CEH Module 12: Evading IDS, Firewalls, and Honeypots (Part-1)
Have you ever wondered how hackers bypass the sophisticated security measures organizations implement? How do they evade Intrusion Detection Systems (IDS), Firewalls, and Honeypots designed to trap them? Understanding these techniques is essential for defending against attacks and enhancing the security systems you help create.

As businesses increasingly rely on the Internet, protecting network infrastructure has become more critical. However, cyber attackers are constantly adapting and discovering new methods to infiltrate even the most secure networks. This CEH module 12 will guide you through hackers’ methods to evade IDS, Firewalls, and Honeypots and show you how to counter these techniques effectively. So, let’s first understand what Intrusion Detection Systems (IDS) is.
The Hidden Tale of Intrusion Detection Systems (IDS)
An Intrusion Detection System (IDS) is a critical component in the cybersecurity arsenal, designed to monitor, detect, and protect networks or systems from malicious activities. Acting as a vigilant sentinel, an IDS alerts security personnel immediately upon detecting intrusions, thereby enabling a rapid response to potential threats.
IDS systems are invaluable because they continuously monitor a network’s inbound and outbound traffic, scrutinizing activities to detect any signs of security breaches. Specifically, they analyze traffic for signatures that match known intrusion patterns and raise an alarm when a match is detected. This proactive strategy is crucial for detecting and addressing cyber threats before they can cause substantial damage.
Types of IDS
IDS are categorized into two main types based on their functionality:
- Passive IDS: This type of IDS primarily focuses on detecting intrusions. Passive IDS monitors network traffic and logs potential security breaches, alerting security personnel without actively preventing the intrusion.
- Active IDS (also known as IPS – Intrusion Prevention Systems): Unlike passive IDS, an active IDS detects intrusions and takes action to prevent them. This might include blocking traffic from suspicious IP addresses or terminating malicious sessions.
Additionally, IDS can be classified into network-based IDS (NIDS) and host-based IDS (HIDS) based on their deployment locations.
- Network-Based Intrusion Detection Systems (NIDS): Network-Based Intrusion Detection Systems (NIDS) are intended to observe and evaluate network traffic for indications of malicious behavior. It inspects every packet that enters the network for anomalies and incorrect data. By thoroughly examining all traffic, NIDS can identify potential security breaches and generate alerts based on the content observed. Some of the key features include:
1. Extensive Traffic Monitoring: NIDS captures and inspects all network traffic, generating alerts at the IP or application level based on detected anomalies.
2. Distributed Deployment: NIDS are typically more distributed than host-based IDS, identifying anomalies at both the router and host levels.
3. Comprehensive Auditing: They audit the information in data packets, log malicious packets, and assign threat levels to each risk, helping the security team remain vigilant.
4. Promiscuous Mode Operation: NIDS often consists of a black box placed on the network in promiscuous mode, which listens for patterns indicative of an intrusion, such as DoS attacks, port scans, or unauthorized access attempts.
- Host-Based Intrusion Detection Systems (HIDS): Host-Based Intrusion Detection Systems (HIDS) focus on monitoring and analyzing the behavior of individual devices (hosts) within a network. HIDS can be installed on any system, from desktop PCs to servers, providing a versatile solution for detecting unauthorized activities. Some of the key features include:
1. System-Specific Monitoring: HIDS analyzes each system’s behavior, focusing on detecting unauthorized insider activities and file modifications.
2. Versatility: They can be deployed on various platforms, including Windows and UNIX, making them more versatile than NIDS.
3. Detailed Event Auditing: HIDS audits events that occur on a specific host, providing detailed insights into changes and activities on the device.
4. Platform-Centric Focus: HIDS often focuses on platform-specific behaviors, significantly emphasizing the Windows operating system.
Functions of IDS
- Information Gathering and Analysis: An IDS collects and scrutinizes information from within a computer or a network to identify possible violations of security policies, such as unauthorized access or misuse.
- Packet Sniffing: Often referred to as a “packet sniffer,” an IDS intercepts packets traveling via various communication media and protocols, usually TCP/IP.
- Traffic Evaluation: The intercepted packets are analyzed after they are captured. An IDS evaluates this traffic for suspected intrusions and raises an alarm upon detecting such activities.
Where Should You Place Your IDS for Maximum Security?
Have you ever been asked where to place your Intrusion Detection System (IDS) for optimal security? The placement of your IDS is vital for ensuring it performs efficiently in monitoring and detecting intrusions. Here’s how to strategically position your IDS within your network.
One of the most common places to deploy an IDS is near the firewall. But should it be outside or inside the firewall? The answer depends on the specific traffic you wish to monitor. When placed inside, the IDS is ideal if it is near a Demilitarized Zone (DMZ), which adds an additional layer of security. However, the best practice is to use a layered defense approach by deploying one IDS in front of the firewall and another behind it within the network.
How IDS Works?

An IDS operates as follows:
- Detection of Malicious Signatures: IDS has sensors that detect malicious signatures in data packets. Some advanced IDS also include behavioral activity detection to identify malicious traffic behavior. Even if packet signatures do not match perfectly with the signatures in the IDS database, the activity detection system can alert Security Administrators about possible attacks.
- Predefined Actions: If a signature matches, the IDS performs predefined actions such as terminating the connection, blocking the IP address, dropping the packet, and raising an alarm to notify the Security Administrators.
- Anomaly Detection: When the signature matches, anomaly detection may be skipped; otherwise, the sensor may analyze traffic patterns for anomalies.
- Forwarding Packets: The IDS will forward it to the network once the packet passes all tests.
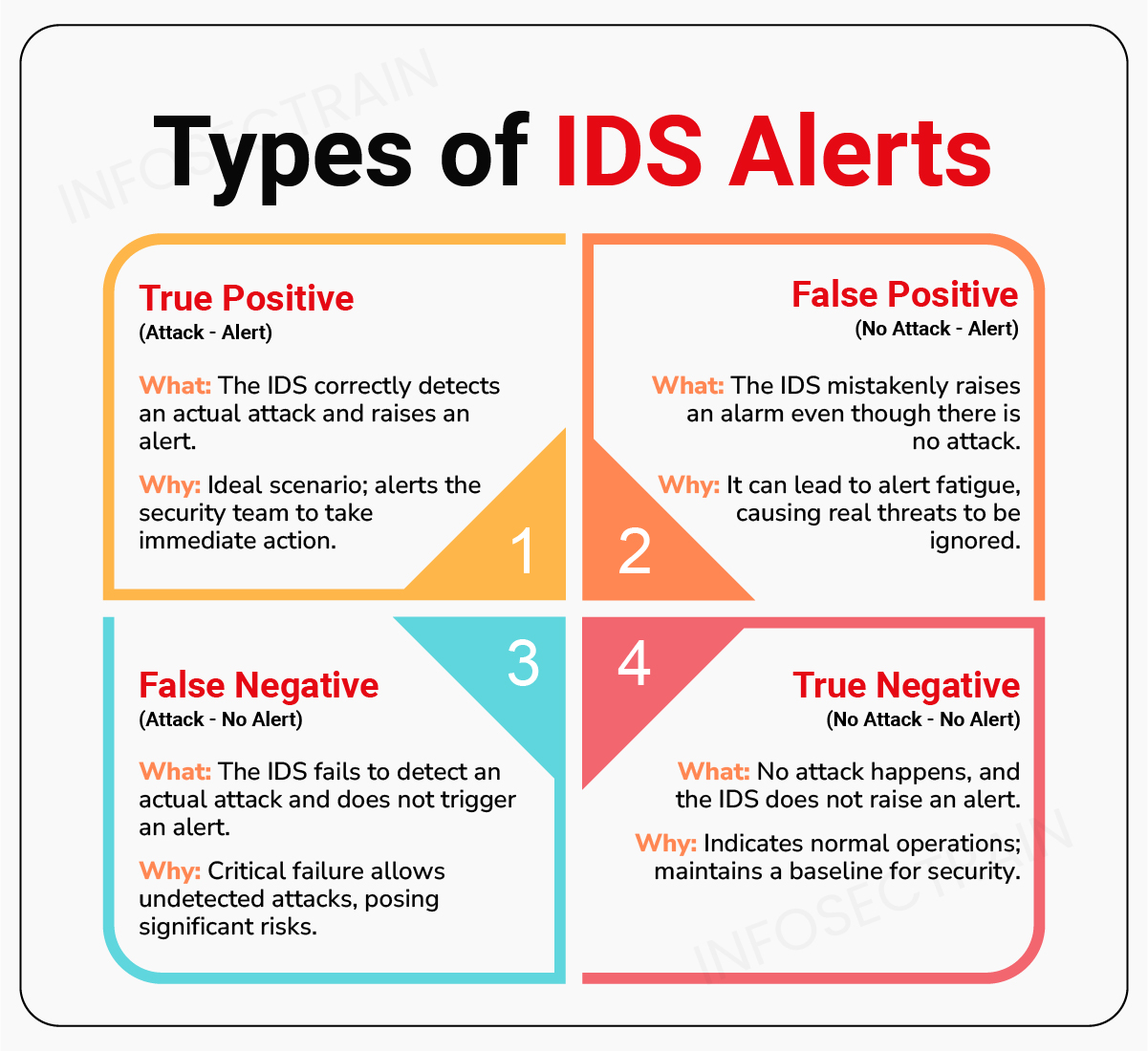
Types of IDS Alerts
Understanding the different types of alerts that an IDS can generate is crucial for effective network security management. Four types of IDS alerts include:
Intrusion Prevention System
Intrusion Prevention Systems (IPS) are advanced security measures that not only detect intrusions but actively prevent them. As active IDS, IPS continuously monitors network traffic, sitting behind firewalls as an added layer of defense. Unlike passive IDS, which only alerts security teams about potential threats, IPS is positioned inline within the network, between the source and destination. This strategic placement allows IPS to analyze network traffic in real-time and make automated decisions to protect the network. Some of the key functions include:
- Generate Alerts: IPS generates alerts if any abnormal traffic is detected within the network, ensuring that security teams are immediately aware of potential threats.
- Continuous Monitoring: They continuously record real-time logs of network activities, providing a comprehensive view of network health and potential security incidents.
- Block and Filter Malicious Traffic: IPS actively blocks and filters out malicious traffic, preventing harmful data from entering the network.
- Rapid Threat Response: Positioned inline, IPS detects and eliminates threats quickly, minimizing the time that malicious activities have to impact the network.
- Accurate Threat Identification: IPS accurately identifies threats without generating false positives, ensuring that security teams focus on genuine threats without unnecessary distractions.
An IPS operates based on predefined rules and policies configured by network administrators. These rules determine the actions the IPS takes when detecting potential intrusions, such as logging the event, blocking the offending traffic, or even modifying network configurations to mitigate the threat. This proactive approach enables IPS to prevent the occurrence of intrusions or attacks rather than simply detecting them after they occur.
Benefits of IPS
- Enhanced Security: By blocking malicious traffic and preventing intrusions, IPS significantly enhances network security.
- Comprehensive Logging: Continuous real-time logging provides valuable insights into network activities and potential threats.
- Reduced False Positives: Accurate threat identification minimizes false positives, allowing security teams to concentrate on actual threats.
- Rapid Response: Inline placement allows for quick detection and elimination of threats, reducing potential damage.
To be continued…
Firewalls and Honeypots
Master CEH with InfosecTrain
Ethical hacking is a complex and multi-phase process that requires deep knowledge and security certifications. Professionals can improve their security assessment and network architecture skills through ethical hacking courses, such as the Certified Ethical Hacker training provided by InfosecTrain. This training provides individuals with the essential skills and methods needed to perform sanctioned hacking into organizations.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 26-Apr-2025 | 01-Jun-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Close ] | |
| 11-May-2025 | 28-Jun-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 31-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 07-Jun-2025 | 13-Jul-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 21-Jun-2025 | 27-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |


 1800-843-7890 (India)
1800-843-7890 (India)