CompTIA CySA+ Domain 3: Security Operations and Monitoring
When it comes to your company’s security, knowing what is going on behind the scenes in your network and computer systems is critical. It not only provides important insights into the threats you face, but it also provides the information you need to rapidly and efficiently fix security issues as they emerge. That is when it comes to securing your assets; being proactive is crucial. Therefore, security operations and monitoring are vital for Cybersecurity Analysts to avoid data breaches and cyber-attacks.
The CompTIA Cybersecurity Analyst+ (CySA+) certification exam requires you to know how to use tools and resources to monitor activities so that you can observe what’s going on and what the apps and users are doing, as well as how the system is working, and there are a variety of tools you may use to do so.
Domains of CySA+
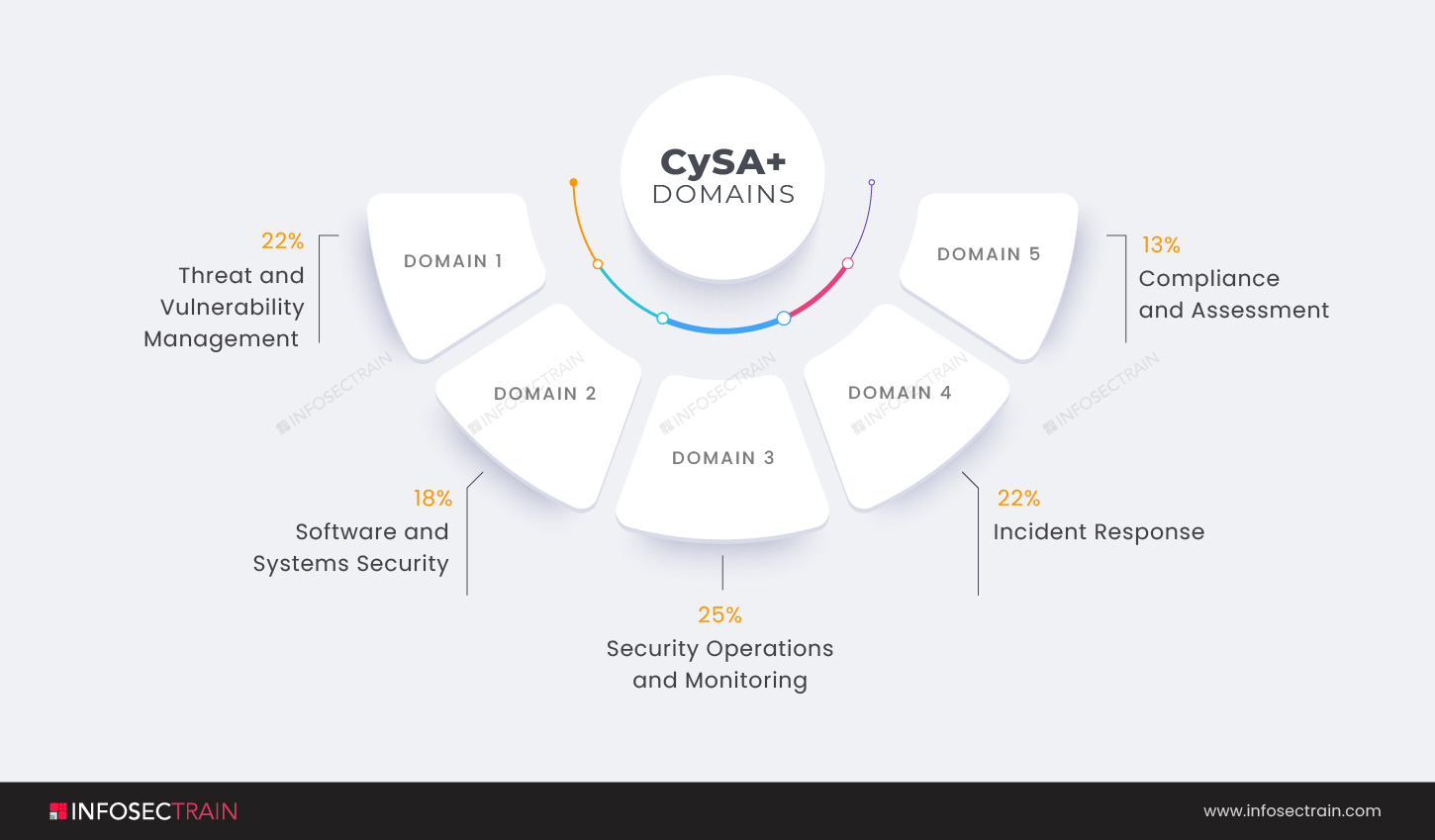
- Domain 1: Threat and Vulnerability Management (22%)
- Domain 2: Software and Systems Security (18%)
- Domain 3: Security Operations and Monitoring (25%)
- Domain 4: Incident Response (22%)
- Domain 5: Compliance and Assessment (13%)
This article gives an overview of the CompTIA CySA+ Domain 3: Security Operations and Monitoring.
CompTIA CySA+ Domain 3: Security Operations and Monitoring
The third domain of the CompTIA CySA+ certification exam is Security Operations and Monitoring. The domain comprises 25% weightage. You will learn about the fundamentals of security monitoring, how to set up and monitor various sorts of nodes/systems on your network, and how to configure multiple security technologies to help harden your system, devices, and applications against attackers. In the third domain of the CySA+ certification, you will learn how to effectively protect your resources by configuring them and monitoring Indicators of Compromise (IoC). When you are completed with this domain, you will have the abilities and knowledge, which includes how to better safeguard your resources and what Indicators of Compromise (IoC) you should be monitoring.
The third domain of the CompTIA CySA+ certification exam covers the following subtopics:
- Given the scenario, analyze data as part of security monitoring activities
- Given a scenario, implement configuration changes to existing controls to improve security
- Explain importance of proactive threat hunting
- Compare and contrast automation concepts and technologies
1. Given the scenario, analyze data as part of security monitoring activities
This section delves into the process of data analysis. The amount of data generated by security monitoring activities is substantial. It is necessary to understand the various data formats that you see and recognize data kinds and actions that suggest a malicious activity for determining what is significant and what is not. The section will discuss heuristics, trend analysis, impact analysis, Security Information and Event Management (SIEM) review, email analysis, and query writing as part of security monitoring tasks.
2. Given the scenario, implement configuration changes to existing controls to improve security
This section will go over concepts like firewall setup, data loss prevention, endpoint detection and response, network access control, as well as how to implement configuration modifications to existing controls to improve security. Permissions, allow lists, blocklists, firewalls, Intrusion Prevention System (IPS) rules, Data Loss Prevention (DLP), Endpoint Detection and Response (EDR), sinkholing, malware signatures, sandboxing, and port security will all be covered.
3. Explain importance of proactive threat hunting
This section will explore the concept and importance of threat hunting. Threat hunting is a proactive security search of networks, endpoints, and datasets for malicious, suspicious, or risky actions that have eluded existing detection systems. This method instructs your security team on where to look and what to look for. They can see emerging issues and contain them before they become full-fledged security breaches. As a result, they will jump ahead in the race.
Establishing a hypothesis, threat hunting tactics, profiling threat actors and activities, reducing the attack surface area, bundling vital assets will be covered in this section. It will also go over numerous attack vectors, the notion of integrated intelligence, and methods for increasing detection capabilities.
4. Compare and contrast automation concepts and technologies
The domain emphasizes the importance of automation in security and some of its popular applications, such as creating malware signatures and evaluating threat feeds. This section will go over how to compare and contrast various automation concepts and technologies, such as Application Programming Interface (API) integration, automated malware signature creation, and data enrichment. It will also cover threat feed combination, machine learning, automation protocols and standards, continuous integration, and deployment/delivery.
CompTIA CySA+ with InfosecTrain
InfosecTrain, a significant provider of IT and cybersecurity training and an authorized partner of CompTIA, offers the CompTIA CySA+ certification training course. We help participants understand how to configure and use technologies to ensure that suspicious activity in their environment is rapidly discovered and dealt with. Our trainers will be there for you at every step of your certification journey. So you can enroll with InfosecTrain today to prepare for the CompTIA Cybersecurity Analyst (CySA+) certification exam.







 1800-843-7890 (India)
1800-843-7890 (India)