Active Attack vs. Passive Attack
Active attacks and passive attacks are two different types of attacks that relate to computer security, network security, information security, and more. Both pose significant security risks to computer networks, information systems, and web applications and can be used by hackers or malicious actors to compromise security and gain unauthorized access to systems or data. Dealing with active and passive attacks can be challenging for every organization, regardless of size or industry. Therefore, organizations need to be aware of these types of attacks and take appropriate security measures to protect against them. These measures include firewalls, encryption, intrusion detection and prevention systems, and regular security audits and updates.
In this article, we will cover active and passive attacks, two of the most common forms of security attacks, and the differences between the two.
Table of Contents
What is an active attack?
Types of active attacks
What is a passive attack?
Types of passive attacks
Differences between active attack and passive attack
What is an active attack?
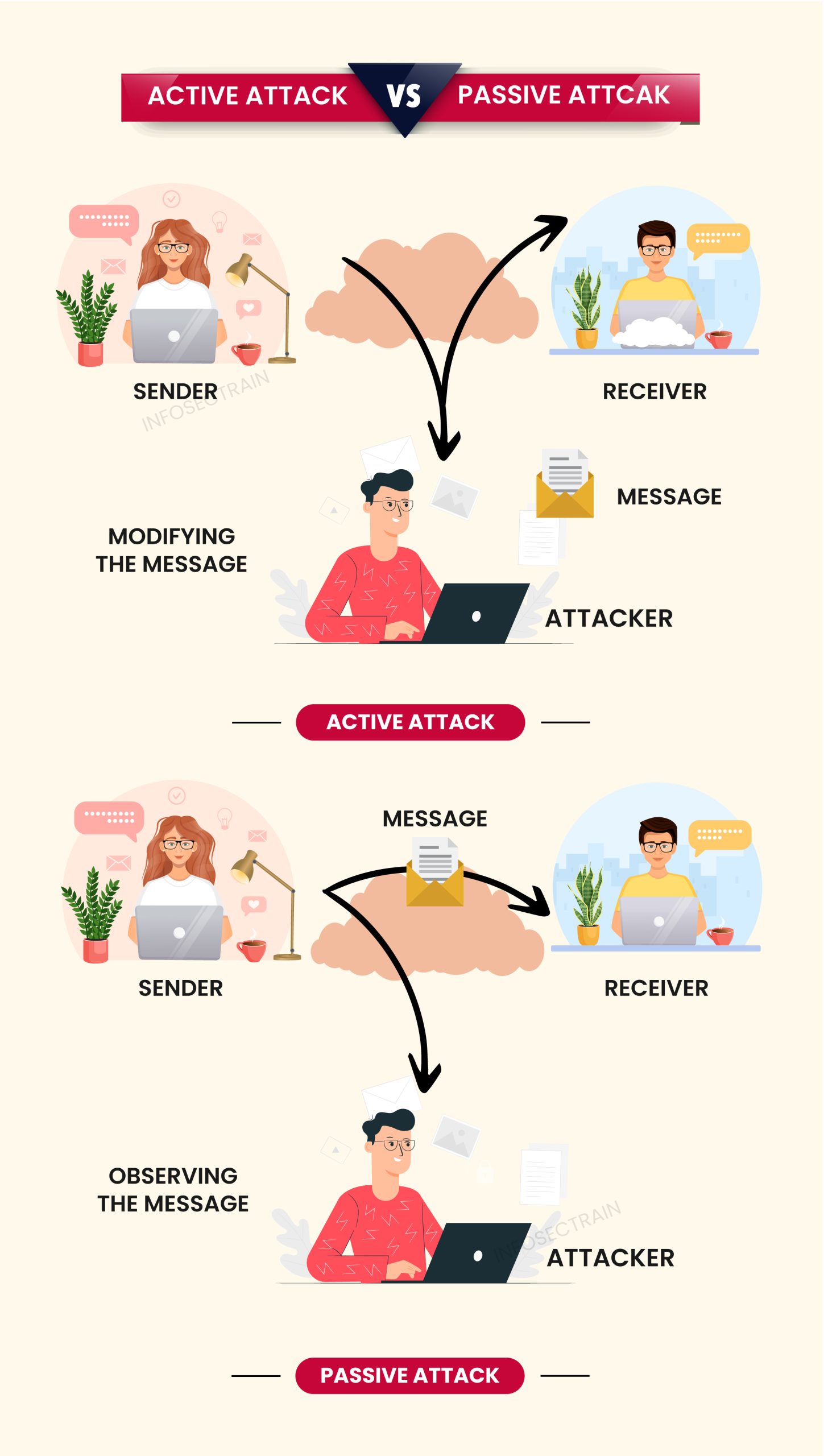
An active attack is a security attack in which the attacker directly communicates with the target system or network. In this attack, an attacker attempts to modify or disrupt the system or network’s functioning by injecting malicious traffic or executing unauthorized commands. It can be dangerous to the integrity and availability of a system or network. It can compromise the data integrity and reduce the availability of system resources, leading to significant damage and financial loss for the targeted organization.
Types of active attacks:
Active attacks can take many forms, including:
- Distributed Denial of Service (DDoS) attack: In this attack, the attacker uses a network of compromised devices known as a botnet to flood a target system or network with excessive traffic causing it to crash or become unavailable.
- Masquerade attack: In this attack, the attacker pretends to be a legitimate user or system to gain unauthorized access to confidential information or perform malicious actions.
- Session hijacking: In this attack, the attacker takes over a user’s session by stealing their session ID, which can be used to impersonate the user and perform actions on their behalf.
- Replay attack: In this attack, the attacker intercepts and records data packets transmitted between two parties and later replays them to gain unauthorized access to a system or network.
What is a passive attack?
A passive attack is also a type of security attack in which an attacker is in indirect contact with the target system or network and monitors the communication between the target system. In this attack, an attacker monitors, intercepts, or eavesdrops on data transmissions without altering or affecting them. The main objective of a passive attack is to gain unauthorized access to sensitive or confidential data or information without being detected. They are often difficult to discover as they do not disrupt system operations or modify data.
Types of passive attacks:
Passive attacks can take many forms, including:
- Release of message contents: In this attack, the attacker can intercept and view the content of a message being transmitted over a network and use this information for malicious purposes.
- Traffic analysis: In this attack, the attacker can monitor the traffic between two or more communication nodes to obtain information about the communication patterns and behavior of the system.
- Network mapping: In this attack, the attacker creates a network map by monitoring the network traffic and identifying the communication patterns between different devices on the network.
- Sniffing: In this attack, the attacker captures and analyzes network traffic to intercept sensitive data such as login details, credit card numbers, or other confidential information.
Differences between active attack and passive attack:
Here are the differences between active attacks and passive attacks:
| Parameters | Active attack | Passive attack |
| Objective | Obtain unauthorized access to a network or system and cause damage or gain sensitive information. | Obtain confidential information or monitor system behavior without being detected. |
| Effect | It can have severe consequences, such as data theft, loss of sensitive information, and system downtime. | It can have serious consequences, such as data leakage, unauthorized access to sensitive information, and loss of privacy. |
| System resources | The attacker may consume or modify system resources, potentially causing system failure or data loss. | The attacker only monitors and collects data; therefore, system resources are not directly affected or modified. |
| Duration | The duration of an active attack is likely to be shorter than a passive attack. | It may be carried out over an extended period to gather as much data as possible. |
| Detection | It can often be detected by monitoring network traffic for unusual patterns or behaviors, such as a sudden increase in traffic or unexpected traffic to unique destinations. | It can be more challenging to detect because they do not disrupt system operation. However, they can sometimes be detected by monitoring network traffic for suspicious patterns or anomalies. |
| Prevention | It can be mitigated using strong passwords, two-factor authentication, firewalls, intrusion detection/prevention systems, anti-malware software, security awareness training, and regular software updates and patching. | It can be mitigated using encryption, security protocols, network segmentation, monitoring and logging, access control, VPNs, and physical security measures. |
| Examples |
|
|
In conclusion, active attacks are more aggressive and involve a direct attempt to harm the target system or network, while passive attacks are more subtle and focus on gathering information without being detected.
Go to the video below for further information on how to defend your organization from cyberattacks.
How to start cyber security strategy in your organization step by step process
You can also refer to the related blogs:
- How to Protect Organizations from Cyberattacks?
- Top 5 Ways To Defeat Cyberattacks
- Importance of Information Security Programs for Businesses
How can InfosecTrain help?
Cybersecurity is a crucial aspect of our lives today as technology continues to evolve and is increasingly incorporated into our daily routines. With society’s growing dependency on technology, cybersecurity threats have become more prevalent and sophisticated, posing a significant risk to individuals, organizations, and governments.
Do you intend to start a career in cybersecurity? Enroll in InfosecTrain‘s various cybersecurity training courses with our experienced instructors. We will provide you with more practical knowledge on cybersecurity and information security, support you in accomplishing your goals, and help you achieve the most pertinent certifications, so you may move up the success ladder and closer to the level of success you seek.






 1800-843-7890 (India)
1800-843-7890 (India)