Fundamental Security Concepts
In the cybersecurity domain, establishing a robust foundation is paramount. CompTIA Security+ offers an extensive framework for understanding the core principles that underpin a robust security posture. Domain 1.2 of this certification specifically focuses on “Fundamental Security Concepts”, serving as the cornerstone for aspiring security professionals.

This article helps you understand these core concepts of security. It will explore the principles that are the foundation of a strong security posture. We will break down the complexities of security controls, risk management, and mitigation techniques, ensuring you understand the essential knowledge required to safeguard digital assets.
1.2 Summarize Fundamental Security Concepts
Fundamental security concepts are an essential topic that introduces the core principles and practices vital for safeguarding information and resources in the digital world. This section encompasses a range of concepts, including:
1. Confidentiality, Integrity, and Availability (CIA): These are the three core information security principles.
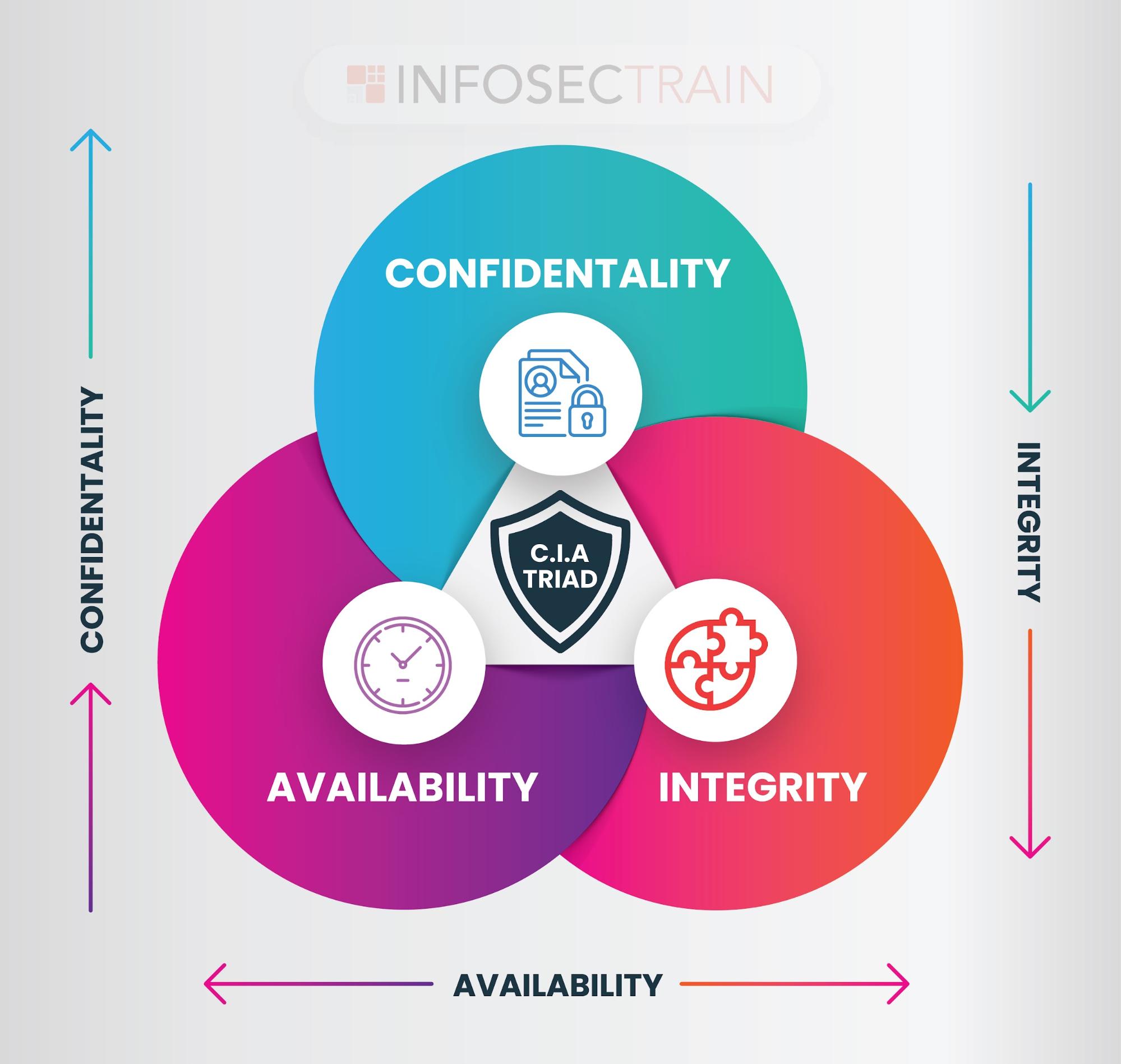
- Confidentiality: Ensuring that data is not shared with unauthorized people.
- Integrity: Assuring the accuracy and reliability of data. An example is using checksums or hashes to detect unauthorized changes to data.
- Availability: Ensuring that authorized users have reliable access to information and resources when needed. An example is having redundant systems to prevent downtime.
2. Non-Repudiation: This security principle ensures that a party in a transaction cannot deny the authenticity of their signature on a message that they sent, ensuring accountability and traceability.
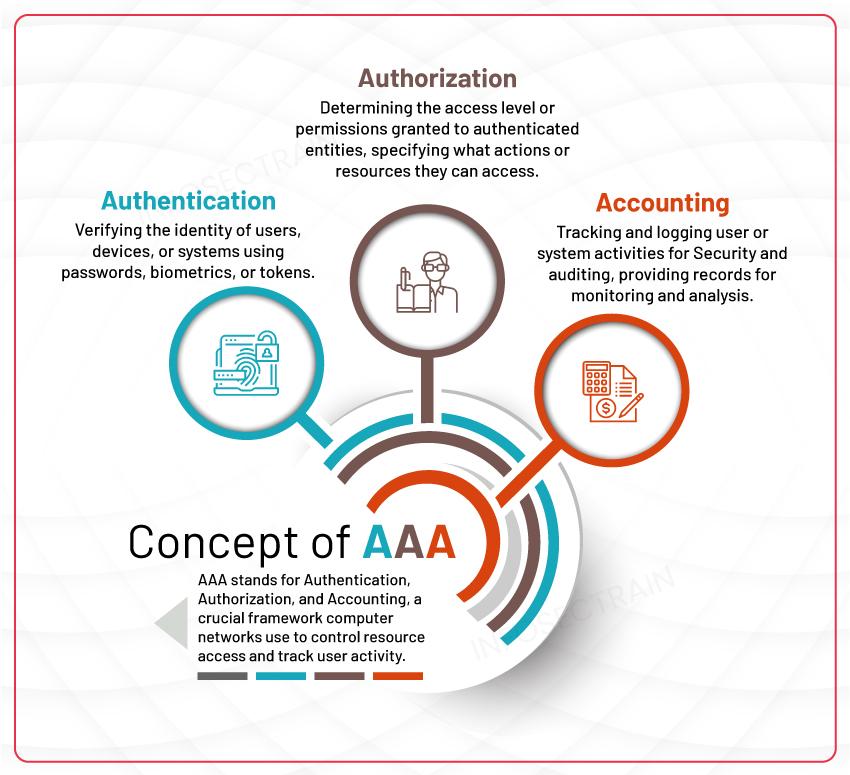
3. Authentication, Authorization, and Accounting (AAA): These are the processes that control access to resources:
4. Gap Analysis: This is a method of assessing the differences between the current security posture and the desired state, helping to identify necessary improvements. For example, comparing current security measures with industry best practices to identify areas for improvement.
5. Zero Trust: This security model emphasizes the necessity of verification for all individuals attempting to access network resources and advises against assuming trust without proper authentication. Key components include:
Control Plane:
- Adaptive Identity: The ability to adjust user access based on context.
- Threat Scope Reduction: Techniques to limit the potential impact of threats.
- Policy-Driven Access Control: Access permissions defined by policies.
- Policy Administrator: The person or role responsible for policy management.
- Policy Engine: The system that processes and enforces security policies.
Data Plane:
- Implicit Trust Zones: Areas within the network where certain trust levels are assumed.
- Subject/System: The entity requesting access to a resource.
- Policy Enforcement Point: The location where access decisions are enforced.
6. Physical Security: This is an essential aspect of an overall security strategy, which protects the organization’s physical assets. It encompasses measures to deny unauthorized access to facilities, equipment, and resources, safeguarding individuals and assets from potential harm or damage.
- Bollards: Sturdy posts used to prevent vehicle access
- Access Control Vestibule: A small entrance room that allows for secure access control
- Fencing: Barriers used to protect an area
- Video Surveillance: Cameras that are utilized to monitor and record activities
- Security Guard: Personnel tasked with protecting a facility
- Access Badge: Identification used to gain physical access to a building
- Lighting: Illumination to deter unauthorized access or activities
- Sensors: Sensors are listed as tools used in physical security systems:
- Infrared: Detects infrared energy (heat) emitted by objects; used in security systems to detect temperature variations indicating presence.
- Pressure: Identifies weight or force on a surface; used in floor mats to detect presence by pressure exertion.
- Microwave: Emits microwave waves and measures their reflection off moving objects; widely used for motion detection.
- Ultrasonic: Emits ultrasonic waves and listens for echoes to detect motion or measure distance to objects.
7. Deception and Disruption Technology: This category includes tools and techniques designed to deceive, mislead, or disrupt the operations of malicious actors:
- Honeypot: Security setup to detect and deflect unauthorized system use. It appears to be part of a network but is isolated and monitored to lure and analyze attackers.
- Honeynet: A network intentionally made vulnerable to attacks for studying attacker’s methods, often comprising one or more honeypots to enhance network security.
- Honeyfile: A decoy file used to bait cyber attackers; accessing it triggers an alert, signaling a potential attack, allowing swift response from security teams.
- Honeytoken: A digital or non-digital decoy that is used to detect and counter unauthorized use of information systems.
Conclusion
CompTIA Security+ (SY0-701) section “Fundamental Security Concepts” is not just about learning security concepts; it is about understanding the principles shaping your approach to protecting digital assets. Whether you are preparing for the Security+ exam or looking to strengthen your organization’s security posture, these fundamental concepts are your starting blocks in the ever-evolving race against cyber threats.
Master CompTIA Security+ with InfosecTrain
You can check and enroll in InfosecTrain’s CompTIA Security+ certification training course. Our course provides a comprehensive understanding of security concepts, emphasizing the practical skills needed to tackle security threats, manage risks, and ensure the confidentiality, integrity, and availability of information. Under the guidance of our experienced trainers, you will understand the latest security vulnerabilities, technologies, regulations, and practices.
TRAINING CALENDAR of Upcoming Batches For Security+ SY0-701
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 30-Mar-2025 | 10-May-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 12-Apr-2025 | 25-May-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |


 1800-843-7890 (India)
1800-843-7890 (India) 