Identity and Access Management (IAM) in Cloud Security
As more businesses embrace cloud computing, concerns surrounding data security and unauthorized access have escalated. While cloud technology provides manifold benefits, such as accessibility, scalability, cost-efficiency, and environmental sustainability, it also presents new cybersecurity challenges. Among these challenges, safeguarding sensitive information from unauthorized access and maintaining the integrity of user identities has become crucial. This is where IAM, or Identity and Access Management, steps up as a crucial cornerstone of cloud security.

Crucial Role of IAM in Cloud Security
IAM is a crucial security framework that manages and controls user identities and access to systems, applications, and data in the cloud environment. Its primary objective is to allow authorized individuals to access the necessary resources while preventing unauthorized access or data leaks. IAM solutions encompass various processes, technologies, and policies that address the multifaceted aspects of cloud security.
Key Components of IAM in Cloud Security
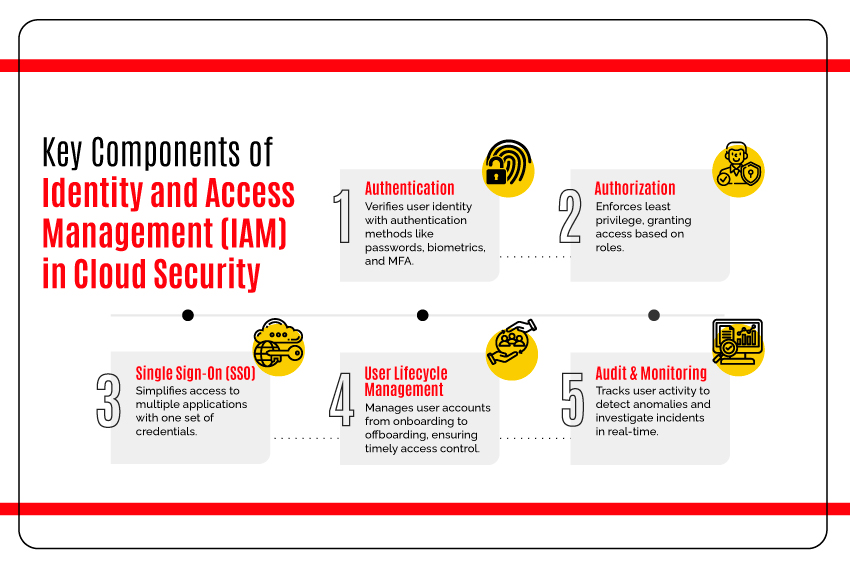
- Authentication: IAM uses various authentication methods, from traditional passwords to cutting-edge biometrics and Multi-factor Authentication (MFA), to verify the user’s identity when accessing cloud resources.
- Authorization: After the user has been successfully authenticated, IAM guarantees that access to resources is provided according to their roles, adhering to the least privilege principle. It minimizes breach impact by restricting unnecessary access.
- Single Sign-On (SSO): SSO enables users to log into multiple applications and services with a single set of credentials. It enhances user convenience and reduces the risk of password-related vulnerabilities.
- User Lifecycle Management: IAM solutions facilitate the efficient management of user accounts throughout their lifecycle, from onboarding to offboarding. It ensures access is only granted when necessary and promptly removed when no longer needed.
- Audit and Monitoring: IAM solutions offer robust auditing and monitoring capabilities, allowing organizations to track user activity, identify anomalies, and promptly investigate potential security incidents in real-time.
Benefits of IAM in Cloud Security
Here are some benefits of Identity and Access Management (IAM) in Cloud Security:
- Enhanced Security: It protects against insider threats, unauthorized access, and data breaches by enforcing strict access controls and authentication mechanisms.
- Reduced Attack Surface: It reduces the attack surface by minimizing the potential entry points for malicious actors or hackers.
- Efficiency and Productivity: It simplifies user access management, reducing the administrative load and guaranteeing that employees possess the necessary access to perform their tasks effectively.
- Centralized Management: It offers a centralized dashboard for managing user identity and access across various cloud services, facilitating the administration process.
- Reduced Insider Threats: It minimizes the limiting of insider threats by restricting user privileges to only what is necessary for their roles. It reduces the likelihood of unauthorized activities by employees, contractors, or partners.
- Regulatory Compliance: Many industries are bound by strict compliance regulations. IAM aids organizations in maintaining compliance by providing tools to manage user access, authorization, and audits.
How Can InfosecTrain Help?
At InfosecTrain, we offer a range of cloud security certification and training programs, including Cloud Security Practitioner, CCSK Foundation, CCSE, and CCSP. These courses cover various aspects of IAM in cloud security, giving individuals and organizations a comprehensive understanding of this area. Our experienced instructors with a deep knowledge of IAM and cloud security will provide the training. Their expertise can help clarify complex topics and provide real-world insights to enhance participants’ understanding.
We also offer the Cloud Security Expert Combo training course, which teaches various cloud security skills, best practices, and strategies to integrate cloud security tools effectively across diverse cloud infrastructures.


 1800-843-7890 (India)
1800-843-7890 (India)