A Beginner’s Guide to Common Network Protocols
Did you know? The Internet relies on a hidden language – a set of protocols governing how devices communicate. Think of these protocols as the established language spoken by devices on a network. These standardized procedures act as a roadmap, ensuring data travels from one point to another securely and efficiently. This article serves as a guide to some of the most common network protocols you’ll encounter.

Top Common Network Protocols
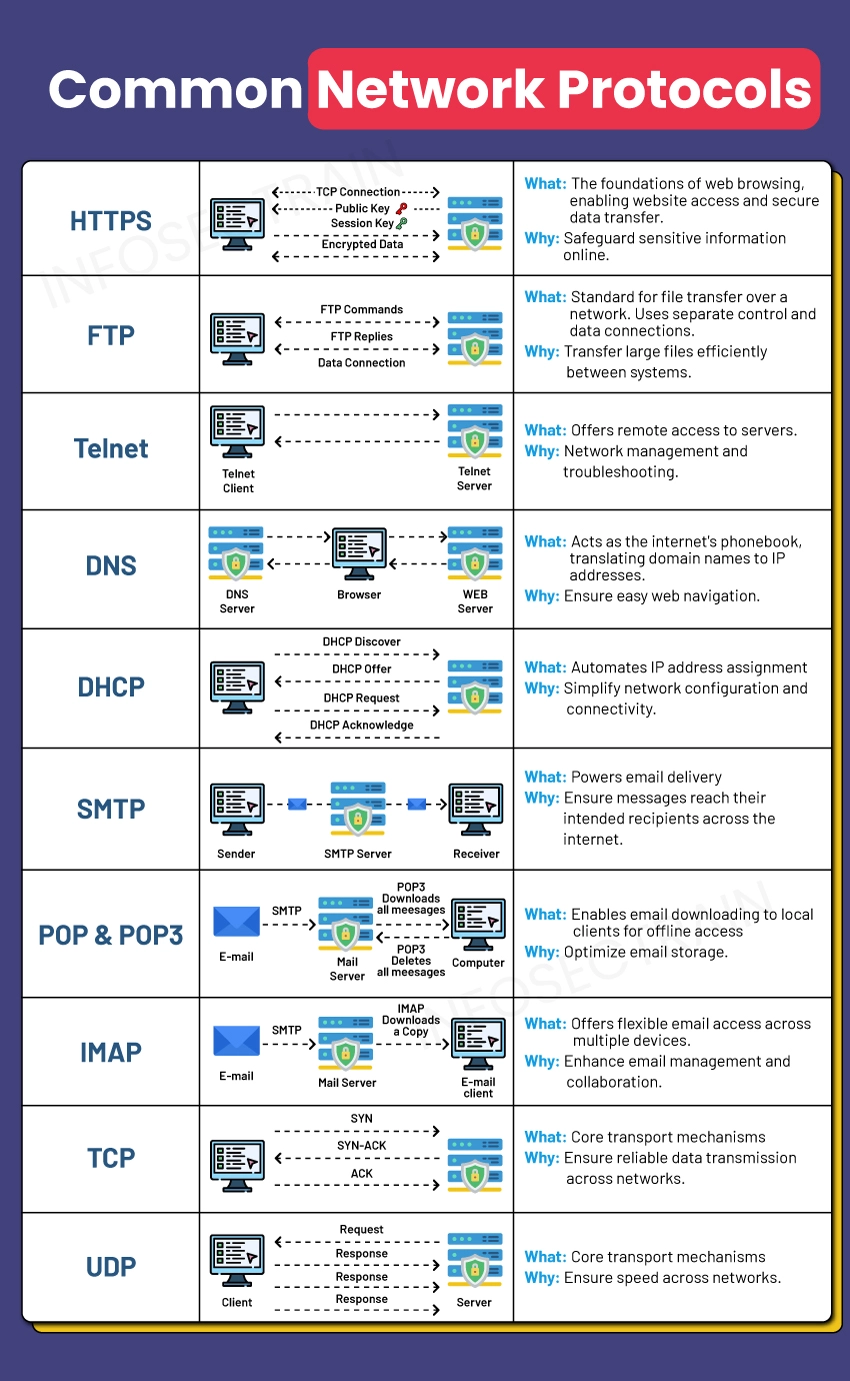
Hypertext Transfer Protocol Secure (HTTPS): The Guardian of Online Security
Without HTTPS acting as a secure tunnel, any sensitive information you submit on a website travels “naked” across the Internet, vulnerable to prying eyes. Thankfully, HTTPS protocol acts as a secure communication channel, encrypting the data transmission between your web browser and the website. This encryption technology scrambles the data, making it unreadable to anyone who might intercept it.
File Transfer Protocol (FTP): Moving Gigabytes with Ease
Need to transfer a large video file to a colleague or upload a website update to your server? This is where FTP comes in handy. It’s the workhorse of file sharing, establishing a dedicated channel for transferring files efficiently across networks. FTP utilizes two separate connections: one for managing commands (like requesting a file transfer) and another specifically for transferring the actual data. This streamlined approach ensures faster and more reliable file transfers than simply sending files through email attachments.
Telnet: Reaching into the Server Room
For network administrators, Telnet offers a powerful tool for managing servers remotely. Imagine having a virtual extension cord that allows you to connect to a server in another location and execute commands directly on that machine. Telnet provides this functionality, enabling administrators to monitor system performance, troubleshoot issues, configure settings, and perform maintenance tasks efficiently without physically being present at the server location.
Domain Name System (DNS): The Internet’s Phonebook
Have you ever wondered how you access websites simply by typing in a user-friendly domain name instead of a complex string of numbers? DNS serves as the Internet’s phonebook, translating these easily remembered domain names into corresponding IP addresses that computers can understand. This crucial service simplifies web navigation by eliminating the need to memorize numerical codes for every website you visit.
Interestingly, DNS protocol also plays a critical role behind the scenes in other internet functionalities. For example, it helps route email messages to the correct recipient’s server.
Dynamic Host Configuration Protocol (DHCP): Simplifying Network Management
Imagine a network with hundreds of devices requiring a unique IP address to communicate. DHCP protocol automates this process, eliminating the need for manual configuration. It acts like an automated network administrator, dynamically assigning unique IP addresses to devices as they join the network. This simplifies network setup and management and ensures efficient allocation of IP addresses, preventing conflicts and maintaining smooth network operation.
Simple Mail Transfer Protocol (SMTP): The Mail Carrier of the Digital World
The Simple Mail Transfer Protocol acts as the unseen courier service, ensuring your email reaches its destination when you hit “send.” It dictates the rules for how emails are formatted, routed, and delivered to their intended recipients across the Internet. Think of it as the mail carrier in the digital world, ensuring your messages reach the correct mailboxes.
Post Office Protocol ( POP 3) & Internet Message Access Protocol (IMAP): Managing Your Digital Mailbox
Once emails are delivered, how do you access them on your computer? This is where POP 3 and IMAP come into play. Both protocols retrieve emails from a mail server to a local email client on your device.
- POP3 (Post Office Protocol Version 3): Emerged as a solution for managing email in an earlier era. It allows users to download emails from a server to their local device. This downloaded copy can be managed on the device, enabling users to read, organize, and delete emails as needed, even when offline.However, a key limitation of POP3 is its focus on single-device management. This means downloaded emails are primarily accessible from the device they were downloaded to, making it less convenient for users who access their email from multiple devices.
- Internet Message Access Protocol (IMAP): A more contemporary approach, IMAP offers greater flexibility than POP. It allows you to download a copy of an email for offline access on your device while the original message remains on the server. This lets you access and manage your emails from any device, just like checking a virtual mailbox from anywhere, similar to accessing your physical mailbox from different locations.
Transmission Control Protocol (TCP) & User Datagram Protocol (UDP): The Language of Data Delivery
Imagine sending a package across the country. There are two main approaches: guaranteed delivery with verification or faster delivery with the possibility of missed packages. TCP and UDP function similarly when it comes to data transmission across networks.
- Transmission Control Protocol (TCP): TCP is known for its reliability, as it establishes a connection between the sender and receiver before data transmission begins. It breaks down data into packets, transmits them, and verifies their successful delivery with acknowledgments. This ensures all data packets arrive in the correct order at the destination, making it ideal for applications that require high accuracy, like file transfers or video conferencing.
- User Datagram Protocol (UDP): Designed for speed, UDP prioritizes faster transmission over guaranteed delivery. It sends data packets without establishing a prior connection or verifying their arrival. This makes it suitable for real-time applications where speed is vital, such as online gaming or live streaming, where a slight delay or missing data packet might not be critical.
These are just a few examples of the many protocols that form the backbone of the Internet. From ensuring secure communication to streamlining file transfers and managing email, these protocols work tirelessly to facilitate the seamless flow of information across the digital world.
How can InfosecTrain Help?
Master the network language with InfosecTrain’s CompTIA Network+ Online Certification Training. This program equips you with the knowledge to navigate network protocols through interactive modules, practical labs, and expert instruction. You’ll gain a solid understanding of network fundamentals, delve into common protocols like TCP/IP, DNS, and DHCP, explore security best practices, and develop troubleshooting techniques. Boost your resume with a valued CompTIA Network+ credential, open doors to exciting IT careers, gain hands-on experience, and learn from industry-certified instructors passionate about network security – all with the flexibility of our online program.







 1800-843-7890 (India)
1800-843-7890 (India)