Types of DDoS Attacks?
DDoS attacks have become a recurring and significant problem for enterprises and organizations of all sizes. These attacks pose a constant and severe threat to network infrastructure, online services, and business operations in today’s digital landscape. These attacks can have devastating impacts on businesses, including financial losses, reputational damage, and disruption of critical services. These attacks can leverage compromised device networks to flood targets with overwhelming traffic.

Let us discuss what a DDoS attack is and DDoS attack types.
Table of Contents
DDoS Attack Overview
Types of DDoS Attacks
Volumetric Attacks
Protocol Attacks
Application Layer Attacks
DDoS Attack Overview
A Distributed Denial-of-Service (DDoS) attack is a malicious attempt to disrupt the availability or performance of a targeted network, system, or application by overwhelming it with a flood of illegitimate traffic or requests. Multiple compromised devices are used to generate the attack traffic in this attack. The aim is to exhaust the target’s resources, such as network bandwidth, processing power, or memory, causing disruption or rendering the target inaccessible to legitimate users.
Types of DDoS Attacks:
DDoS attacks are classified into three types:
Volumetric Attacks: Volume-based or Volumetric attacks aim to overwhelm a target by flooding it with a massive volume of traffic, saturating its network bandwidth and resources. These attacks typically utilize many compromised devices (a botnet) to generate overwhelming traffic. Volumetric attacks can disrupt the availability of a targeted network, service, or application.
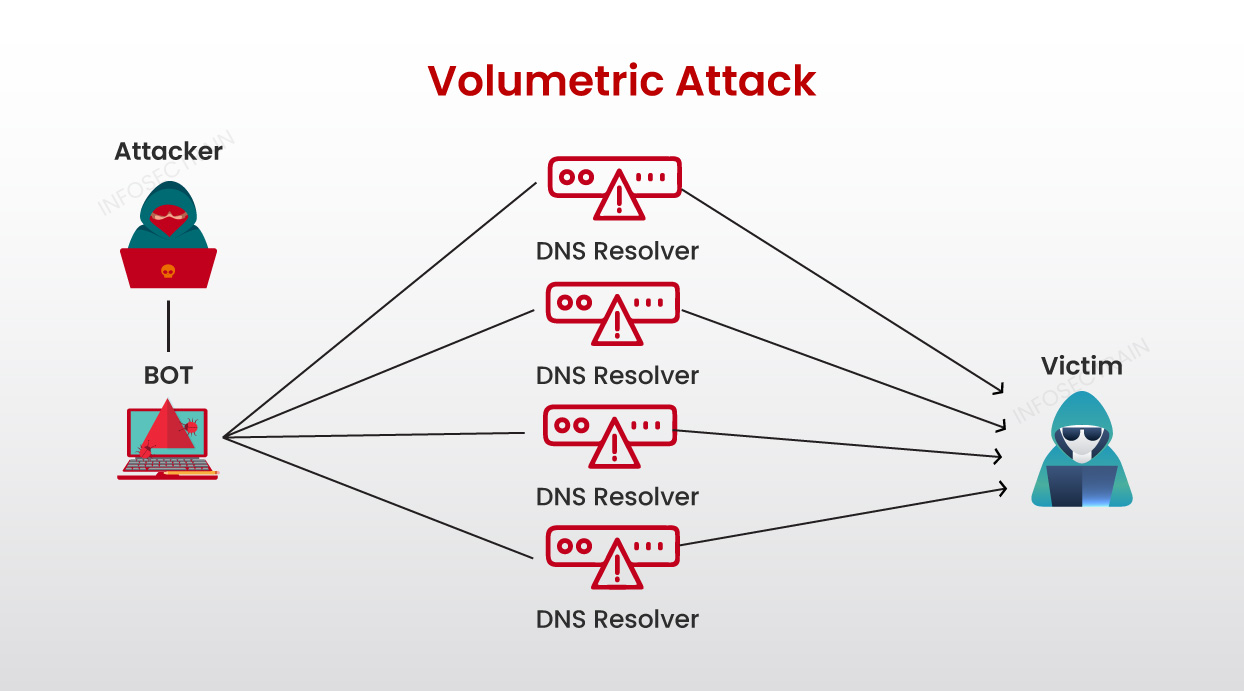
Common DDoS attacks in this category include:
1. DNS Amplification: This attack exploits vulnerable DNS servers to generate a massive volume of traffic toward the target.
2. ICMP Flood: This attack floods the target with a high volume of ICMP (Internet Control Message Protocol) packets.
3. UDP Flood: This attack floods the target system with a high volume of UDP packets to overwhelm network resources.
4. Ping of Death: This attack sends oversized or malformed ICMP packets to the target to crash vulnerable systems.
Protocol Attacks: Protocol attacks exploit vulnerabilities or weaknesses in network protocols to disrupt or disable network services. These attacks target specific protocols used in networking to exploit their design flaws and overwhelm the target system or network.
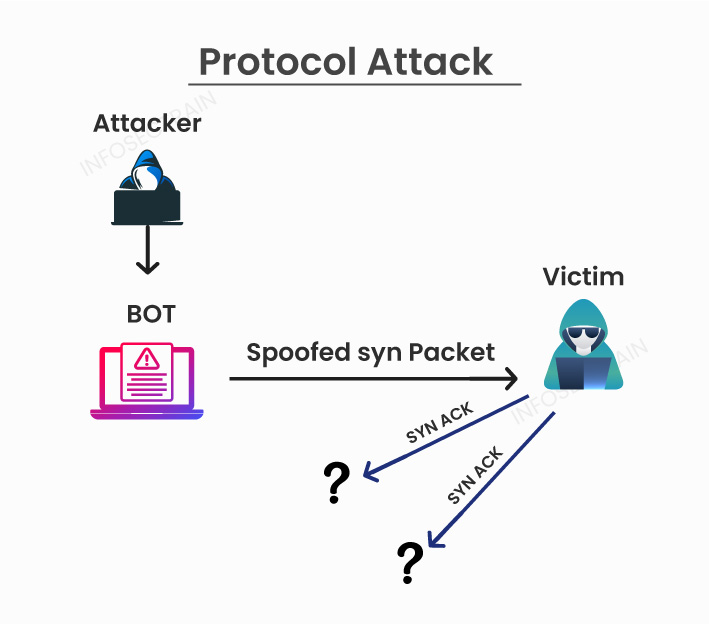
Common DDoS attacks in this category include:
1. SYN Flood: This attack overwhelms a target by flooding it with TCP SYN packets, exhausting resources, and preventing legitimate connections.
2. Fragmentation Attack: This attack exploits vulnerabilities in the IP packet fragmentation process to overwhelm the target’s resources.
Application Layer Attacks: Application layer attacks target vulnerabilities or weaknesses in the application layer of a network protocol stack. These attacks exploit flaws in the design, implementation, or configuration of applications, often aiming to disrupt availability, compromise integrity, or steal sensitive information from the targeted system.
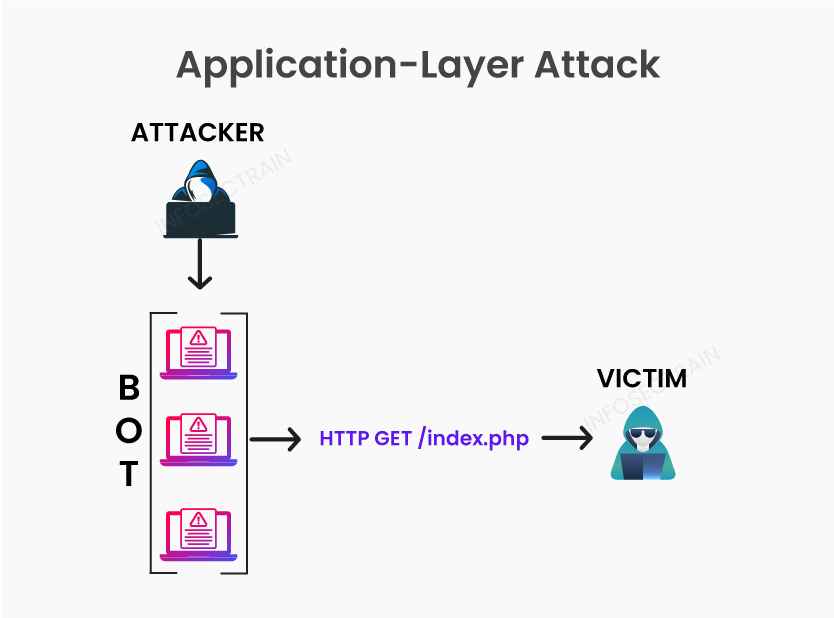
Common DDoS attacks in this category include:
1. HTTP Flooding: This attack floods the target server with an excessive number of HTTP requests, consuming its resources and making it unable to respond to legitimate user requests.
2. Slowloris: This attack exploits web server resource limits by keeping multiple connections open with partial HTTP requests, exhausting server resources, and preventing new connections.
Related articles:
- Common Cyber Attacks and Ways to Prevent Them
- Types of Network Security Attacks
- How to Protect Organizations from Cyberattacks?
- How To Prevent Zero-Day Attacks?
How can InfosecTrain help?
Enroll in InfosecTrain‘s Certified Ethical Hacker (CEH) certification training course to learn about DDoS attack techniques, tools, mitigation strategies, and best practices to defend against them. We offer hands-on exercises, recorded sessions, workshops, and other resources to help individuals and organizations better understand DDoS attacks and develop effective strategies to mitigate and respond to them.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 06-Apr-2025 | 24-May-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Close ] | |
| 26-Apr-2025 | 01-Jun-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Close ] | |
| 11-May-2025 | 28-Jun-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 31-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |







 1800-843-7890 (India)
1800-843-7890 (India)