A Guide to Protect Yourself From Ransomware Attacks
Ransomware can be compared to kidnapping where someone who is close to you is abducted and is threatened to be only released once a ransom amount is paid to the abductors. However, in this case, rather than abducting a person, the attackers/ hackers instead lock your systems so that you can not use your data and then proceed to demand money to release your data.

Paying the ransom to recover your access to the files is no assurance that your data will be actually returned. The attackers may continue to demand additional money or refuse to release your data in any case. Given the predominance of Ransomware and how difficult it may be to deal with, it’s best to avoid it entirely.
And the biggest scam in recent times is that Cyber Criminals are ganging up to share ideas, tools, and intelligence to target big organizations.
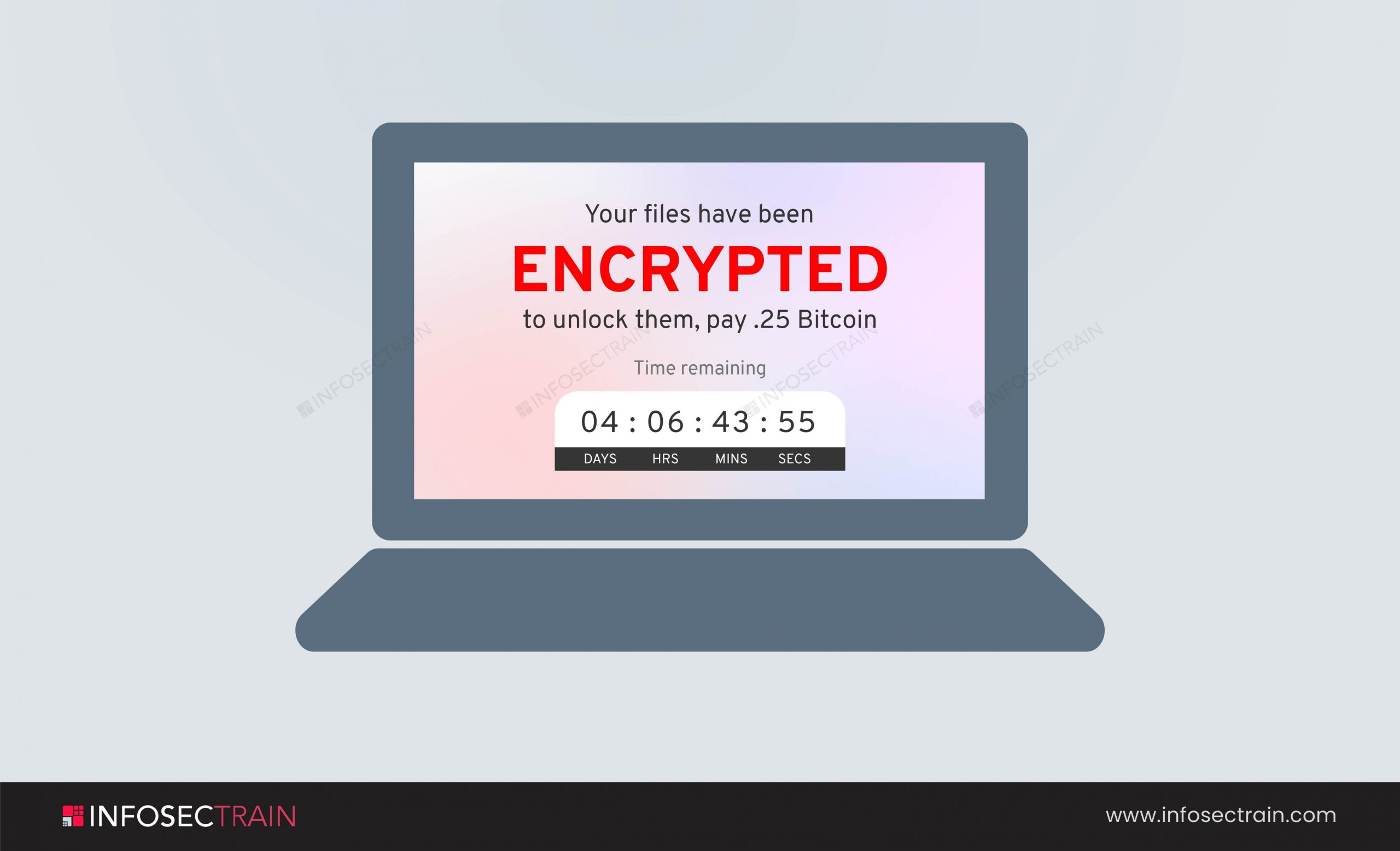
As you can view in the picture, the attacker locked the system and demanded .25 Bitcoin. And the time they gave to send the money is 4 days 6hours. So this is how you see the message of a ransomware attacker.
Fortunately, there are some steps to avoid Ransomware. In this blog, you are going to witness some of them. Let us dive into the topic:
1. Search for decryption tools: If you are already facing this problem, browse for the decryption tools. “NO MORE RANSOM!” is a project developed by law enforcement and various security companies in which you will find many decryption keys for multiple versions of Ransomware.
2. Backup: Backing up your data is always a better idea. This step not only helps you when your system is encrypted, but it also helps you in the following situations:
- Sometimes you may delete your data accidentally.
- Your system may crash.
At that time, having the Backup data is very useful. If you have backed up your data, you need not to pay ransom to anyone. All you have to do is avoid ransomware messages and restore your data.
3. Multi-Factor Authentication: MFA is a method where the user can access the files only after undergoing two or more authentication processes. The authentication evidence may be in the form of soft-token, hard-token, or an SMS code called One Time Password (OTP). In this case, as the attacker cannot have your physical devices with him to check the SMS or soft-token, you don’t need to worry about the system’s security failing to keep up.
4. Filter and scan emails before they reach your staff and users: Staff should not open phishing and ransomware emails, which can happen if they arrive in their inboxes. Content scanning and email filtering will take care of many phishing and ransomware scams before they can reach staff.
5. Be careful of what you click: Sometimes, it isn’t easy to protect yourself from Ransomware because it depends on your behavior over the internet. It would be best if you were very careful while clicking ads, spam Email links, social media messages. In my opinion, it is best if you do not respond to the Emails, links, or social media messages of an unknown source.
6. Use robust security: Using Antivirus Software can help you prevent some ransomware variants, but you have to run frequent scans to check for any common threats. And if you have already faced the problem and are trying to backup your data, make sure the system is clean after the attack. You can check your system by using Security software.
7. Update your software: Hackers or attackers mostly try to attack the outdated versions of software because the security measures in the outdated software may not be able to prevent the modern attacks. As they say, modern problems need modern solutions. So keep your systems, software, and mobile applications updated.
8. Use the Least Privilege method: Give people just the privileges they need to accomplish their tasks to reduce the chance of attackers getting access to key systems or sensitive data. IAM controls can assist you in granting the least privileged access based on who is seeking it, the context of the request, and the hazard of the access environment.
9. Update yourself about the latest threat intelligence: Keeping up with the most recent threat intelligence allows you to notice an attack fast, respond effectively, and stop it from spreading. Threat intelligence can also assist you in determining the origins of some attacks and use that knowledge to restrict incoming traffic at the firewall.
10. Train your employees: Offer the latest security awareness training to ensure that your workers use good cyber hygiene habits on all devices, such as strong passwords and secure Wi-Fi connections, and assist them in detecting and responding to the latest phishing methods.
About InfosecTrain:
InfosecTrain is one of the leading training providers with a pocket-friendly budget. So, if you want to get a good grip on the various Security courses, then join us to experience an incredible journey with our industry experts. Our courses are available in live instructor-led and self-paced sessions, making it easy for you to take up and complete your learning/ training journey at ease. Join InfosecTrain to learn skills that can change your life.






 1800-843-7890 (India)
1800-843-7890 (India)