CompTIA CySA+ Domain 1: Threat and Vulnerability Management
Introduction to CompTIA CySA+
The CompTIA Cybersecurity Analyst (CySA+) certification is the industry standard for demonstrating that cybersecurity professionals can analyze data and interpret the results to detect vulnerabilities, threats, and risks to an organization. It is offered by CompTIA, a nonprofit trade organization that provides vendor-neutral certification in a range of IT fields.

You must pass the CS0-002 exam to become a CompTIA CySA+ certified professional. It verifies that candidates have the knowledge and skills needed to use intelligence and threat detection techniques, identify and address vulnerabilities, analyze and interpret data, recommend preventive actions, and successfully respond to and recover from incidents.
Domains of CySA+
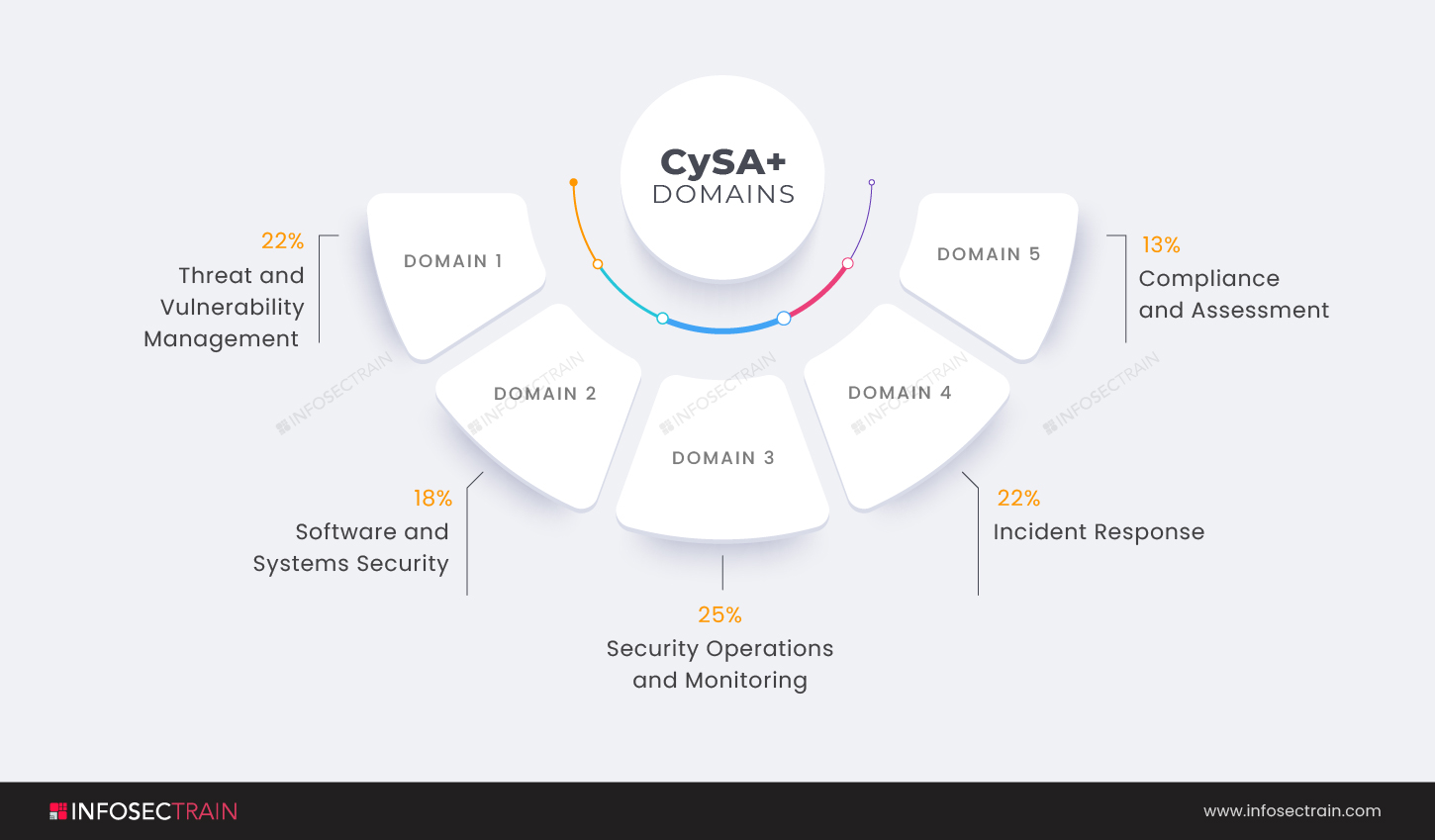
- Domain 1: Threat and Vulnerability Management (22%)
- Domain 2: Software and Systems Security (18%)
- Domain 3: Security Operations and Monitoring (25%)
- Domain 4: Incident Response (22%)
- Domain 5: Compliance and Assessment (13%)
This article provides an overview of the CompTIA CySA+ Domain 1: Threat and Vulnerability Management.
CompTIA CySA+ Domain 1: Threat and Vulnerability Management
Cybersecurity Analysts are in charge of ensuring the confidentiality, integrity, and availability of their organization’s information and information systems. Threat and Vulnerability Management is the first domain in the CompTIA CySA+ certification exam. The domain comprises 22% weightage. In the first domain of the CySA+ certification, you will learn how to identify the cybersecurity threats your company faces and evaluate the risk they pose to your operations’ confidentiality, integrity, and availability.
To prevent or mitigate threats, security professionals must have full knowledge of them. You will learn about several types of threat intelligence in this domain, as well as sources and methods for evaluating the relevance and accuracy of a threat intelligence source. You will also learn how to use threat intelligence in your business.
Threats and vulnerabilities must be managed for your systems to remain secure. Threat and vulnerability management provides actionable data that may be used to quickly eliminate threats and vulnerabilities in your environment, lowering your risk exposures. In this domain, you will learn to use a well-defined methodology, and continuous assessment approaches to identify, prioritize, and remediate threats and vulnerabilities. The first domain of the CompTIA CySA+ certification exam covers the following subtopics:
- Explain the importance of threat data and intelligence
- Given the scenario, utilize threat intelligence to support organizational security
- Given a scenario, perform vulnerability management activities
- Given a scenario, analyze the output from common vulnerability assessment tools
- Explain threats and vulnerabilities associated with specialized technology
- Explain threats and vulnerabilities associated with operating in the cloud
- Given the scenario, implement controls to mitigate attacks and software vulnerabilities
1. Explain the importance of threat data and intelligence: Threat intelligence is data that an organization utilizes to understand the risks that have targeted, will target, or are presently attacking in a better way. This information is used to anticipate, prevent, and identify cyber threats attempting to exploit valuable resources. This section will teach you about the many types of threat intelligence and sources and methods for evaluating the relevance and accuracy of a threat intelligence source.
This section will address sources that you can use in your work. There is an enormous threat intelligence community, and this section will explore sources that you may utilize in your work. Threat classification and threat actors will also be covered. In this segment, one will be tested on topics such as where to obtain intelligence and how to manage indicators such as STIX and TAXII.
2. Given the scenario, utilize threat intelligence to support organizational security: This section covers attack frameworks like MITRE ATT&CK, the diamond model of intrusion analysis, and Lockheed Martin’s cyber kill chain created to help you as you model and describe threats. Threat research, such as using the Behavioral Indicator of Compromise (BIC) or the Common Vulnerability Scoring System (CVSS), and threat modeling methodologies to estimate the risk posed by specific threats, are also covered. It will also go over threat intelligence sharing with supported functions.
3. Given a scenario, perform vulnerability management activities: The process of identifying, analyzing, treating, and reporting security vulnerabilities in systems and the software that runs on them is known as vulnerability management. This, combined with other security measures, is critical for businesses to prioritize risks and reduce their attack probabilities. This section discusses how to identify vulnerabilities, true or false positives, and negatives, patching or hardening, risk acceptance, scanning parameters and criteria, vulnerability management tools like IDS, IPS, firewalls. It will also go over the function of MOUs and SLAs, and the need to keep the business running while evaluating remedial options.
4. Given a scenario, analyze the output from common vulnerability assessment tools: Vulnerability reports can provide a lot of information with regard to potential system flaws. This section focuses on a crucial aspect of anyone responsible for system security: analyzing logs generated by vulnerability assessment tools. Penetration testing tools such as Nikto, OWASP Zed Attack Proxy (ZAP), Burp Suite, or Arachni, infrastructure vulnerability scanners such as Nessus, OpenVAS are discussed. The domain may cover the software assessment tools and techniques and enumeration using Nmap or hping, wireless penetration testing options such as Reaver, and cloud infrastructures assessment tools like Prowler and Pacu. The section also discusses reverse engineering, static and dynamic analysis, as well as fuzzing.
5. Explain threats and vulnerabilities associated with specialized technology: A lot of IT professionals, especially novice Cybersecurity Analysts, have experience with the core technologies used in a corporate context, such as Windows and Linux hosts, switches and routers, and maybe firewalls and intrusion detection systems. These systems are common in a corporate network environment. However, there are special technologies to which many Cybersecurity Analysts are not exposed during their careers.
A threat is a process that increases the possibility of a negative event, such as a vulnerability being exploited. On the other hand, a vulnerability is a flaw in your infrastructure, networks, or apps that could expose you to threats. This section is significant since it tackles vulnerabilities connected with today’s most popular technologies, such as IoT and mobile alternatives. Process automation systems, industrial control systems, and SCADA are also addressed, as are system-on-chip (SoC) and real-time operating systems (RTOS).
6. Explain threats and vulnerabilities associated with operating in the cloud: Unauthorized access through inadequate access controls and the misuse of employee credentials are two of the most prominent cloud security issues. Unauthorized access and unsecured APIs are tied for first place as the single most perceived cloud security vulnerability. This section delves more into the threats that come with the widespread use of the cloud. It covers topics such as cloud service models (SaaS, PaaS, IaaS), cloud deployment models (public/private/hybrid/community), serverless architecture, Infrastructure as Code (IaC), improper key management, unprotected storage, and logging and monitoring.
7. Given the scenario, implement controls to mitigate attacks and software vulnerabilities: Data and information systems, as well as other information assets, must be safeguarded from security threats. This section discusses how to recognize potential attacks that a professional might face. It will cover overflow, remote code execution, XML assaults, session hijacking, and cross-site scripting, as well as vulnerabilities such as poor error handling, dereferencing, unsecured object references, race conditions, sensitive data exposure, insecure components, and failed authentication.
CompTIA CySA+ with InfosecTrain
InfosecTrain, a significant provider of Information Technology and cybersecurity training, offers the CompTIA CySA+ certification training course. We help participants in our training program be very efficient in learning knowledge about advanced persistent threats, as well as how to configure and use threat-detection tools. Every step of the journey, our trainers will be there for you! So get started with InfosecTrain today to prepare for the CompTIA Cybersecurity Analyst (CySA+) certification exam.







 1800-843-7890 (India)
1800-843-7890 (India)