed user-login pages, and other techniques rather than BEC.
5. Consequences
Successful whaling attacks usually have far higher expenses than spear phishing. The reward for hackers is likewise smaller because spear phishing targets users with fewer privileges. On the other hand, a successful whaling attack suggests flagrant ignorance somewhere, and CEOs, COOs, and other senior executives are often schooled in cybersecurity best practices.
| Spear Phishing | Whaling |
|
|
|
|
|
|
|
|
|
|
How can InfosecTrain help?
Ready to fortify your cybersecurity knowledge? Enroll in InfosecTrain‘s comprehensive cybersecurity training courses like CompTIA Security+, CEH, and more today! Get the knowledge and tools to deal with sophisticated cyberattacks. Do not let yourself and your organization be victims – learn to defend against these attacks. Join now to strengthen your defenses and stay ahead in the cybersecurity game!







 1800-843-7890 (India)
1800-843-7890 (India)