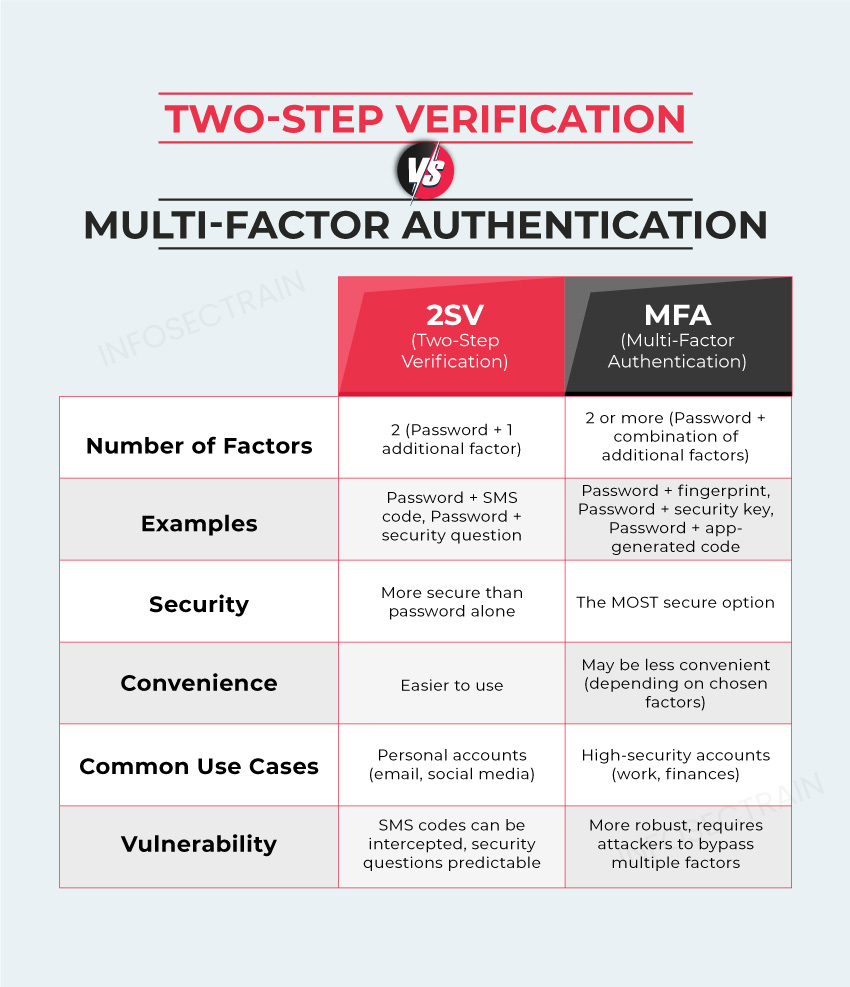
Two-Step Verification vs. Multi-Factor Authentication
Our online footprint holds immense value in today’s digital age, from professional credentials to personal memories. However, it has also exposed us to a constant barrage of security threats. While usernames and passwords are the first line of defense, they’re no longer enough. This is where Two-Step Verification (2SV) and Multi-Factor Authentication (MFA) emerge as powerful tools, providing additional layers of security. Let us understand the differences between 2SV and MFA.

The Core Concept: Authentication Factors
Authentication verifies a user’s claimed identity during a login attempt. Traditionally, this relied on a single factor – a password. However, passwords are susceptible to theft or brute-force attacks. 2SV and MFA introduce additional authentication factors, making unauthorized access significantly more difficult.
- Something You Know: This could be a password, PIN, or security question answer.
- Something You Have: This includes physical tokens, security keys, or one-time codes generated by an app on your smartphone.
- Something You Are: Biometric factors like fingerprints, facial recognition, or iris scans fall into this category.
Two-Step Verification (2SV) Explained
2SV adds a second step to the login process after entering your username and password. This second step typically involves:
- Security code: A one-time code sent via SMS text message or generated by an authentication app on your phone.
- Security question: Answering a predefined security question.
While 2SV is a significant improvement over passwords alone, it has limitations. SMS text messages, a common method for sending codes, are susceptible to interception. Additionally, security questions can sometimes be predictable, making them less secure.
Multi-Factor Authentication (MFA) Explained
MFA builds upon 2SV by requiring two or more of the three authentication factors mentioned earlier. This offers a more robust defense against unauthorized access attempts. Here are some common MFA methods:
- Password + Security Key: This combines something you know (password) with something you have (physical security key).
- Password + Biometric Authentication: This combines something you know (password) with something you are (fingerprint, facial recognition).
- Password + Authentication App: This combines something you know (password) with something you have (one-time code generated by an app).
MFA offers greater security compared to 2SV. Since it requires multiple factors, it becomes more challenging for attackers to bypass, even if they have access to your password.
Choosing the Right Method: Security Needs and Convenience
So, the question arises- which is better 2SV or MFA? The ideal method depends on the level of security required and your preference for convenience.
- For high-security accounts like financial institutions or work accounts with sensitive data, MFA is the recommended choice.
- 2SV offers a good balance between security and convenience for personal accounts with less sensitive information.
Additional Considerations: Usability and Backup Options
While security is paramount, usability should also be factored in. Opting for an MFA method that integrates seamlessly with your workflow can encourage consistent use. Additionally, ensure you have a backup plan for retrieving MFA codes in case you lose your phone or security key.
In conclusion, 2SV and MFA significantly enhance the security of your online accounts compared to relying solely on passwords. Understanding their differences empowers you to make informed decisions about protecting your digital identity. Remember, security is an ongoing process. Stay updated on evolving threats and best practices to keep your accounts safe.
How can InfosecTrain Help?
Cybersecurity extends far beyond personal protection. InfosecTrain offers a range of carefully crafted certification training courses for those seeking to elevate their cybersecurity expertise and protect their organizations. These courses, designed by industry experts, equip participants with the necessary skills to navigate the unpredictable cybersecurity landscape. From penetration testing to incident handling, InfosecTrain strives to provide a unique learning experience that empowers individuals to become valuable assets in the fight against cybercrime.







 1800-843-7890 (India)
1800-843-7890 (India)