Steps for Effective DNS Footprinting
DNS (Domain Name System) footprinting is a crucial reconnaissance technique used to gather information about the target’s DNS infrastructure, which helps understand the network topology and identify potential vulnerabilities.
In this guide, we’ll walk you through various tools and techniques used by Penetration Testers and Ethical Hackers to perform DNS footprinting efficiently, step-by-step.
DNS Footprinting
DNS is like the phonebook of the internet. It translates human-readable domain names (like example.com) into IP addresses (like 192.168.1.1), which are essential for communication over the internet. It involves collecting DNS-related data about a target domain or network, such as IP addresses, subdomains, and DNS records. This information can help reveal critical infrastructure details and uncover potential attack vectors.
Common Objectives of DNS Footprinting
- Identifying subdomains and hidden domains
- Retrieving DNS records (A, MX, NS, CNAME)
- Uncovering potential attack vectors
- Understanding the target’s IP address space
How DNS Footprinting Works?
Here is a step-by-step breakdown of how DNS footprinting works:
Step 1: Gather Domain Information
Start by collecting basic information about the target domain, such as registrar details, contact information, and domain history. This preliminary step provides details about the domain’s ownership and may expose admin or contact details, which are useful for social engineering.
Tools: Use whois/dig/nslookup for domain lookups.
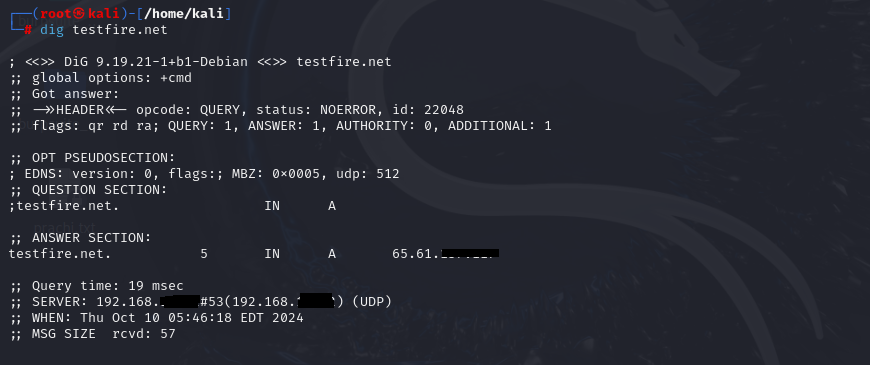
Command: dig testfire.net
Command: whois testfire.net
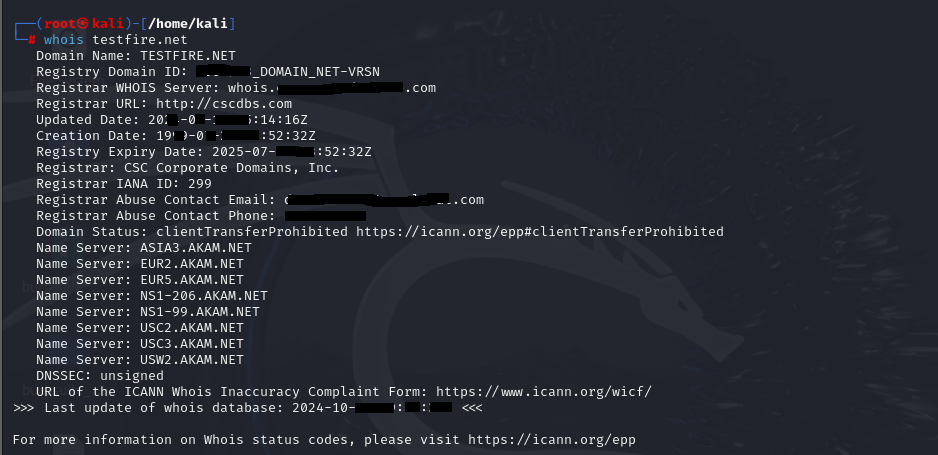
What it does: The dig and whois command provides essential details like domain registration dates, expiration, and potentially admin contact details. This can reveal the tech or administrative contacts who could be vulnerable to phishing or social engineering attacks.
Step 2: DNS Zone Transfers
Zone transfers allow one DNS server to share its data with another server in a synchronized way. Sometimes, a DNS server may allow an unauthorized zone transfer due to misconfigurations, exposing the entire domain’s DNS records, including A, MX, and TXT records.
Tool: Use dig/nslookup/fierce/axfr tool to attempt a zone transfer.
Command: dig AXFR testfire.net @ns1-206.akam.net.

Command:
nslookup
set querytype=soa
testfire.net
ls -d asia3.akam.net

What it does: These commands attempt a zone transfer. If successful, you gain access to a valuable source of information, such as internal DNS records, subdomains, mail servers, and other sensitive data.
Step 3: DNS Record Enumeration
DNS records contain essential details about how a domain is structured and how its services are organized. By enumerating DNS records, you can learn about the IP addresses, mail servers, and nameservers. Focus on gathering the following record types:
- A Record (Address Records): Maps domain names to IP addresses. For instance, www.targetdomain.com might map to 192.168.1.1. Knowing this IP helps in understanding the target’s network.
- MX Record (Mail Exchange Records): Lists mail servers, which might be a weak point for social engineering attacks.
- NS Record (Name Server Records): Nameservers that manage DNS queries for the domain.
- TXT Record: May contain useful info for email authentication (SPF, DKIM) and other records that provide details about the domain’s policies.
Tools: Use nslookup/dig/host to extract DNS records.
Command: dig testfire.net any

What it does: This command requests all available DNS records for the domain. Gathering A, MX, NS, and TXT records provides a detailed overview of the domain’s structure.
Step 4: Reverse DNS Lookups
Reverse DNS lookup can help map IP addresses back to their associated domain names. This step is useful if you only have an IP address to start with and want to discover the associated domains or infrastructure.
Tools: Use nslookup/dnsrecon for reverse DNS lookups.
Command: nslookup testfire.net

What it does: The command reveals the domain associated with a particular IP address, which can help map out the target’s infrastructure.
Step 5: Brute-Force Subdomain Enumeration
Finding subdomains is critical to DNS footprinting as they often reveal hidden or less-secured services running within the same infrastructure. Subdomains might be part of development environments, staging servers, or internal services.
Tools: Use Sublist3r/dnsenum/amass/Fierce for subdomain enumeration.
Command: sublist3r -d infosectrain.com
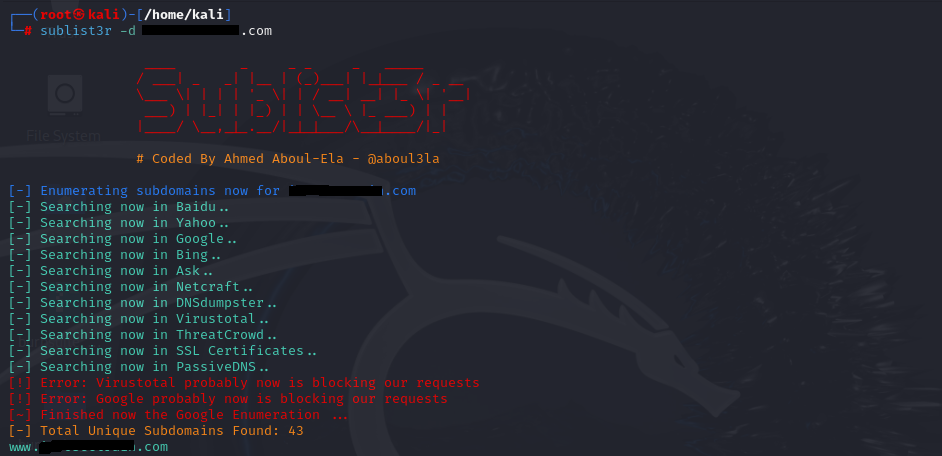
What it does: This tool uses wordlists and DNS records to discover subdomains associated with a domain. Finding hidden subdomains can lead to discovering more vulnerabilities.
Step 6: DNS Reconnaissance with Nmap
Nmap, a popular port-scanning tool, can also be used to extract DNS information. Using Nmap’s Scripting Engine (NSE), you can extract DNS information, identify misconfigurations, and check if zone transfers are allowed.
Tool: Nmap with NSE (Nmap Scripting Engine).
Command: nmap -sT -p 53 –script=dns-brute testfire.net

What it does: This command performs DNS brute-forcing, attempting to discover hidden subdomains or services that standard DNS queries might miss.
Step 7: Email Harvesting from DNS
Some DNS records (e.g., SOA and TXT records) that contain email addresses can be a goldmine for phishing attacks or further social engineering. While this is usually for legitimate purposes, careless configuration can leak this information.
Tool: Use theHarvester for email gathering.
Command: theHarvester -d infosectrain.com -b all

What it does: This tool scrapes email addresses from public sources and DNS records. Careless configuration can lead to the exposure of contact emails through DNS queries, which can then be targeted for attacks.
Output:

Conclusion
DNS footprinting is a vital step in the reconnaissance phase of ethical hacking. It allows you to map out a target’s DNS infrastructure and gather valuable insights that may lead to discovering vulnerabilities.
CEH v13 AI with InfosecTrain
Enroll in InfosecTrain‘s CEH v13 AI certification training course that provides individuals with a comprehensive understanding of ethical hacking, with a particular focus on key techniques such as DNS footprinting. Through hands-on training, participants will gain practical expertise in identifying and analyzing domain names, IP addresses, and network infrastructures. By mastering the steps of effective DNS footprinting and other essential tools, participants will be well-prepared to identify and mitigate security risks in real-world scenarios.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 11-May-2025 | 28-Jun-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 31-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 07-Jun-2025 | 13-Jul-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 21-Jun-2025 | 27-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |


 1800-843-7890 (India)
1800-843-7890 (India)