What is Session Management?
Session management is a critical security aspect for web applications that aims to establish a strong and cryptographically secure link between authenticated users and their sessions. This ensures that users’ identities and session data are protected. It helps protect user data, prevent unauthorized access, and mitigate session-related vulnerabilities such as session hijacking or session fixation attacks. By properly managing user sessions, web applications can ensure the confidentiality, accessibility, and accuracy of user interactions, enhancing overall security posture.

Table of Contents
Introduction to Session Management
Key Components of Session Management
Types of Session Management
Introduction to Session Management
Session management is the process of maintaining and controlling user sessions in a web application or system. It involves managing the interaction between a user and the system during a specific period. It involves assigning a unique session identifier to each user, which is stored on the server side and used to retrieve relevant session data. It ensures that users remain authenticated throughout browsing and enables personalized experiences. This facilitates session state maintenance, timeout management, and secure logout handling, ensuring seamless, secure experiences.
Key Components of Session Management
Below are the key components of session management:
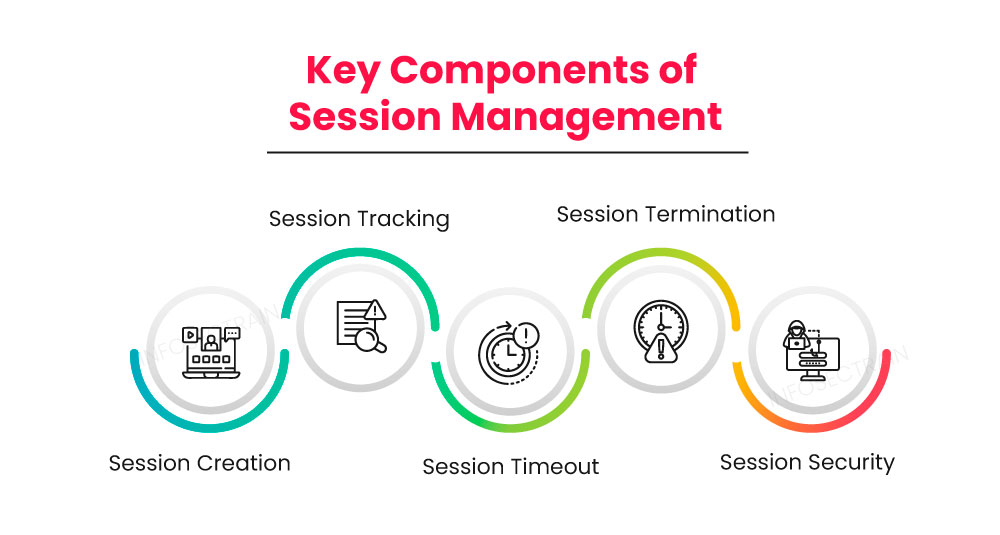
- Session Creation: When a user initiates a session by accessing a web application, a unique session ID is generated for that user. This ID identifies and associates the user’s interactions with the session.
- Session Tracking: The server keeps track of active sessions by associating each session ID with relevant user data. This data can be stored in server-side storage, such as a database or memory cache.
- Session Timeout: Sessions have a predefined timeout period to ensure that inactive sessions are automatically terminated. When a session runs out, the user must log in again to establish a new session.
- Session Termination: Users can manually terminate their sessions by logging out of the application. When a session is terminated, all associated session data is cleared, and the session ID becomes invalid.
- Session Security: Session management systems use security measures to protect against session hijacking or fixation attacks and unauthorized access.
Types of Session Management
There are two main types of session management:
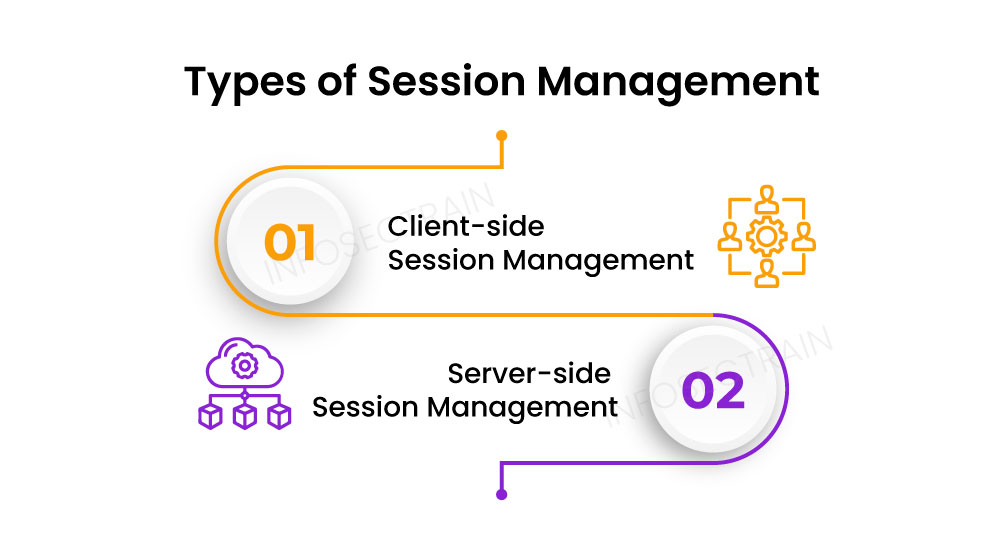
Client-side Session Management: In this type, the session data is stored and managed on the client side, typically within a cookie or using browser storage mechanisms such as local or session storage. The session data may be encrypted or encoded to maintain security. The server relies on the client to send the session data with each request, and the server validates and processes it accordingly.
Server-side Session Management: In this type, the session data is stored and managed on the server. The server generates a distinct session ID for each user and maintains the associated session data. The session ID is typically stored as a cookie on the client side and sent with each request. The server retrieves the session data based on the session ID and uses it to maintain user state and perform authentication and authorization checks.
How can InfosecTrain Help?
You may enroll in InfosecTrain‘s Web Application Penetration Testing online training course to gain in-depth knowledge about session management and its associated security considerations. The course will provide comprehensive insights into session management techniques, vulnerabilities, and exploitation methods for securing sessions. During this training, we will provide you with hands-on labs and real-world scenarios to simulate the testing and exploitation of session management vulnerabilities. This hands-on experience will help you develop the skills and techniques to identify, exploit, and remediate session-related security issues in web applications. You will also learn how to implement effective security measures to safeguard user sessions.







 1800-843-7890 (India)
1800-843-7890 (India)