What is LogShield APT Detection Framework?
Organizations seek innovative solutions to stay ahead of the continually expanding array of cyber threats. The LogShield APT Detection Framework is a beacon of excellence in cybersecurity, providing a proactive defense against Advanced Persistent Threats (APTs). By adopting advanced techniques and staying ahead of the threat landscape, this framework enables organizations to prevent APTs and protect their digital assets proactively. As APTs evolve, LogShield continues to serve as a reliable ally, ensuring organizations remain well-prepared for the cybersecurity challenges of today and tomorrow.
What is the LogShield APT Detection Framework?
LogShield is a groundbreaking framework that utilizes a transformer-based architecture to detect advanced persistent threat (APT) attack patterns within system logs. LogShield effectively captures how events are related in provenance graphs by using the self-attention mechanism found in transformers. This enables the framework to identify nuanced patterns that could signify APT activity. Its proactive approach sets it apart in cybersecurity, offering an effective means of early detection. With LogShield, organizations gain a powerful tool to safeguard against sophisticated cyber threats.
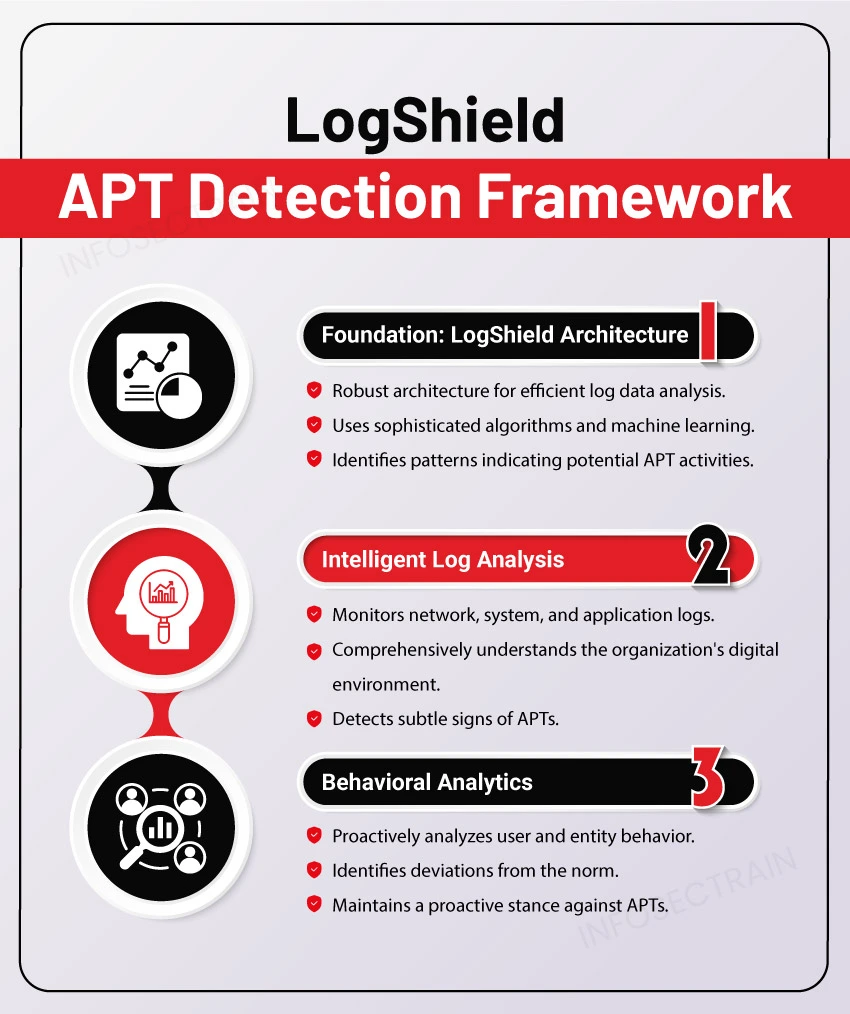
- The Foundation: LogShield Architecture: LogShield’s robust architecture forms the foundation. It was meticulously designed to sift through extensive volumes of log data efficiently. Utilizing advanced algorithms and machine learning, it actively detects patterns and anomalies that may signal potential APT activities.
- Intelligent Log Analysis: LogShield excels in performing intelligent log analysis, showcasing its strength. The framework monitors various log sources, including network, system, and application logs, to comprehensively understand the organization’s digital environment. This active and holistic approach empowers LogShield to detect subtle signs of APTs that might elude traditional security measures.
- Behavioral Analytics: LogShield distinguishes itself with a standout feature – its proactive emphasis on behavioral analytics. Instead of relying solely on signature-based detection, LogShield analyzes user and entity behavior to identify deviations from the norm. By adopting this approach, organizations can maintain a proactive stance against APTs, consistently adapting to their evolving tactics.
Benefits of LogShield APT Detection Framework
1. Enhanced APT Detection Accuracy: LogShield achieves enhanced APT detection accuracy through its transformer-based approach, leveraging the self-attention mechanism. By employing LogShield, the system effectively captures contextual relationships between events in provenance graphs. Consequently, LogShield identifies subtle patterns and anomalies that may indicate APT activity, resulting in more accurate detection and reduced false positives.
2. Continuous Learning and Improvement: LogShield ensures continuous learning and improvement through its adaptive training strategy and capabilities. The framework actively stays up-to-date with evolving APT threats and TTPs, maintaining its effectiveness over time and enhancing its ability to protect against emerging threats.
3. Enhanced Integration with SIEM Systems: LogShield actively enhances integration with Security Information and Event Management (SIEM) systems, enabling real-time threat monitoring, alert correlation, and streamlined incident response workflows. This active integration facilitates timely responses to potential APT attacks, contributing to the efficiency of security operations.
4. Reduced Computational Overhead: LogShield’s optimized architecture and model parameters reduce computational overhead. This active optimization makes real-time APT detection scenarios practical, enabling organizations to continuously monitor their systems without compromising performance or resource utilization.
5. Improved Generalizability: LogShield demonstrates improved generalizability by adapting to various system environments and APT attack patterns. This active ability ensures that LogShield can maintain its detection performance even when confronted with new or evolving APT threats, providing continuous protection.
Implementation and Integration of LogShield APT Detection Framework
Step 1: Log Data Collection and Preprocessing
- Identifying Data Sources: Determine the relevant system logs, network traffic logs, and endpoint data sources that LogShield will utilize.
- Implementing Data Collection Mechanisms: Set up mechanisms to collect and store the identified log data from various sources in a centralized location.
- Conducting Data Preprocessing and Normalization: Apply data preprocessing techniques to clean, normalize, and structure the raw log data, ensuring compatibility with LogShield’s input format.
Step 2: LogShield Deployment and Configuration
- Choosing Deployment Environment: Select a suitable deployment environment for LogShield, considering scalability, performance requirements, and integration with existing infrastructure.
- Configuring Model: Set up LogShield’s model parameters, including embedding layers, attention mechanisms, and training strategies, aligning them with your organization’s log data characteristics.
- Integrating with Security Information and Event Management: Incorporate LogShield into your SIEM system to enable real-time threat monitoring, alert correlation, and streamlined incident response workflows.
Step 3: Model Training and Evaluation
- Dividing the Preprocessed Log Data: Divide the preprocessed log data into training, validation, and testing sets to assess the model’s performance during training and refinement.
- Training the Model: LogShield’s transformer-based model actively leverages training data to optimize its parameters, maximizing accuracy in APT detection while minimizing false positives.
- Evaluating the Model: Assess the trained model’s performance on the validation and testing sets, evaluating its ability to generalize unseen data and identify actual APT attacks.
Step 4: Continuous Monitoring and Refinement
- Real-time APT Detection: Continuously monitor incoming log data with the trained LogShield model to identify and prioritize potential APT threats in real-time.
- Threat Intelligence Integration: Integrate threat intelligence feeds into LogShield to update its knowledge base of APT indicators and TTPs, enhancing its detection capabilities.
- Model Refinement and Adaptation: Periodically retrain the LogShield model with new data and refine its parameters to maintain effectiveness against evolving APT threats.
Cybersecurity Training with InfosecTrain
InfosecTrain, a proficient global entity in technology and security training, offers a range of cybersecurity training programs and consulting services. Our programs deliver valuable insights and knowledge, empowering individuals to comprehend and effectively counteract the ever-evolving landscape of cybersecurity challenges. Our extensive courses accommodate individuals at all expertise levels, catering to beginners and seasoned professionals. InfosecTrain provides various advantages, including flexible training schedules, session recordings for participants, ongoing post-training support, and the issuance of certificates of participation upon completion. Fortify your ability to safeguard digital assets by elevating your cybersecurity prowess through our cutting-edge training.







 1800-843-7890 (India)
1800-843-7890 (India)