Virus: Understanding the Key Concepts
Malicious software, often referred to as malware, poses a major risk to computers and networks around the globe. Viruses are among the most common and notorious threats to our cyber world. While viruses might seem like a complex technical topic, it’s important for everyone to have a basic understanding of what they are and how they work. After all, being aware of the enemy is the first step in defending against it, right?

To understand virus’s threats, it’s crucial to grasp how they work, their different phases, and the techniques they use to evade detection. That’s where the Certified Ethical Hacker (CEH) Module 7 subsection: Virus concepts come in. This subsection of CEH module 7 dives deep into the world of viruses, introducing the fundamental concepts and dissecting their operational phases and inner workings.
Concept of Virus
A computer virus (Vital Information Resources Under Siege) is a form of malicious software that is created to copy itself and move from one computer to another, typically without the user’s awareness or permission. These self-replicating programs latch onto executable files like documents, applications, or system files, primarily to inflict damage or disrupt the usual functioning of a computer.
The term “virus” is derived from the biological analogy of a virus that infects living organisms. Just like their biological counterparts, computer viruses are parasitic in nature, relying on host files or programs to propagate and carry out their malicious activities. Viruses typically follow a specific life cycle:
- Design: This is where the virus is conceived and created by its author using programming languages or specialized virus construction toolkits. It’s like an evil scientist cooking up a nefarious plan in their secret lab.
- Replication: During this stage, the virus quietly makes copies of itself and spreads its code within the infected system, lying low and multiplying before making its presence known. Think of it as a silent invasion, with the virus replicating and fortifying its position.
- Launch: This is when the real trouble begins. The virus becomes active and starts executing its malicious payload, often triggered by an unsuspecting user running an infected program or file. It’s like the evil virus finally revealing itself and unleashing its sinister plan.
- Detection: At this point, security systems and antivirus programs raise the alarm, identifying the virus as a threat and marking it as harmful to the system. It’s like the good guys finally catching on to the virus’s tricks and sounding the alarm bells.
- Incorporation: Once the virus is detected, antivirus developers swing into action, analyzing the threat and integrating new defenses into their software to protect against it. This is like the security team developing a specialized antidote or countermeasure to neutralize the virus.
- Execution of the Damage Routine: In this final stage, users update their antivirus software with the latest definitions, allowing it to detect and remove the virus from their systems, effectively stopping its harmful effects in its tracks. It’s like the good guys deploying their antidote and squashing the evil virus once and for all (at least until the next one comes along).
Types of Viruses

Working Process of Virus
Viruses have two phases to execute an attack: The infection phase and the attack phase.
Infection Phase
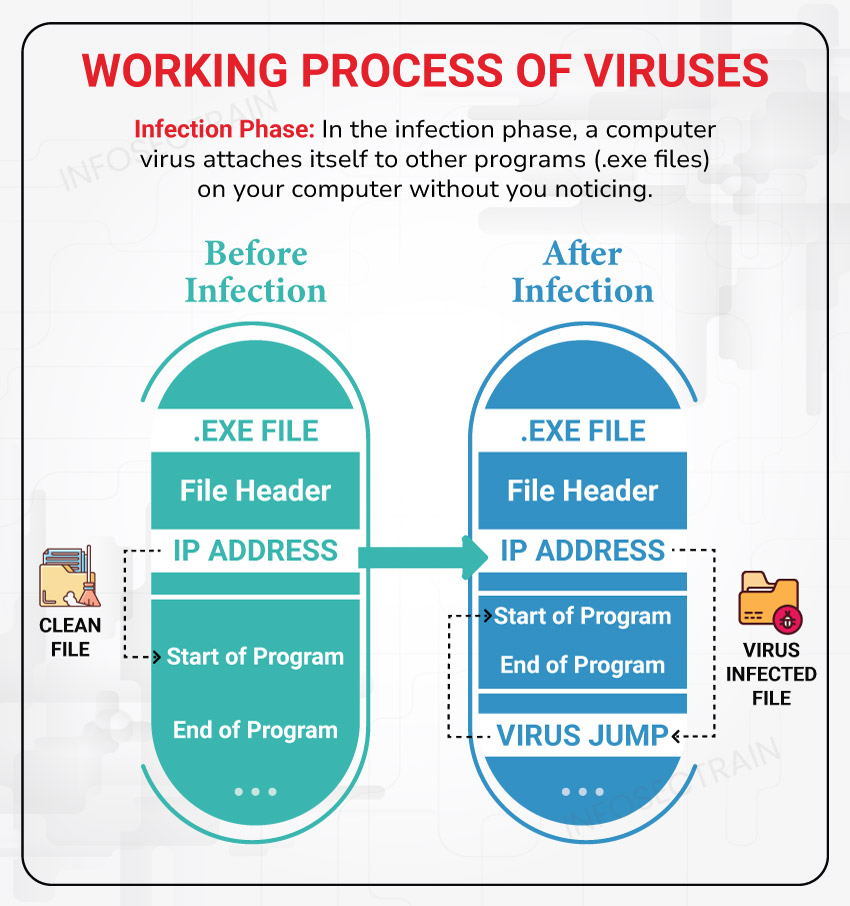
In the infection phase, a computer virus attaches itself to other programs on your computer without you noticing. It’s like a sneaky passenger hitching a ride. The most important factors in the infection phase are:
- Method of infection
- Method of spreading
Once a program is infected by a virus, it can infect other programs on the computer. This cycle continues until the user notices something is wrong with the system.
Sequence of Infection:
- A virus begins by loading itself into the computer’s memory and looks for any executable programs stored on the hard drive.
- It then secretly adds malicious code to a legitimate program without the user’s knowledge.
- The user, unaware that the program has been tampered with, starts the program and activates the virus.
Most Common Methods to Spread Virus
- Infected Files: A virus can hide in different types of files. When someone opens these files, their computer gets infected.
- File-Sharing Services: Viruses can spread through online file-sharing platforms. If someone downloads and opens an infected file from these services, their computer could get infected.
- Hard Drives and Storage Media: If you use an infected DVD, USB drive, or external hard disk on your computer, the virus from these devices can spread to your system.
- Malicious Attachments and Downloads: Viruses can be hidden in email attachments or in apps downloaded from untrustworthy sources. Opening these attachments or installing these apps can infect your computer.
Attack Phase

After spreading throughout a computer, viruses begin damaging files and programs. They only start causing harm after a specific trigger event occurs. Some viruses can even copy themselves and perform actions like deleting files or making the computer run slower. These viruses typically carry out the harmful activities they were designed for by their creators. Common actions include:
- Deleting files or changing data, which slows down the computer.
- Doing unusual tasks, such as playing music or displaying animations, that aren’t related to any applications you’re using.
Characteristics and Purpose of Viruses
Characteristics:
- Self-Replicating: Viruses are designed to replicate themselves by attaching their malicious code to other programs or files on a computer system. This allows them to spread rapidly.
- Host Dependency: Viruses cannot propagate on their own. They require a host file or program to latch onto to execute and replicate.
- Payload Delivery: Most viruses contain a particular payload or malicious code intended to cause harm, such as deleting files, corrupting data, or providing unauthorized access.
- Stealth Techniques: Advanced viruses employ stealth techniques to evade detection by antivirus software and conceal their activities from users.
- Polymorphic Nature: Some viruses use polymorphic code that mutates with each iteration, making it harder for antivirus programs to detect them based on signatures.
Purposes:
- Causing Disruption: Many viruses are created with the sole purpose of causing chaos, deleting data, or disrupting normal system operations, often for malicious fun or revenge.
- Financial Gain: Some viruses are designed to steal sensitive information like passwords or financial data for monetary gain or corporate espionage.
- Demonstrating Skills: In some cases, virus creators develop viruses to demonstrate their programming skills or to challenge security measures.
- Political/Ideological Motives: Viruses can also be created to spread political or ideological messages or to target specific organizations or individuals.
- Building Botnets: Viruses are sometimes used to turn infected systems into bots, which can then be controlled remotely as part of a larger botnet for carrying out distributed attacks or other malicious activities.
To be continued…
Computer Worms: Understanding Fundamental Concept
CEH with InfosecTrain
Ethical hacking is a complex and demanding field that requires a thorough understanding of cybersecurity. Enrolling in courses like the Certified Ethical Hacker program at InfosecTrain enables learners to enhance their skills in assessing security and optimizing network systems. This training equips participants with the expertise and knowledge needed to help organizations effectively bolster their security measures. Join InfosecTrain’s CEH training to become a leading professional in protecting sensitive information.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 11-May-2025 | 28-Jun-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Close ] | |
| 31-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 07-Jun-2025 | 13-Jul-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 21-Jun-2025 | 27-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 06-Jul-2025 | 16-Aug-2025 | 09:00 - 23:00 IST | Weekend | Online | [ Open ] |


 1800-843-7890 (India)
1800-843-7890 (India)