The Ultimate Guide to SMTP and DNS Enumeration Practices
The sub-section of CEH module-4 provides an overview of enumeration strategies for extracting data pertinent to network resources. Additionally, it explores methods for DNS enumeration that offer insights into the organization’s DNS servers and network configuration. The content delves into both SMTP and DNS enumeration techniques, including how to perform SMTP enumeration to identify legitimate users on an SMTP server, the use of SMTP enumeration tools, strategies for DNS zone transfer, the practice of DNS cache snooping, and the method of DNS zone walking.
SMTP Enumeration
SMTP enumeration is a technique used in mail systems that rely on SMTP (Simple Mail Transfer Protocol) alongside POP3 (Post Office Protocol 3) and IMAP (Internet Message Access Protocol). SMTP is predominantly employed for dispatching emails, whereas POP3 and IMAP serve the purpose of email retrieval. POP3 enables users to download emails to their personal devices for offline perusal, contrasting with IMAP, which facilitates the organization and retention of emails on the server itself.
SMTP communicates with mail exchange (MX) servers responsible for routing emails via DNS (Domain Name System). DNS functions to translate domain names into their corresponding IP addresses and uses MX records to route emails to the appropriate mail servers by interpreting the domain segment of an email address.
SMTP operates on TCP (Transmission Control Protocol) ports. The default SMTP port is port 25. An alternative port, used in case port 25 is blocked, is port 2525. Port 587 is typically used for SMTP submission, which involves encryption and authentication. SMTP provides the following three in-built commands:
1. VRFY Command
- This command is used to verify the existence of an email address on the server.
- In the Telnet session, after issuing the HELO command and a domain address, the VRFY command is inputted.
- The server confirms known users and returns an error for unknown users.
2. EXPN Command
- This command is utilized to uncover the specific email addresses linked to a distribution list.
- Again, a Telnet session to the same SMTP server is shown, where the EXPN command is used after the initial greeting (HELO).
- The server confirms a known email and expands it to show the actual delivery address, but it returns an error for unknown emails.
3. RCPT TO Command
- This command is used to specify the recipient of the email message.
- For example, a Telnet session to an SMTP server at the IP address 192.168.168.1 on port 25.
- The server responds to the HELO command only after providing a domain address.
- The MAIL FROM command indicates the sender, and RCPT TO specifies the recipient.
SMTP servers exhibit different responses to VRFY, EXPN, and RCPT TO commands depending on whether the users are recognized as valid or not. This behavior allows for the identification of legitimate users on an SMTP server. By utilizing the Telnet interface, individuals can engage with the SMTP server to compile a list of authentic users.
SMTP Enumeration Tools
SMTP enumeration tools are used in cybersecurity to discover usernames by interacting with an email server. Cyber attackers can exploit such tools to gain information that could facilitate subsequent attacks on a network.
- NetScanTools Pro: NetScanTools Pro includes an SMTP Email Generator feature. This feature allows for the simulation of sending an email through an SMTP server. It can capture all the email header details, including specific flags like ‘confirm’ or ‘urgent.’ Attackers might use this to monitor and record the SMTP session, which is then stored in a log file for further analysis and potentially nefarious activities. The information is used to understand system vulnerabilities and to take preventive measures against unauthorized access.
- smtp-user-enum: The “smtp-user-enum” tool is designed for identifying operating system-level user accounts on Solaris systems by leveraging the SMTP protocol, typically implemented by the sendmail service. The tool works by examining server responses to specific SMTP commands such as VRFY, EXPN, and RCPT TO. To utilize this tool effectively, one must supply a list of user names and at least one target host that is running an SMTP service.
Command-line options for the smtp-user-enum tool, which is used for determining valid usernames on an SMTP server:
- -D dom: This option is used to append a domain to the list of user names provided, assisting in creating email addresses.
- -U file: Selects a file that contains a list of usernames to be checked by the SMTP service.
- -t host: Defines the server running the SMTP service to be queried.
- -T file: Chooses a file that lists the hostnames of servers running the SMTP service.
- -p port: Sets the TCP port on which the SMTP service is listening, the default being port 25.
- -d: Turns on debugging output for more detailed process information.
- -t n: Specifies a timeout value in seconds to wait for a response from the SMTP service, with the default being 5 seconds.
- -v: Enables verbose output, providing more detailed information during the operation.
- -h: Displays a help message with information about the command’s usage.
Additionally, other options include:
- -m n: Sets the maximum number of concurrent processes to run, with the default being 5.
- -M mode: Allows the selection of the SMTP command to be used for username guessing, with the options EXPN, VRFY, and RCPT TO; VRFY is the default.
- -u user: Checks if a specific user exists on the remote system.
- -f addr: Specifies the email address to be used in the “RCPT TO” command for guessing, with the default being user@example.com.

DNS Enumeration Using Zone Transfer
DNS Enumeration via Zone Transfer is like asking a main directory (the primary DNS server) to share its entire list of contacts and details with a backup directory (the secondary DNS server). This is normally done to back up and update information across servers.
However, a hacker can use this process to sneakily get a complete list of all the names, numbers, and addresses (like server names, machine names, usernames, and IP addresses) that are stored in the main directory, but only if the main directory is willing to share this information without proper checks. If the hacker’s request is denied, they’ll hit a dead end, as the main directory refuses to give out the list. They use tools like ‘nslookup’, ‘dig’, or ‘DNSRecon’ to try and make this request seem legitimate.
In a DNS zone transfer attack, the attacker pretends to be a legitimate entity, asking the DNS server to share a section of its directory containing a wealth of information about the network’s domain structure. The server, thinking the request is genuine, may send over details from its database about the network’s zone.
dig Command:
Attackers use the ‘dig’ command on Linux machines to interact with the target’s DNS name servers.
- Information Gathering: This command helps them gather data about target host addresses, DNS name servers, and mail exchange servers.
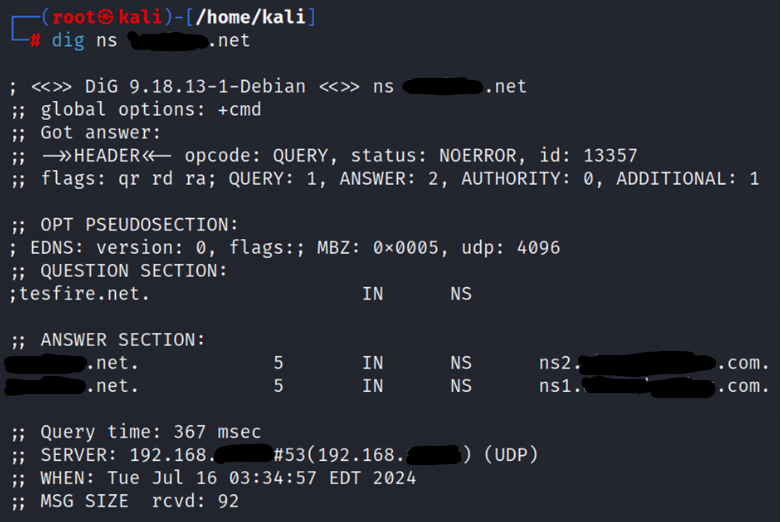
- Initiating Zone Transfer: To initiate a DNS zone transfer, they enter ‘dig ns <target domain>.‘
- List Retrieval: The command returns a list of all DNS name servers associated with the target domain.
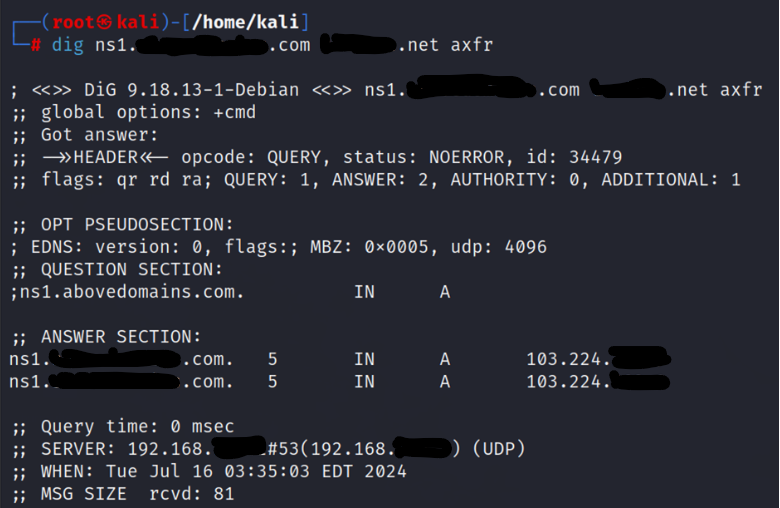
- Testing for Transfer Vulnerability: Using one of the listed name servers, the attackers then check if a zone transfer is possible with ‘
| dig @<domain of name server> <target domain> axfr’ |
‘nslookup’ Command
Attackers run the ‘nslookup’ command on Windows systems to request information from DNS name servers about a target’s hosts, name servers, and email servers.
- Setting Query Type: They configure the command to ask for the Start of Authority (SOA) record by using ‘set querytype=soa‘, which tells about the domain’s administrative details.
- Targeting Domain: Attackers input the target domain after setting the query type to get the SOA record information.
- Attempting Zone Transfer: To try and pull the zone data, they use the command
| ‘/ls -d <domain of name server>’ |

What is DNS Cache Snooping?
DNS cache snooping is when someone tries to find out what websites you’ve visited by looking at the saved data on a DNS server. Just like checking the history in your web browser, they can see the names of the sites you’ve been to. This can also tell them who runs the DNS server, who provides its internet service, and even sensitive stuff like banking details. The snoopers use special commands and tools to do this, kind of like using a special key to peek into someone’s diary.
- Non-Recursive Query: Attackers send a special kind of query that doesn’t ask the DNS server to look further if it doesn’t know the answer.
- Query for Cached Records: They ask for specific types of DNS records that are stored in the server’s memory.
- Server’s Response: If the record is there, the server confirms the site was visited; if not, it either points to another server or shares root server information.
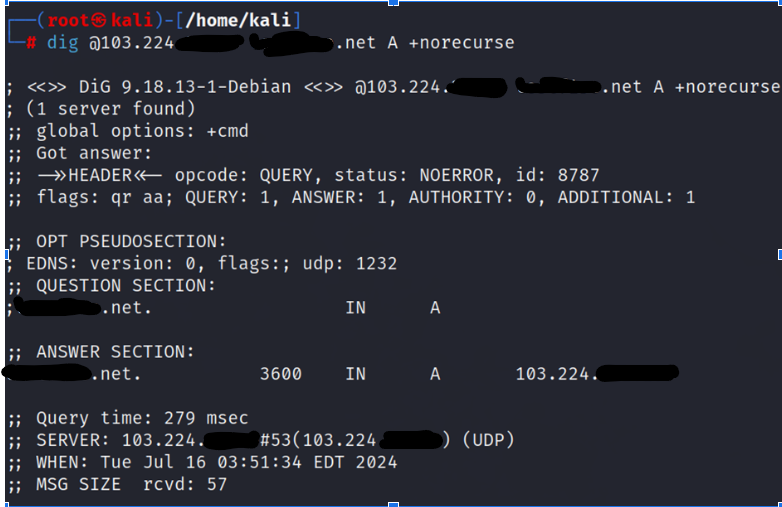
- ‘dig’ Command with No Recursion: Attackers use ‘dig’ with a special option to ensure the query stays non-recursive.
- Command Example: ‘dig @<IP of DNS server> <Target domain> A +norecurse’ is the format used.
- Recursive Query Method: Attackers send queries that allow the DNS server to request additional information from other servers if needed.
- Use of ‘+recurse’ Option: This method uses the ‘+recurse’ option instead of ‘+norecurse’, asking the server to keep looking for the answer.
- Checking Time-to-Live (TTL): They examine the TTL field to see how long the DNS record has been in the server’s cache.
- Determining Site Visitation: If the TTL is less than the set value, it means the site has been visited recently.
- Command Format: The ‘dig’ command is used with the DNS server’s IP, the target domain, and the ‘+recurse’ option for this method.

CEH with InfosecTrain
Ethical hacking is a complex and multi-phase process that requires deep knowledge and security certifications. Professionals can improve their security assessment and network architecture skills through ethical hacking courses, such as the Certified Ethical Hacker (CEH v12) training provided by InfosecTrain. This training provides individuals with the essential skills and methods needed to perform sanctioned hacking into organizations.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 06-Apr-2025 | 24-May-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Close ] | |
| 26-Apr-2025 | 01-Jun-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Close ] | |
| 11-May-2025 | 28-Jun-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 31-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |







 1800-843-7890 (India)
1800-843-7890 (India)