Burp Suite: A Practical Walkthrough for Cybersecurity Enthusiasts
Cybersecurity threats are evolving at breakneck speed. With over 2,200 cyberattacks per day and web application vulnerabilities being among the top exploited attack vectors, Penetration Testers and security professionals must stay ahead of the game. According to a recent IBM Security Report, the average cost of a data breach in 2024 surpassed $4.45 million, highlighting the urgent need for robust security testing tools.

Enter Burp Suite—a powerhouse tool used by cybersecurity professionals, Ethical Hackers, and Web Developers to identify and exploit vulnerabilities in web applications. Whether you’re an aspiring CEH participant, Penetration Tester, or Web Application Developer, mastering Burp Suite can significantly enhance your cybersecurity skill set. Let’s take a deep dive into its core functionalities, how to set it up, and practical use cases.
Getting Started with Burp Suite
Before diving into Burp Suite’s advanced features, let’s start with the basics. Burp Suite is a web vulnerability scanner and penetration testing framework developed by PortSwigger. It comes in three versions:
- Burp Suite Community Edition (Free): Ideal for beginners but lacks automation and advanced scanning features.
- Burp Suite Professional: Includes powerful automation and scanning capabilities.
- Burp Suite Enterprise Edition: Designed for continuous security testing in large organizations.
Installing Burp Suite
- Download Burp Suite from PortSwigger’s official website.
- Install Java (if not already installed), as Burp Suite requires Java to run.
- Launch Burp Suite and select your preferred mode (Temporary Project or Open Project).
- Set Up the Browser: Configure Burp Suite as an intercepting proxy to capture and manipulate HTTP/S traffic.
The Proxy Tab – Intercepting HTTP/S Traffic
The Proxy Tab in Burp Suite allows Security Testers to intercept, analyze, and modify HTTP/S requests between the client and the web server. This feature is particularly useful for finding hidden vulnerabilities in web applications.
To configure Burp Suite as an intercepting proxy:
# Set up proxy listener on port 8080
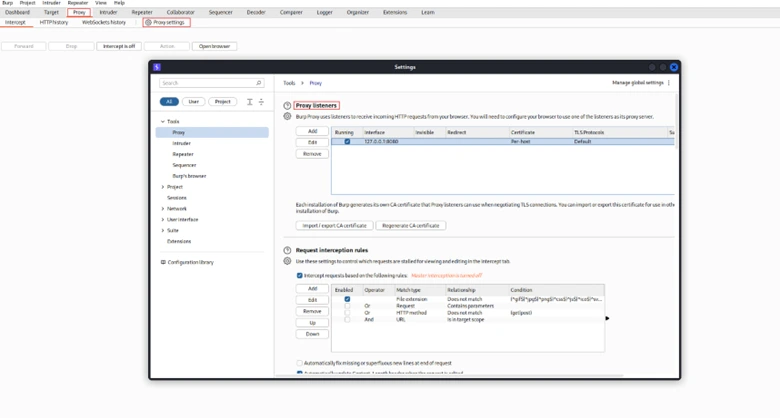
# Configure browser proxy settings to Burp Suite’s IP and Port
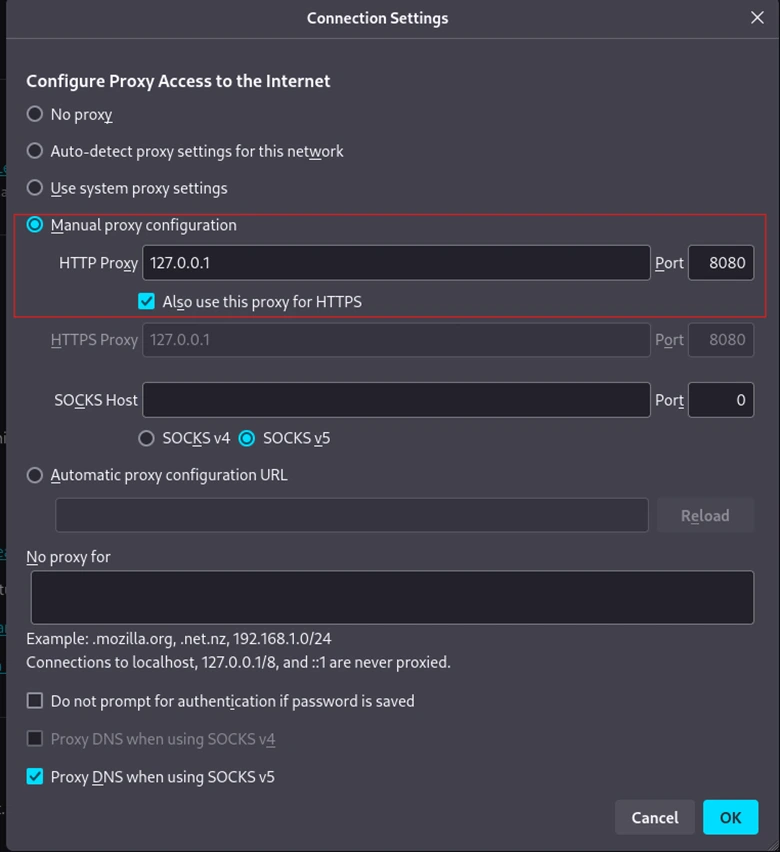
- Enable Intercept: Navigate to the Proxy tab and turn on the “Intercept” option.
- Capture Requests: Open a web application in your configured browser.
- Analyze and Modify Requests: Modify headers, parameters, or body content to test for security loopholes.
- Forward or Drop Requests: Choose to forward the request to the server or drop it entirely.
Pro Tip: Use the “HTTP history” sub-tab to review past intercepted requests without enabling intercept mode.
HTTP History – Understanding and Manipulating Requests
The HTTP history Tab logs all HTTP/S traffic flowing through Burp Suite, allowing testers to inspect requests, responses, headers, and cookies.
Practical Use Cases:
- Session Hijacking: Analyze session tokens and cookies to test for authentication vulnerabilities.
- Identifying Sensitive Data Exposure: Detects sensitive information being transmitted insecurely.
- Testing for SQL Injection & XSS: Modify requests to check for common web vulnerabilities.
To access HTTP History, go to the Proxy → HTTP history tab and click on any request to inspect the details.
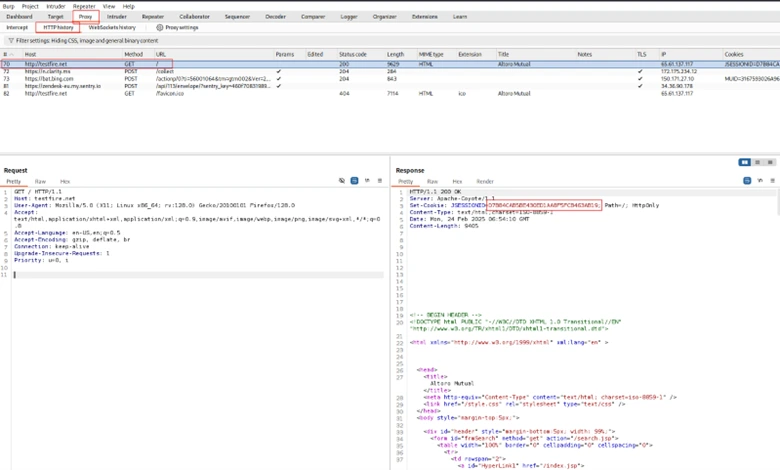
To analyze HTTP history using Burp Suite and command-line tools:
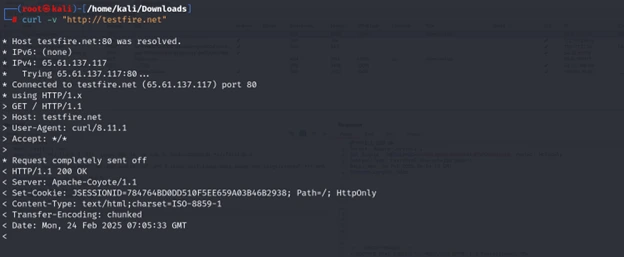
# Use curl to fetch request details
curl -v “http://testfire.net”
# Extract session cookies from a request
curl -c cookies.txt “http://testfire.net”
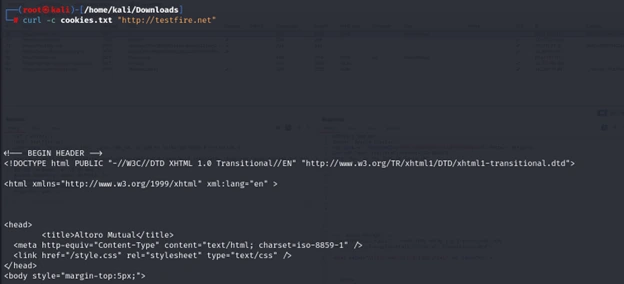
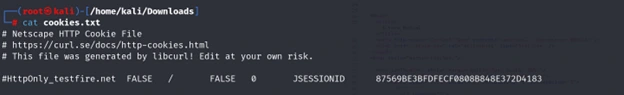
cat cookies.txt
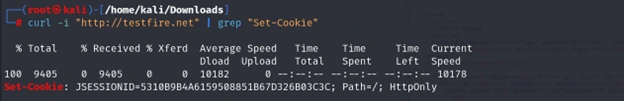
# Analyze responses using grep
curl -i “http://testfire.net” | grep “Set-Cookie”
Intruder – Automating Attacks and Fuzzing Inputs
The Intruder tool is a beast when it comes to automated attacks. Whether you need to brute-force logins, perform parameter fuzzing, or test for injection flaws, Intruder is your go-to feature.
How to Use Intruder?
Automating brute force attacks using Burp Suite Intruder:
# Load a wordlist (for example, a password list)
Steps to perform an attack:
- Select a Request – Go to HTTP history and select a request to test.
- Send to Intruder – Right-click and choose “Send to Intruder.”
- Configure Attack Type – Choose between Sniper, Battering Ram, Pitchfork, or Cluster Bomb (each with a unique attack style).
- Set Payloads – Load dictionaries, custom wordlists, or payloads for the attack.
- Start the Attack – Click “Start Attack” and analyze the results.
Pro Tip: Use Burp Collaborator for advanced external service interaction testing!
Extending Burp Suite with Extensions
One of the most powerful aspects of Burp Suite is its ability to integrate with third-party extensions via the BApp Store.
Popular Burp Suite Extensions:
- Autorize – Helps in detecting broken authentication.
- js – Scans for outdated JavaScript libraries.
- Burp Bounty – Automates security testing.
- Logger++ – Advanced logging for request/response data.
To install an extension:
- Navigate to Extender → BApp Store.
- Browse and select an extension.
- Click “Install” and restart Burp Suite.
Advanced Features and Pro Tips
Scanner – Automated Web Security Testing
The Burp Suite Scanner (Pro version) automates vulnerability detection, identifying SQL Injection, Cross-Site Scripting (XSS), CSRF, and security misconfigurations.
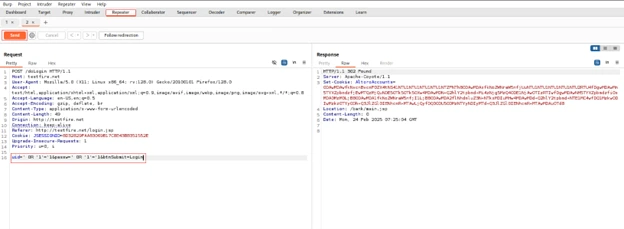
Repeater – Manual Request Manipulation
To manually modify and resend requests:
# Example cURL request to modify and resend
- Send to Repeater – Right-click a request and choose “Send to Repeater.”
- Modify Request Parameters – Edit headers, cookies, or request bodies.
- Send the Request – Click “Send” to observe response changes.
- Analyze Response – Look for anomalies, security vulnerabilities, or authentication flaws. Repeater allows you to modify and resend requests manually to analyze responses in-depth. It’s particularly useful for fine-tuning payloads and debugging security flaws.
Decoder and Comparer- Data Analysis and Comparison
To analyze encoded data:
# Example of decoding a Base64 encoded string
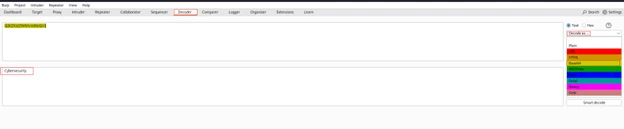
- Decoder helps in encoding/decoding data (Base64, URL encoding, etc.).
- Comparer identifies differences in responses, useful for detecting authentication bypass vulnerabilities.
- Decoder helps in encoding/decoding data (Base64, URL encoding, etc.).
- Comparer identifies differences in responses, useful for detecting authentication bypass vulnerabilities.
How Can InfosecTrain Help You?
Burp Suite is a game-changer in web application security testing, offering a suite of tools for both beginners and professionals. From intercepting HTTP/S requests to automating attacks with Intruder, mastering Burp Suite can significantly boost your cybersecurity expertise.
Key Takeaways:
- The Proxy Tab is essential for intercepting and modifying traffic.
- HTTP History helps analyze past requests for vulnerabilities.
- The Intruder tool automates attacks like brute-forcing and fuzzing.
- Extensions supercharge Burp Suite’s capabilities.
- Advanced features like Scanner, Repeater, and Decoder streamline vulnerability analysis.
As cybersecurity threats continue to rise, tools like Burp Suite will remain a cornerstone for Ethical Hackers and Penetration Testers. Ready to take your cybersecurity skills to the next level? Start exploring Burp Suite today!
If you want to enhance your cybersecurity skills, InfosecTrain offers comprehensive cybersecurity courses designed for beginners and professionals. From Certified Ethical Hacker (CEH) training to Advanced Penetration Testing, our courses provide hands-on expertise in tools like Burp Suite, helping you stay ahead in the cybersecurity domain.
Take the next step in your cybersecurity journey—Explore InfosecTrain’s courses today!
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 16-Aug-2025 | 28-Sep-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 06-Sep-2025 | 12-Oct-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 20-Sep-2025 | 26-Oct-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |

 1800-843-7890 (India)
1800-843-7890 (India)