Best Career Opportunities as a CISSP Professional
If you look around these days, you will see that technology has become more important in our day-to-day lives than it has ever been. With an overabundance of reliance on technology, risks lurk behind every gadget and platform. Regardless of how society views modern technology, cyber security threats posed by it are a severe threat.

So, experts who can help block these technological flaws are in high demand with the constant rise in cybercrime. One of these experts is the CISSP professionals. The CISSP Professionals are internationally acknowledged experts in the field of information technology security. The CISSP Professionals demonstrate their knowledge and skills in IT security and their ability to plan, implement, and manage a cybersecurity program. They have a broad range of responsibilities that apply to many types of organizations. CISSP professionals are on a list of well-informed personnel on cybersecurity concerns and consulted when new policies and procedures are being developed.
If you want to make the next best career move in the world of information security, you should become a CISSP professional. It will not only boost your career options but will also provide you with a plethora of networking opportunities, educational materials, and other benefits. CISSP professionals are also among the highest-paid experts in the market. This article will highlight the career prospects of CISSP professionals.
Job Prospects for CISSP Professionals
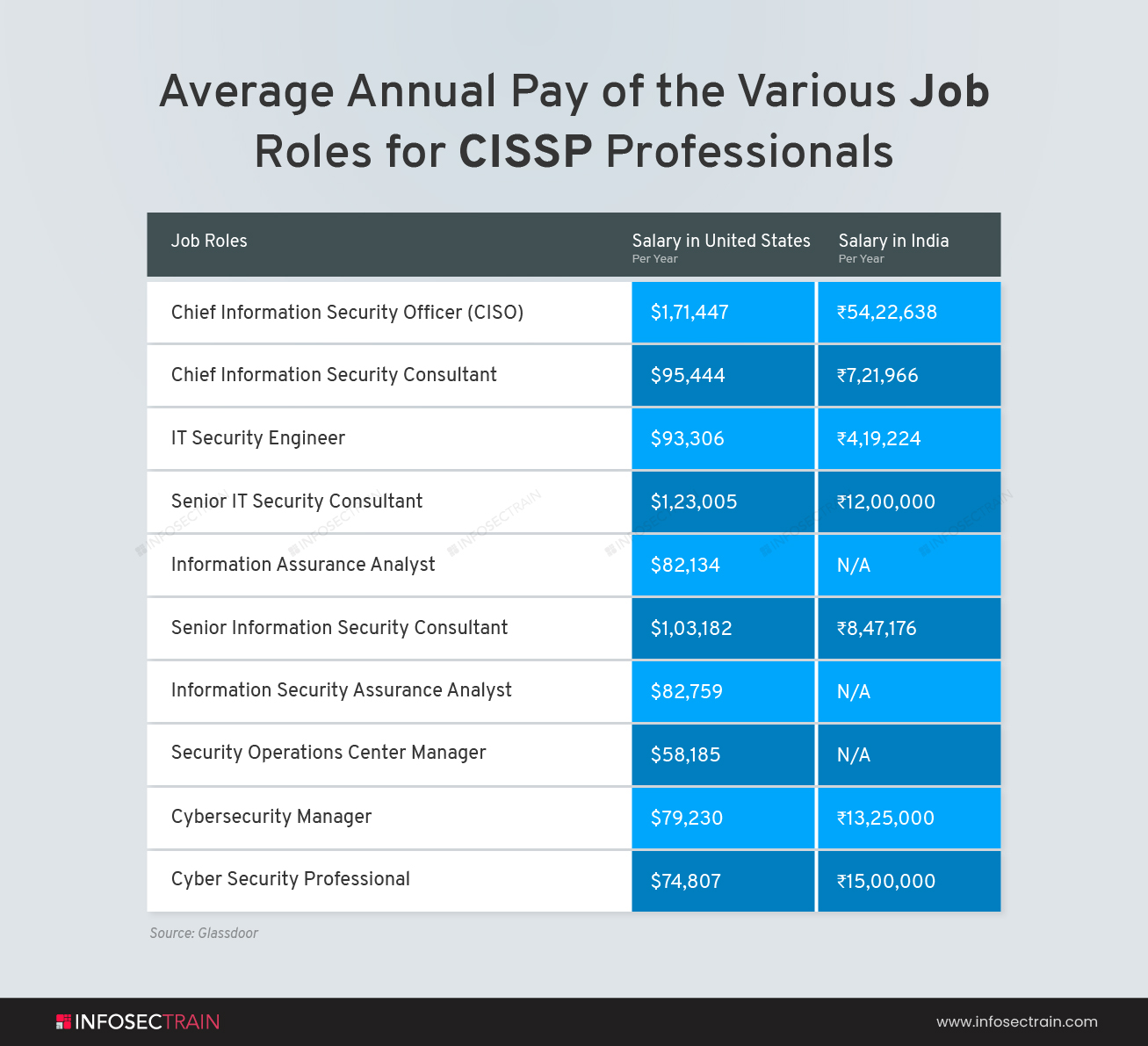
Some of the career options you will get as a CISSP professional are discussed below:
1. Chief Information Security Officer (CISO): A Chief Information Security Officer accredited as CISO is a C-level executive who manages information security in an organization. A CISO creates and implements an information security program, which includes processes and policies to safeguard company communications, systems, and assets from internal and external threats. A CISO needs a wide range of IT experience, as well as excellent leadership and communication skills, in addition to extensive knowledge of information security.
2. Chief Information Security Consultant: A Chief Information Security Consultant is an expert in information security responsible for the confidentiality, integrity, and availability of data and network devices.
3. IT Security Engineer: IT Security Engineers design and monitor information security solutions to avoid cybercrime-related breaches, taps, and leaks.
4. Senior IT Security Consultant: A Senior IT Security Consultant is an IT specialist who specializes in setting up security processes and systems to safeguard a company’s data and network. Internal research and analysis to identify present IT security systems’ strengths and weaknesses, provide solutions to issue areas and suggest new tools and approaches to increase data security are part of their job role.
5. Information Assurance Analyst: An Information Assurance Analyst supervises and leads technology professionals to find and remediate system vulnerabilities and works with IT to ensure suitable policies and protocols to detect and prevent system intrusions.
6. Senior Information Security Consultant: Senior Information Security Consultants are highly qualified and professional consultants that assist businesses in ensuring data security. They use various software security technologies to examine the susceptibility of information systems. The primary responsibility of a Senior Information Security Consultant is to conduct information security assessments, ensure the execution of information security programs, work with firms to strengthen security policies and provide assistance on security management systems.
7. Information Security Assurance Analyst: The Information Security Assurance Analysts will find and fix vulnerabilities, install security solutions, improve user awareness and training, and help with incident response planning. They will assist in the development of security policies and programs and identify and implement relevant technology solutions and the hands-on operation of security-related systems.
8. Security Operations Center Manager: A Security Operations Center Manager ensures the organization’s safety and security by assessing the facility’s state, operational tools and equipment performance, and the adherence of workstream processes to the company’s safety standards and protocols.
9. Cybersecurity Manager: Cybersecurity Managers keep an eye on the channels through which data enters and exits an organization’s network. Their responsibility is to monitor all network operations and manage the infrastructure that enables those operations.
10. Cyber Security Professional: Cyber Security Professionals safeguard online data from being compromised. They ensure the safety of IT infrastructure, data, edge devices, and networks. Their key responsibility is to prevent data breaches as well as monitor and respond to cyber-attacks.
Conclusion
The need for CISSP professionals grows steadily with the rise in the cybersecurity field to provide expert guidance and solutions for security breaches across all industries. Now is a perfect moment to take the initial step toward a highly satisfying and lucrative career as a CISSP professional in almost any business. Enroll in InfosecTrain’s CISSP certification training course to help you become a CISSP professional. We are a global leader in cyber security and information security training.
To know more about the CISSP certification, you can read ‘A comprehensive guide to CISSP certification (2021)’ or watch the video given below.







 1800-843-7890 (India)
1800-843-7890 (India)