AWS CloudHSM vs. AWS KMS
In today’s cloud-centric world, where data breaches dominate headlines, data security has become crucial. Amazon Web Services (AWS) offers many services to ensure your data’s safety and integrity. The two most prominent solutions are AWS CloudHSM and AWS Key Management Service (KMS), offering distinct advantages and challenges. One provides the robustness of a hardware-based solution, and the other offers the adaptability and versatility of a managed service. Yet, this is not merely about choosing between two AWS offerings; it has the potential to redefine how you safeguard your most sensitive data. Let us understand the critical differences between AWS CloudHSM and AWS KMS and determine which service best suits your specific security needs.

Table of Contents
What is AWS CloudHSM?
What is AWS KMS?
Understanding the Key Differences: AWS CloudHSM vs. AWS KMS
AWS CloudHSM and AWS KMS: Which one to Choose?
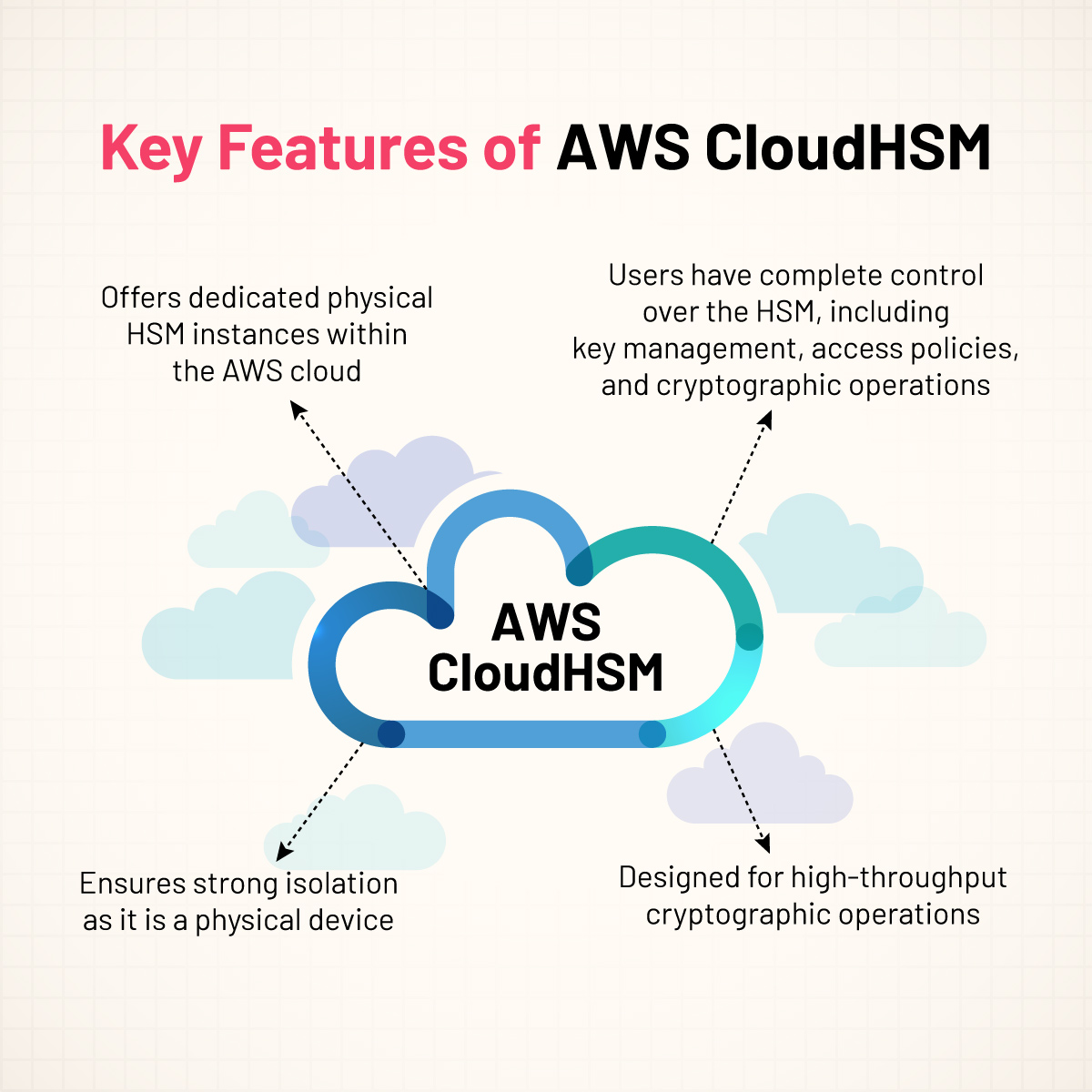
What is AWS CloudHSM?
AWS CloudHSM (Hardware Security Module) provides a robust solution for key storage through its hardware-based approach, ensuring top-tier security and compliance. This cloud-based hardware security module allows users to securely create, store, and oversee cryptographic keys within a tamper-resistant and tamper-evident hardware device. The cryptographic keys are securely stored within the HSM and remain encrypted, never leaving it in plaintext form. It guarantees enhanced protection of the keys from any unauthorized access attempts.
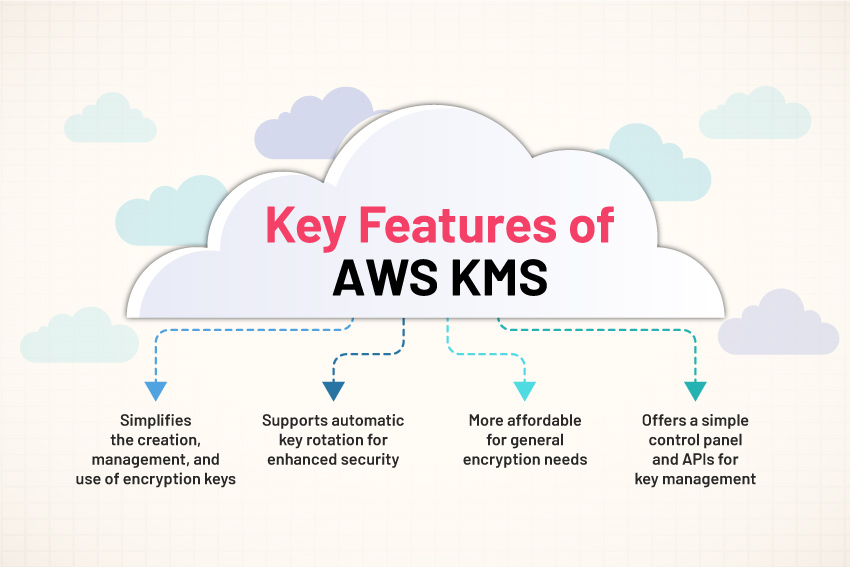
What is AWS KMS?
AWS KMS offers a streamlined solution for generating and managing encryption keys, which play a crucial role in encrypting data. KMS’s design allows it to seamlessly integrate with various AWS offerings, enhancing the security of data stored within these services.
Understanding the Key Differences: AWS CloudHSM vs. AWS KMS
| Aspect | AWS CloudHSM | AWS KMS |
| Purpose | Provides dedicated Hardware Security Module (HSM) instances for key storage and cryptographic operations. | Provides managed service to create and control encryption keys used to encrypt data. |
| Key Management | Users have exclusive control over key management. It includes key generation, key storage, and application of cryptographic operations. | AWS manages the hardware and underlying infrastructure, but users have control over the cryptographic keys and their use. |
| Compliance Standards | Meets high regulatory and compliance requirements, including FIPS 140-2 Level 3, which is suitable for highly regulated industries. | Meets various compliance standards but typically FIPS 140-2 Level 2, offering a balance between security and convenience. |
| Integration | Integration is more complex and limited. Often used in conjunction with other AWS services for enhanced security. | Deeply integrated with AWS services like S3, EBS, RDS, and Redshift, allowing for easy encryption key management within these services. |
| Scalability | Scaling requires manual effort as it involves provisioning additional physical HSM instances. | Highly scalable and can handle higher workloads without manual intervention. |
| Use Case | Ideal for organizations with strict regulatory requirements or those needing to manage their encryption environment closely. | Best suited for organizations looking for an easy-to-use, integrated solution for managing encryption keys across a wide range of AWS services. |
| Ease of Use | Requires specialized knowledge for setup and management, which might be complex for users without prior experience in hardware security. | User-friendly with simplified key management. It is ideal for users who want to manage keys without the complexity of managing the physical hardware involved. |
| Physical Control | Provides exclusive, single-tenant access to physical HSM devices, offering higher isolation and control. | As a managed, multi-tenant service, physical control is handled by AWS, reducing the level of user control over the hardware. |
| Cost | Higher cost due to dedicated hardware. | Lower cost compared to CloudHSM due to the shared environment. |
AWS CloudHSM and AWS KMS: Which one to Choose?
When deciding between AWS CloudHSM and AWS KMS, an organization must consider its specific security, compliance, and usability requirements. CloudHSM is generally used for scenarios requiring stringent regulatory adherence and complete control over the Hardware Security Module (HSM). On the other hand, KMS offers a cost-efficient and user-friendly solution suitable for general key management tasks.
Feel free to explore other blogs:
- AWS EC2 vs. Lambda: Exploring Compute Options in the Cloud
- What is AWS Elastic Beanstalk?
- What is Amazon Elastic Block Store?
- What is AWS EKS?
- CloudTrail in AWS
- What is IAM and Monitoring in the Cloud?
How can InfosecTrain Help?
We hope this article has provided you with a clearer understanding of the difference between AWS CloudHSM and AWS KMS. To delve deeper, consider enrolling in InfosecTrain‘s AWS combo training course. This combo course is tailored to deepen your knowledge of AWS services, emphasizing both theoretical knowledge and practical exercises. Through expert instruction and practical exercises, you will gain invaluable skills, preparing you for advanced roles in cloud security and management. The course offered by InfosecTrain is designed to cater to a range of learners, from those just starting out to seasoned professionals. It covers various topics, from the basics of cloud computing to the sophisticated functionalities of AWS services.






 1800-843-7890 (India)
1800-843-7890 (India)