Interview Questions for Red Team Expert
Ever wondered if you’re truly prepared to tackle the challenges of cybersecurity from a Red Team perspective? In an age where threats evolve faster than ever, it’s not just about knowing how to hack, but understanding how to anticipate and outmaneuver attackers. But when you’re sitting across from an interviewer for that coveted Red Team expert position, will you know how to demonstrate those critical skills?
If you are preparing for a Red Team interview, you are in the right place. In this guide, we’ll uncover the most essential Red Team Expert interview questions and answers that will test your readiness to join the Red Team.
Red Team Expert Interview Questions
1. What is Red Teaming?
Red Teaming is a structured and systematic cybersecurity approach in which an organization identifies potential vulnerabilities and risks by adopting an adversary’s perspective. This approach involves creating a team of experts who use their knowledge, skills, and resources to simulate an attack against an organization’s security systems and processes.
2. Explain the Red Team attack lifecycle.
The Red Team attack lifecycle is a structured process that outlines the steps a Red Team takes to conduct a simulated attack on an organization. The following are the typical stages of the Red Team attack lifecycle:
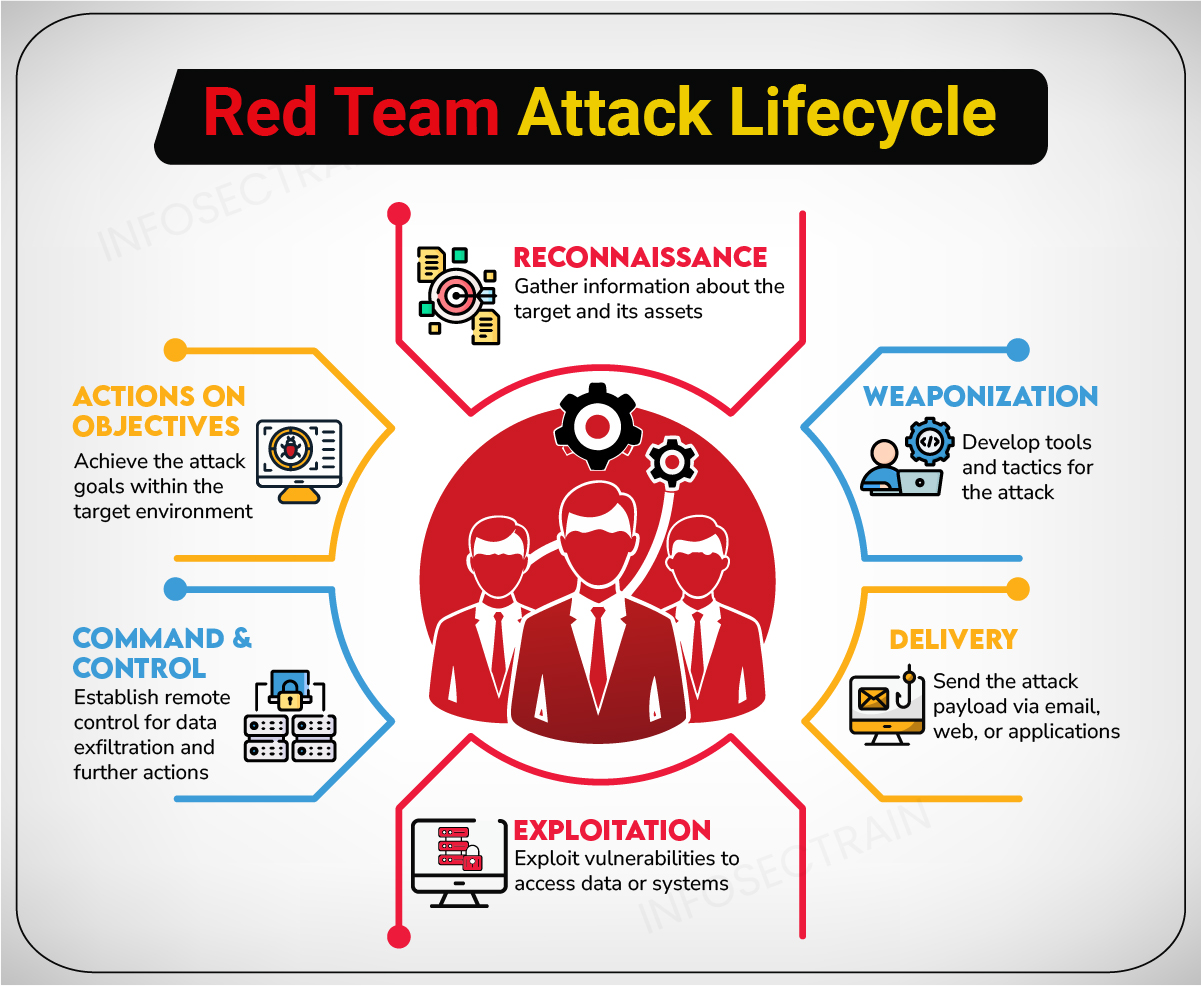
- Reconnaissance: During the reconnaissance phase, the Red Team gathers information about the target organization and its assets.
- Weaponization: In this stage, the Red Team creates the tools and tactics needed to execute the attack.
- Delivery: The Red Team delivers the attack payload to the target organization, typically via email, web, or other application-based methods.
- Exploitation: Once the attack is delivered, the Red Team exploits the vulnerability or security gap to gain access to sensitive data or systems.
- Command and Control: The Red Team establishes a Command and Control (C2) channel to remotely control the compromised system, exfiltrate data, and execute additional actions within the target environment.
- Actions on objectives: In the final stage, the Red Team achieves the attacker’s goals within the target environment.
3. What is Red Team engagement?
Red Team engagement is a security assessment that simulates a real-world attack on a company’s systems, applications, or network infrastructure. A Red Team engagement aims to identify vulnerabilities and weaknesses in a company’s security posture and help improve the organization’s overall security.
4. What are the main objectives of a Red Team exercise?
The primary objective of a Red Team exercise is to simulate real-world adversarial attacks to identify security gaps, test detection and response capabilities, and improve an organization’s overall security posture. By emulating Advanced Persistent Threats (APT) tactics, Red Team exercises assess weaknesses in technical controls, incident response, and procedural defenses. The goal is to provide actionable insights that help the organization prioritize remediation efforts, enhance defenses, and ensure resilience against sophisticated threats.
5. Can you explain the importance of “persistence” in red teaming?
Persistence in red teaming is essential as it allows Red Teams to maintain access to a compromised system over an extended period, even if the initial attack vector is discovered and remediated. This simulates the behavior of advanced adversaries, such as nation-state actors or Advanced Persistent Threats (APTs), who aim to stay hidden while gathering intelligence or moving laterally within the network.
The importance of persistence lies in its ability to simulate realistic, long-term attacks that test an organization’s ability to detect, respond, and eliminate hidden threats. By achieving persistence, Red Teams can demonstrate the potential impact of an undetected breach and help organizations strengthen their defenses and incident response capabilities.
6. How does Red Teaming differ from Penetration Testing?
| Aspect | Red Teaming | Penetration Testing |
| Scope | Simulates real-world adversaries across entire infrastructure | Focuses on finding vulnerabilities in specific systems or apps |
| Objective | Test response capabilities and resilience | Identify vulnerabilities for patching |
| Duration | Long-term, stealthy engagements | Short-term, point-in-time assessments |
| Approach | Focuses on evasion and persistence | Focuses on finding and exploiting known weaknesses |
7. What are the common Rules of Engagement (ROE) that you follow during an operation?
In any Red Team engagement, the Rules of Engagement (ROE) are critical for ensuring the operation is controlled, ethical, and aligned with the organization’s risk tolerance. Key ROEs to follow include:
- Scope Definition: Clearly define what’s in-scope and out-of-scope to focus on the right assets and avoid critical systems.
- No Destructive Testing: Avoid causing system downtime, data loss, or any operational impact.
- Time Windows: Perform operations during pre-defined time windows to minimize disruption to critical business processes.
- Stealth and Incident Handling: Maintain covert operations but have escalation procedures in place if detected.
- Fail-Safe Mechanisms: Use a kill switch to halt operations if things go wrong or if unintentional damage occurs.
- Legal Compliance: Ensure actions comply with legal frameworks, especially with social engineering or physical testing.
- Exploit Control: Limit the use of high-risk exploits, opting for safer techniques or simulations if needed.
- Exit Criteria: Define success criteria and ensure thorough clean-up after the engagement to restore the environment to its original state.
8. Explain the importance of reconnaissance in Red Team operations and the tools you use for it.
Reconnaissance helps gather crucial information about the target, enabling the Red Team to identify vulnerabilities and plan effective attacks. It can be passive (collecting data without interacting with the target, like using OSINT) or active (directly probing the target, like scanning ports).
Tools used for reconnaissance
Passive Tools:
- Maltego: For mapping relationships and dependencies using OSINT data
- Shodan: To identify internet-facing devices, services, and vulnerabilities
- Google Dorks: For finding sensitive information indexed by search engines
- Whois/DNS enumeration tools: For gathering domain registration and DNS record information
Active Tools:
- Nmap: For network scanning, service discovery, and port enumeration
- Nikto: To scan web servers for vulnerabilities and configuration issues
- Recon-ng: A powerful OSINT tool that automates data gathering
- Burp Suite: For web application reconnaissance and mapping vulnerabilities
9. What are some key techniques used by Advanced Persistent Threats (APTs) that you have simulated in your Red Team engagements?
To simulate Advanced Persistent Threats (APTs) in Red Team engagements, use several key techniques:
- Initial Access: Spear-phishing, brute force attacks, exploiting vulnerabilities.
- Execution: Using PowerShell, WMI, or batch files to execute malicious code.
- Persistence: Creating scheduled tasks, registry keys, or services for long-term access.
- Privilege Escalation: Exploiting vulnerabilities or using built-in tools to gain higher-level privileges.
- Lateral Movement: Spreading to other systems within the network using techniques like SMB or WMI.
- Exfiltration: Stealing data using techniques like FTP, email, or cloud storage.
10. How do you perform data exfiltration while avoiding detection in a network?
To perform data exfiltration while avoiding detection, use the following techniques like:
- Encrypted channels (e.g., HTTPS, SSH, or custom encryption) to hide the data
- Steganography to embed data in harmless files (e.g., images or videos)
- Living off the land by using legitimate tools like PowerShell and RDP
- Exfiltrate data in small, fragmented packets over time to avoid bandwidth alerts
- Domain fronting to route traffic through trusted services
- Tunneling protocols (e.SSH, Tor) to bypass monitoring
11. What is Living Off the Land (LoL), and how do you utilize it in Red Team engagements?
Living Off the Land (LoL) is a cyberattack technique where attackers use legitimate tools and features already present in the target’s environment to execute attacks rather than introducing external malware. Attackers leverage trusted system utilities (e.g., PowerShell, WMI, or CertUtil) to avoid detection by security solutions, as these tools are considered safe and commonly used within the network.
12. How do you handle privilege escalation after gaining initial access to a system?
After gaining initial access, handle the privilege escalation by systematically analyzing the system for vulnerabilities. The key steps include:
- System Enumeration: Collect detailed information about the system (like OS version, installed software, user permissions, etc.) to identify potential vulnerabilities.
- Exploiting Misconfigurations: Identify misconfigurations, such as weak file permissions, improperly set SUID/SGID files on Linux, or improperly configured services on Windows, to escalate privileges.
- Vulnerability Exploitation: If there are known vulnerabilities in the system, like unpatched software or outdated services, exploit them using local privilege escalation techniques (e.g., kernel exploits).
- Credential Harvesting: Search for stored credentials, such as plaintext passwords, SSH keys, or credentials in memory, to escalate privileges.
- Abusing Trusted Applications: Use trusted system applications to execute code with higher privileges, which helps in staying under the radar.
13. What social engineering techniques have you used during a Red Team operation?
Social engineering techniques used in Red Team operations:
| Technique | Description |
| Phishing | Sending fraudulent emails to trick users into revealing credentials or clicking malicious links. |
| Vishing | Voice-based attacks to impersonate legitimate entities and extract sensitive information. |
| Baiting | Leaving malicious USB drives in public areas to entice victims into plugging them into their devices. |
| Impersonation | Posing as an authorized person (e.g., IT staff) to gain physical or network access. |
14. What are the challenges of Red Teaming in cloud environments, and how do you overcome them?
Red teaming in cloud environments presents unique challenges due to the complexity, scale, and shared responsibility models of cloud platforms. Some key challenges and how to overcome them are:
- Visibility and Complexity: Cloud environments are highly dynamic, with constantly changing assets and configurations. Overcoming this requires an in-depth understanding of the specific cloud platform and cloud-native tools to track changes and identify attack vectors.
- Shared Responsibility Model: Cloud providers handle infrastructure security, while customers handle areas like data and access management. Red Teams must focus on the customer’s responsibility areas, like misconfigurations or weak access controls, and stay informed about the provider’s security practices.
- Multi-Tenant Risks: Attacking cloud systems can inadvertently affect other customers sharing the same infrastructure. Strictly follow the scope and rules to avoid affecting other customers in shared environments.
- Cloud-Specific Security Controls: Cloud environments use specific security mechanisms like IAM roles, VPCs, and security groups. To overcome this, Red Teams need a deep understanding of these cloud-native controls to find misconfigurations, weaknesses, etc.
- Limited Access to Infrastructure: In cloud environments, Red Teams often don’t have direct access to underlying infrastructure (e.g., hypervisors, network hardware). Instead, focus on application-level attacks, improper API usage, or IAM misconfigurations.
15. Can you explain how you leverage DNS tunneling for C2 (Command-and-Control) purposes?
To use DNS tunneling for C2 (Command-and-Control):
- Encode C2 commands in DNS queries/responses
- Use subdomains to send/receive data through DNS requests
- Exploit DNS as it often bypasses network restrictions
- Set up a C2 server to respond with encoded instructions
- Evades traditional network monitoring and firewall rules
16. What frameworks or methodologies do you follow when conducting Red Team engagements?
When conducting Red Team engagements, follow well-established frameworks to ensure a structured and comprehensive approach. Some of the key frameworks and methodologies include:
- MITRE ATT&CK Framework: This is widely used to understand adversarial tactics, techniques, and procedures. It helps structure the attack and identify loopholes in defenses.
- NIST Framework: NIST guidelines help ensure compliance with security standards and provide a structured process for testing and reporting vulnerabilities.
- Cyber Kill Chain: This model helps map the Red Team process from initial reconnaissance to exploitation, lateral movement, and exfiltration, providing a clear roadmap for attack phases.
- OWASP Top 10: For web application red teaming, use the OWASP Top 10 to identify common vulnerabilities like injection attacks, broken access control, and misconfigurations.
17. What strategies do you use to bypass Endpoint Detection and Response (EDR) systems?
To bypass EDR systems, use the following techniques to avoid detection:
- Living off the Land Binaries (LOLBins): Use legitimate system tools like PowerShell or Windows Management Instrumentation (WMI) to perform malicious activities without triggering EDR alerts.
- Obfuscation: Obfuscate payloads or scripts to evade signature-based detection.
- Fileless Attacks: Execute codes directly in memory through malicious macros or reflective DLL (Dynamic Link Library) injection to avoid writing files to disk where EDRs might catch them.
- Process Injection: Inject malicious code into legitimate processes to blend in with normal system activity and avoid detection.
- EDR Evasion Tools: Use tools like Mimikatz or Cobalt Strike alongside custom-built malware to evade common EDR detection methods, such as behavioral analysis.
18. What tools or techniques do you use for Open-source Intelligence (OSINT) gathering?
When conducting OSINT, different tools and techniques are used to gather publicly available information on the target. Some of the key tools include:
| Maltego | For mapping relationships, networks, and infrastructure using open-source data. |
| Recon-ng | An OSINT framework that automates data collection from multiple sources. |
| Shodan | A search engine to discover internet-connected devices, such as servers, routers, webcams, and IoT devices, and identify services and vulnerabilities. |
| Google Dorks | Specialized search queries to find sensitive information, misconfigurations, and exposed data indexed by search engines. |
| Whois and DNS enumeration tools | To gather domain registration data, IP address information, and DNS records. |
19. How would you execute a fileless attack, and why is it effective in evading detection?
A fileless attack is executed by leveraging legitimate system processes and running malicious code directly in memory without writing files to disk.
How to execute it:
- Initial Access: Use phishing or exploit vulnerabilities to execute code that does not require file downloads.
- Memory Injection: Inject malicious code into trusted processes using techniques like reflective DLL (Dynamic Link Library) injection.
- Living off the Land: Utilize built-in system tools to execute malicious commands, avoiding writing anything to the disk.
Why it’s effective:
- It bypasses traditional antivirus and EDR systems that rely on signature-based detection since no files are written to the disk.
- It blends with legitimate processes, making it harder for behavioral-based detection systems to differentiate between normal and malicious activity.
20. What kind of post-exploitation analysis do you include in your reports?
Post-exploitation analysis in reports:
- Privilege Escalation: Documentation of how privileges were elevated and any misconfigurations or vulnerabilities exploited.
- Lateral Movement: Description of how the team moved within the network and the gaps they exploited.
- Persistence: Explanation of how persistence was established, such as backdoors and the methods used to maintain access over time.
- Data Exfiltration: An analysis of how sensitive data was extracted stealthily.
- Recommendations: Detailed remediation steps to fix security vulnerabilities and improve defenses.
You can also check out for more interview questions:
Become a Red Team Expert with InfosecTrain
A Red Team expert is a specialized cybersecurity professional simulating attacks on an organization’s systems and infrastructure to improve its cybersecurity posture.
InfosecTrain is a prominent provider of information security training and services. Enroll in our online training course to learn how to be a successful Red Team Expert. Our course is created and designed by certified cybersecurity experts and Red Team professionals for aspiring Red Teamers.

 1800-843-7890 (India)
1800-843-7890 (India)