All About Network Protocols

What are Network Protocols?
A collection of rules, conventions, and data formats that govern how devices share data across networks is known as network protocols. In reality, without all these protocols, computer networks would not exist.
Let us first understand what is OSI Model before we deep dive into network protocols.
What is the OSI Model and How it Works?
OSI (Open Systems Interconnection) Model is a seven-layer conceptual structure that explains how a networking or telecom system works. The OSI Model illustrates how a network operates and specifies how networks interact with each other. All of the layers are self-contained, and the tasks that have been allocated to them can be accomplished on their own.
The seven layers of the OSI Model separate the communication mechanism between two network devices. Following the OSI Model, here is a diagram of the interaction of two network devices:
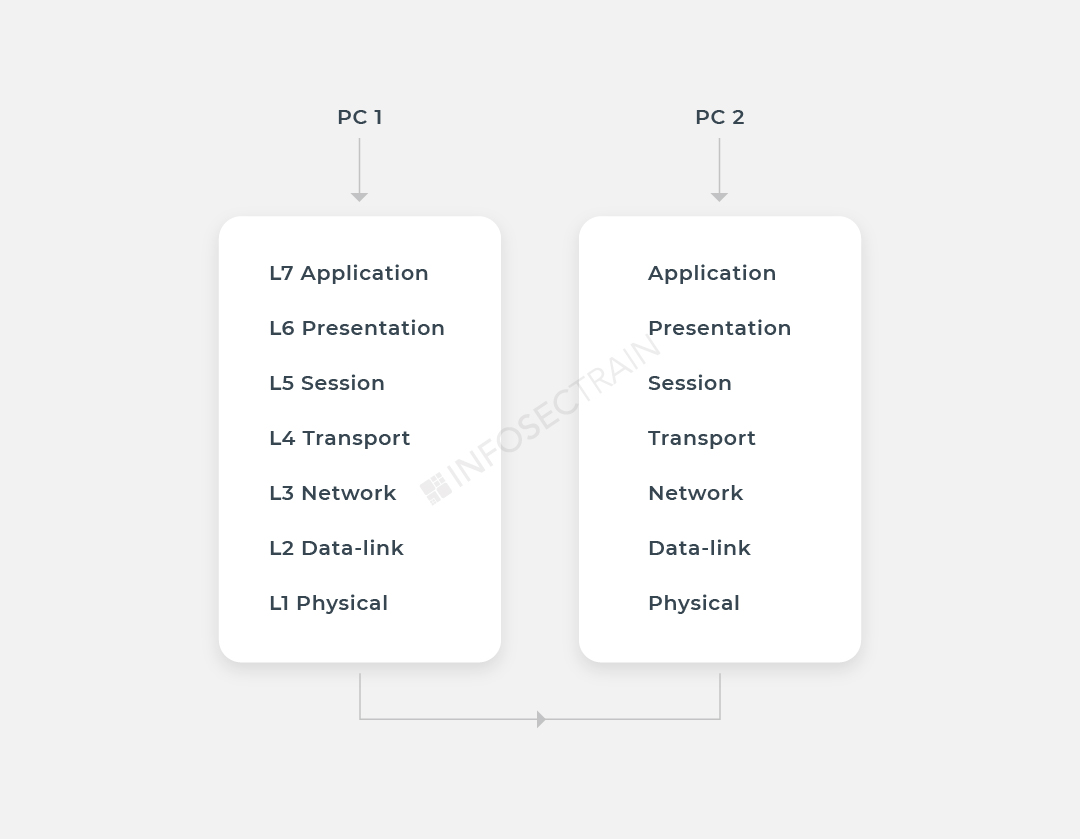
Network protocols separate the communication mechanism into separate tasks in every layer of the OSI Model. At each layer of the data exchange, one or more network protocols are in use.
Network Protocol Characterization
Now that you understand how the OSI model works, let’s jump into protocol classification. The protocols mentioned below are some of the most widely used in communication networks.
Application Layer Network Protocols
HTTP port No – 80
HTTPS port no – 443
Port no – 21 and 20
Telnet port no – 23
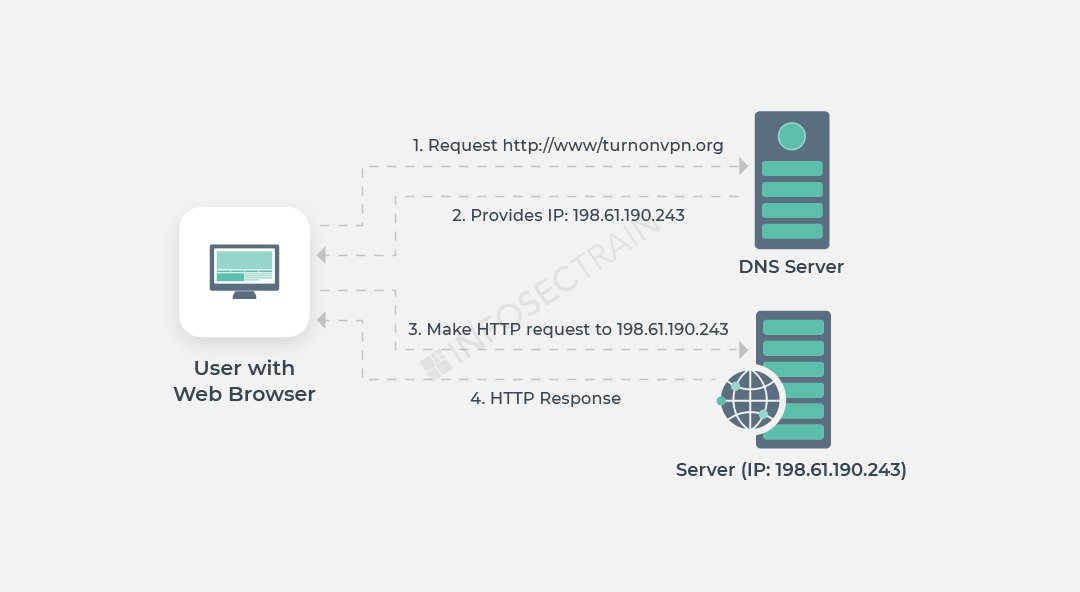
Every Internet-connected device has a unique IP address that other devices use to locate it. Humans are no longer needed to memorize IP addresses because of DNS servers.
(Example – www. Amazon.com to 192.0.2.44)
Port no – 53
APIPA (Automatic Private IP Addressing) is an acronym for Automatic Private IP Addressing (APIPA). When a DHCP (Dynamic Host Configuration Protocol) server is unavailable, it is a feature or attribute of operating systems (for example, Windows) that allows computers to automatically configure an IP address and subnet mask.
DHCP port no – 67, 68
A user can use SMTP to send an email to another user on the same network or some other network.
- Its installation is simple
- It will connect to any device without any limitations
- It does not require any further progress on your part
Port no – 25

Port no – 110
Port no – 143
Transport Layer Network Protocols
- TCP (Transmission Control Protocol): TCP is a transport layer protocol that provides a reliable stream delivery and virtual connection service to applications through the use of sequenced acknowledgment. TCP is a link-oriented protocol, which means that it needs to create a connection before data can be transferred. Its function is to transfer packets through the internet and ensure that data and messages are transmitted successfully across networks. During transmission, TCP dynamically divides data into packets. TCP has the ability to repair transmission errors. It will detect and restore packets that have been sent out of order.
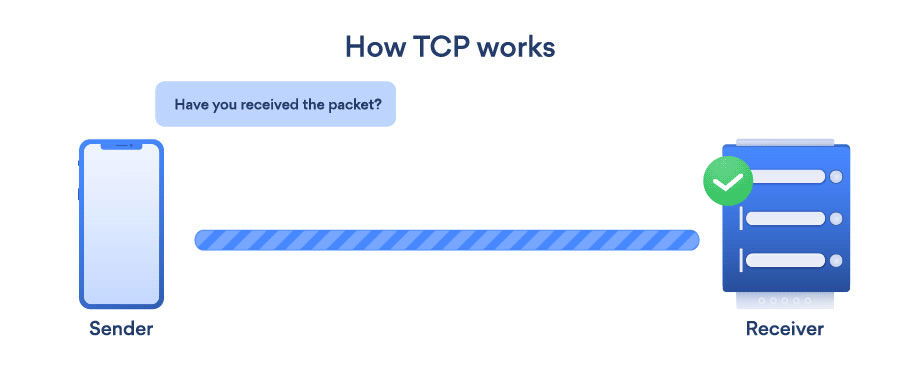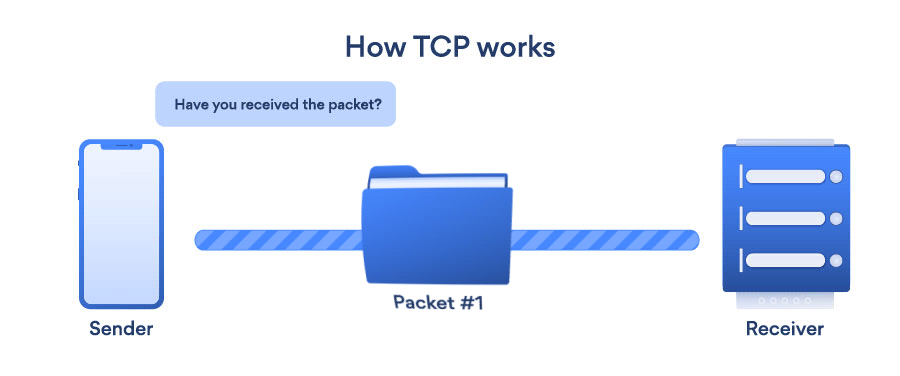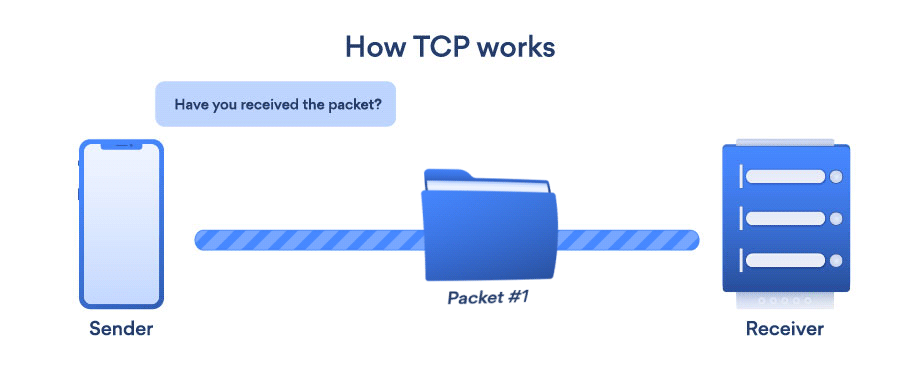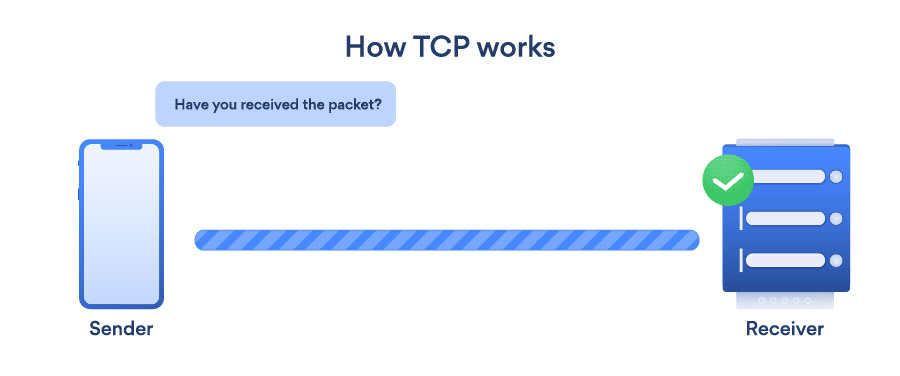
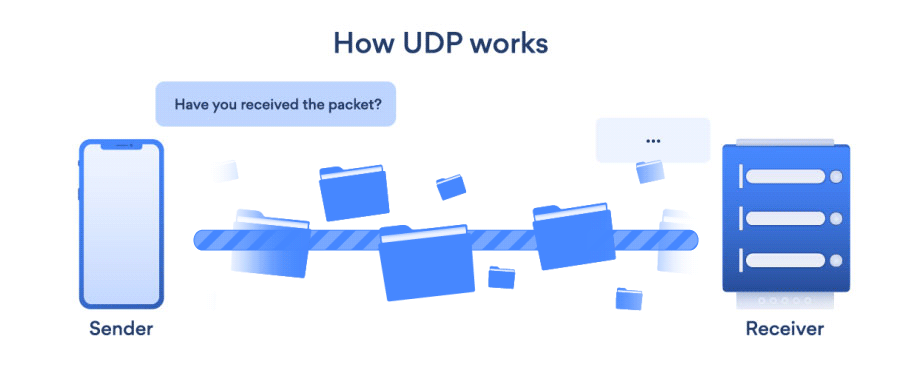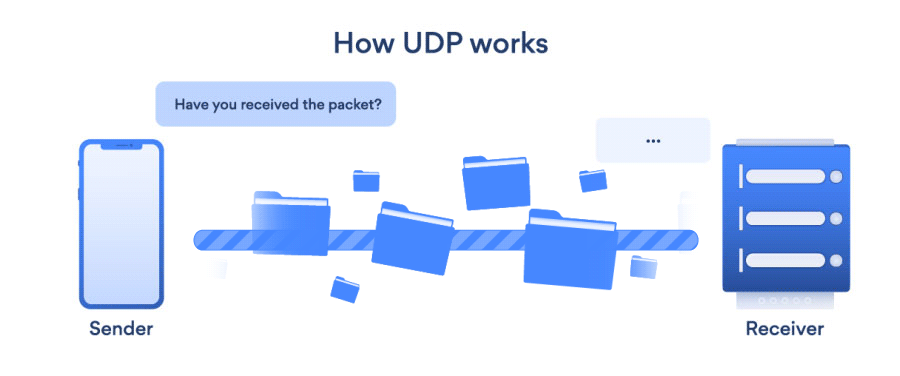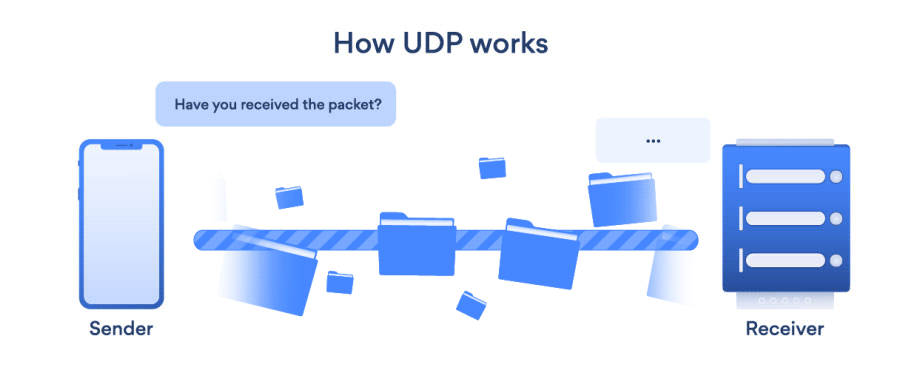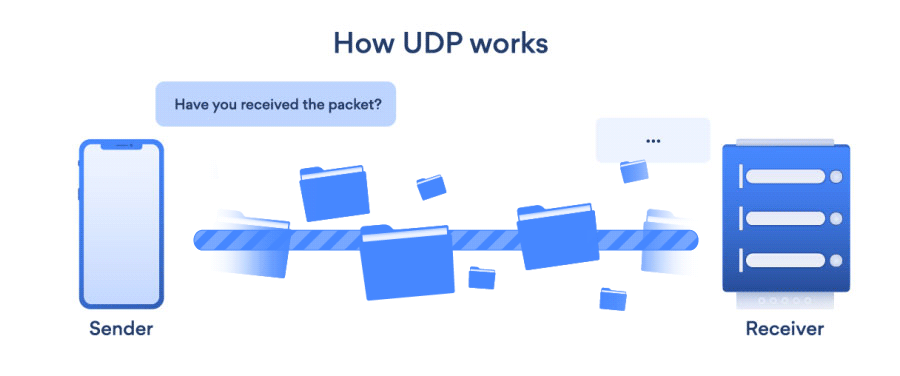
- UDP (User Datagram Protocol): UDP is a connectionless transport layer protocol that offers a clear and simple but unstable message service. Just as with TCP, UDP does not have any functions for stability, flow management, or error handling. When the stability mechanisms of TCP aren’t needed, UDP comes in useful. UDP does not allow for the retransmission of missing data packets.
- UDP allows for broadcast and multicast links.
- TCP is slower than UDP.
Learn Network+ with us
Infosec Train is a leading provider of IT security training. If you are interested and looking for live online training, Infosec Train provides the best online CompTIA Network+ Online Certification Training. The CompTIA Network+ examination training sessions will support candidates in better understanding the concepts in a short period of time.






 1800-843-7890 (India)
1800-843-7890 (India)