A Comprehensive Guide to IoT Security
The Internet of Things (IoTs) has seamlessly integrated into our everyday routines, from smart home gadgets, wearable devices, industrial equipment, and even urban infrastructure. As more devices are interconnected to the network, it becomes increasingly crucial to have strong security measures in place. In this blog post, we will look into the complexities of IoTs, the approaches required to safeguard digital and physical assets, and future trends and advancements.

Table of Contents
What is IoT?
Common IoT Security Threats and Vulnerabilities
Best Practices for Securing IoT Devices and Networks
Future Trends in IoT Security
What is IoT?

The Internet of Things (IoTs) is the interconnected network of physical devices embedded with softwares, sensors, and other technologies that enable them to connect and share data or information with other devices and systems via the Internet. These devices can be as basic as sensors or smart home appliances, or as advanced as industrial machinery and infrastructure components. The importance of IoT lies in its ability to enhance operational efficiency, improve real-time decision-making, increase automation, and facilitate data-driven insights across various industries and personal applications.
Common IoT Security Threats and Vulnerabilities
Here are some of the most prevalent security threats and vulnerabilities in IoT:
- Default Settings: Many devices come with default usernames and passwords that are often easy to guess and widely known, making them easy targets for attackers.
- Insecure Networks: IoT devices often connect over insecure networks, exposing them to potential interception and unauthorized access.
- Software Updates: Many IoT devices cannot be patched or updated, leaving known vulnerabilities unaddressed.
- Lack of Encryption: Data transmitted across IoT devices may not always be encrypted, exposing sensitive information to interception.
- Insecure Interfaces: Weaknesses in user interfaces, such as unsecured web management interfaces, can allow attackers to access devices easily.
- Data Privacy Issues: As devices continue to gather personal information, there is serious concern about privacy breaches if the data is not handled properly or accessed illegally.
Best Practices for Securing IoT Devices and Networks
Securing IoT devices and networks is vital to prevent unauthorized access and protect data integrity. Here are some IoT security best practices:
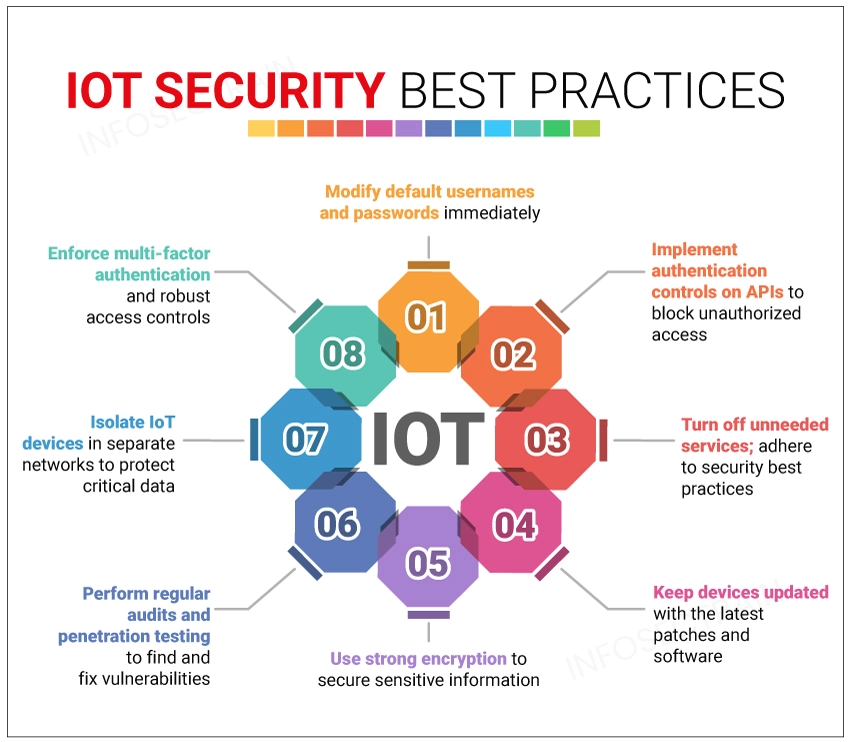
- Change Default Credentials: Always change default usernames and passwords before deploying devices in the network.
- Secure APIs: Ensure that any Application Programming Interface (API) connected to IoT devices are secure and have authentication controls to prevent unauthorized access.
- Secure Device Configuration: Disable unnecessary services on devices and configure security settings according to industry best practices to minimize vulnerabilities.
- Regular Updates and Patch Management: Ensure IoT devices are regularly up-to-date with the latest firmware and software patches.
- Use Strong Encryption: Encrypt data in transit and at rest to secure sensitive information from being intercepted.
- Regular Security Audits: Conduct regular security assessments and audits to identify and remediate vulnerabilities. It includes IoT penetration testing and the use of vulnerability scanners.
- Network Segmentation: Segment IoT devices into separate networks, isolating them from critical network resources.
- Implement Strong Authentication: Use multi-factor authentication and robust authorization protocols to control access to IoT devices.
Future Trends in IoT Security
As technology evolves, so do the approaches to securing it. Here are some anticipated trends in IoT security:
- AI Integration: AI can proactively identify and respond to security threats by analyzing data patterns, enhancing the predictive capabilities of IoT security.
- The Role of 5G Networks: 5G networks provide faster speed, greater connectivity, and lower latency, enabling more efficient and responsive IoT applications and pushing the boundaries of device interconnectivity.
- Edge Computing: Moving data processing to the outermost edge of networks reduces latency and bandwidth use and enhances security by minimizing data transmission.
- AR and VR Integration: Augmented Reality (AR) and Virtual Reality (VR) integration into IoT systems can enhance user interfaces and operations, necessitating robust security frameworks to protect sensitive data and interactions.
- Blockchain Integration: Utilizing blockchain technology in IoT can decentralize data management, create tamper-resistant records, and improve the integrity and confidentiality of data exchanges.
- Zero Trust Architectures: Adopting zero trust principles ensures all devices and users are verified before granting access to IoT networks, significantly reducing the potential attack surface.
- Development of IoT Security Standards: Establishing and adopting global security standards for IoT devices and ecosystems can ensure consistent security measures and facilitate safer and more reliable connectivity.
IoT security is a dynamic field that requires continuous attention and adaptation. As technology evolves, so will the strategies needed to secure it. Individuals and organizations can protect their devices and data from potential breaches by staying informed about the latest security threats and best practices.
Related Articles:
- Role of an Ethical Hacker in Protecting IoT Devices
- Privacy in the Internet of Things (IoTs) Era
- What is IoT Penetration Testing?
How Can InfosecTrain Help?
At InfosecTrain, we offer comprehensive training courses such as Certified Ethical Hacker (CEH) and CompTIA PenTest+ that provide valuable insights into safeguarding IoT devices from intricate cyberattacks. These courses offer hands-on experience and practical knowledge, equipping participants with the skills to identify vulnerabilities, conduct penetration tests, and implement robust security measures in IoT environments. You can join InfosecTrain to get thorough knowledge of these certifications under the guidance of our experienced instructors. We also offer Pentester combo training and other security testing courses that can help you improve your skills.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status |
|---|







 1800-843-7890 (India)
1800-843-7890 (India)