CCSP Domain 4: Cloud Application Security
With the rapid growth of use as well as acclamation of cloud computing, the demand for qualified security professionals with the technical knowledge required by cloud computing has also increased. While many businesses have skilled security and operations professionals, most of what they know about traditional data centers is insufficient for the unique challenges and features of cloud computing.
To bridge that gap, the (ISC)2 and the Cloud Security Alliance (CSA) teamed up to design the Certified Cloud Security Professional (CCSP) certification, which verifies cloud security professionals’ knowledge and skills while also providing the education needed to provide adequate security in the cloud.
The CCSP Common Body of Knowledge (CBK) covers a broad range of topics applicable to all facets of cloud security. There are six domains in the CCSP exam:
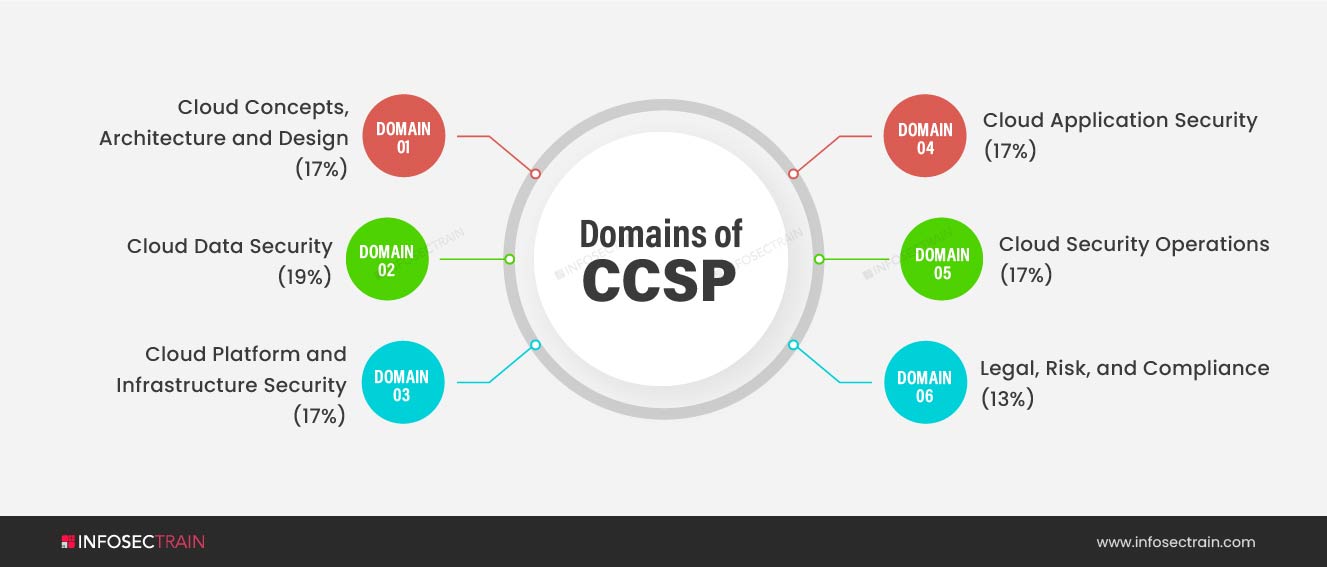
- Domain 1: Cloud Concepts, Architecture and Design (17%)
- Domain 2: Cloud Data Security (19%)
- Domain 3: Cloud Platform and Infrastructure Security (17%)
- Domain 4: Cloud Application Security (17%)
- Domain 5: Cloud Security Operations (17%)
- Domain 6: Legal, Risk, and Compliance (13%)
This article will go through CCSP Domain 4: Cloud Application Security and what candidates should expect in this domain when they prepare for the exam.
Cloud Application Security
Cloud environments and cloud technologies are increasingly gaining prominence because of their low cost and flexibility. The lead time and costs associated with procuring environments or test servers in a traditional data center are largely mitigated in a cloud environment. Cloud environments offer incredible efficiencies and ease in bringing online environments and virtual machines quickly for developers, and costs are only incurred while they are live and operating. The fourth domain of CCSP will focus on cloud application security. Cloud security professionals must have a sound knowledge of secure cloud-based applications, software development and deployment challenges, software security and performance testing methods, and Identity and Access Management (IAM) solutions. It holds the 17% weightage and covers the following topics:
- Advocate Training and Awareness for Application Security
- Describe the Secure Software Development Life Cycle (SDLC) Process
- Apply the Secure Software Development Life Cycle (SDLC)
- Apply Cloud Software Assurance and Validation
- Use Verified Secure Software
- Comprehend the Specifics of Cloud Application Architecture
- Design Appropriate Identity and Access Management (IAM) Solutions
You can watch the video below to acquire a knowledge of the CCSP 4th domain exam outline in detail:
Below is the description of various subsections of the fourth domain of CCSP, along with what you can expect on the CCSP certification exam.
Advocate Training and Awareness for Application Security
The fourth domain of CCSP certification covers the training and awareness for application security. The popularity and pervasiveness of cloud application development are continuously growing. A well-educated professional is essential for an organization to make informed decisions about its specific demands and requirements with cloud computing. Training is frequently required when new development methodologies are introduced. This rule applies to cloud computing as well. Cloud Security Professionals and developers must have a good awareness of the realities of cloud environments, what is required to secure them, and the common risks and vulnerabilities that a cloud faces to leverage effective cloud development, especially with security in mind.
Describe Secure Software Development Life Cycle (SDLC) Process
Domain 4 of CCSP delves into the Software Development Life Cycle (SDLC) in the cloud, including an in-depth study at each step, what it comprises, business requirements, and the critical components that must be addressed before we move on to the next stage, as well as the SDLC’s cyclical nature.
Apply Secure Software Development Life Cycle (SDLC)
This section of domain 4 discusses how to apply a secure Software Development Life Cycle (SDLC) in a cloud environment and avoid common vulnerabilities during the development process. The primary threats and vulnerabilities from the STRIDE and DREAD models are discussed, as well as their application to cloud settings. The section also explains how to ensure that cloud apps are only built and deployed when they are completely secure.
Apply Cloud Software Assurance and Validation
This section of Domain 4 discusses numerous distinct application testing and scanning methods, which are not exclusive to cloud hosting or development. These types are made up of various methodologies and points of view, and when utilized together, they enable exhaustive and comprehensive testing of systems and applications. Static application security testing (SAST) is done with full knowledge of system configurations and access to source code and is done against non-live systems. Dynamic application security testing (DAST) is considered “black-box” testing, which is done against live systems with no special or inside knowledge. Penetration testing focuses on the capabilities of some systems and applications to self-protect and prevent or mitigate attacks as they occur. In contrast, RASP focuses on the capabilities of some systems and applications to self-protect and block or reduce attacks as they occur.
Use Verified Secure Software
The use of verified secure software is covered in this section. Because most modern applications, particularly those in cloud environments, are based on components, services, and Application Programming Interfaces (API) that consume other services and data, selection and verification of relevant elements that match security needs is critical. The old cliché about the weakest link holds true in this case, as a single component’s weakness might expose an entire application or system to attacks and vulnerabilities. Regardless of the source of the components, including commercial, open-source, and community-sourced apps, the same verification and selection process applies.
Comprehend the Specifics of Cloud Application Architecture
Other commonly used technologies and paradigms in cloud computing are discussed in this section, in addition, to secure development principles and techniques. Extensible Markup Language (XML) appliances, web application firewalls (WAFs), and systematic approaches like sandboxing and application virtualization are all examples of this. Their significance in cloud computing, as well as their critical use and reliance on cryptography, are also explored.
Design Appropriate Identity and Access Management (IAM) Solutions
This section of Domain 4 discusses multi-factor authentication technologies, as well as strategic approaches to identity and access management (IAM) and building them into applications during development. Federated Identity Management to provide the policies, processes, and mechanisms that manage identity and trusted access to systems across organizations are also discussed.
CCSP with InfosecTrain
Obtaining a widely acknowledged and recognized industry-standard certification will help you advance in your IT career. The CCSP will set out as an independent verification of your skills and comprehension of these principles to any employer or regulatory agency, with cloud computing increasing rapidly and more enterprises yearning to utilize its potential. If you want to further your IT security career with CCSP certification, you can check and enroll in the CCSP online training and certification course at InfosecTrain. We are a globally leading IT security training organization. Our certified trainers have extensive experience in the industry, which they will share with you during your course. The course will provide you a thorough comprehension of application security, the secure Software Development Life Cycle (SDLC) process, and how to create appropriate Identity and Access Management systems.






 1800-843-7890 (India)
1800-843-7890 (India)