CompTIA PenTest+ Domain 5: Tools and Code Analysis

Domains of CompTIA PenTest+:
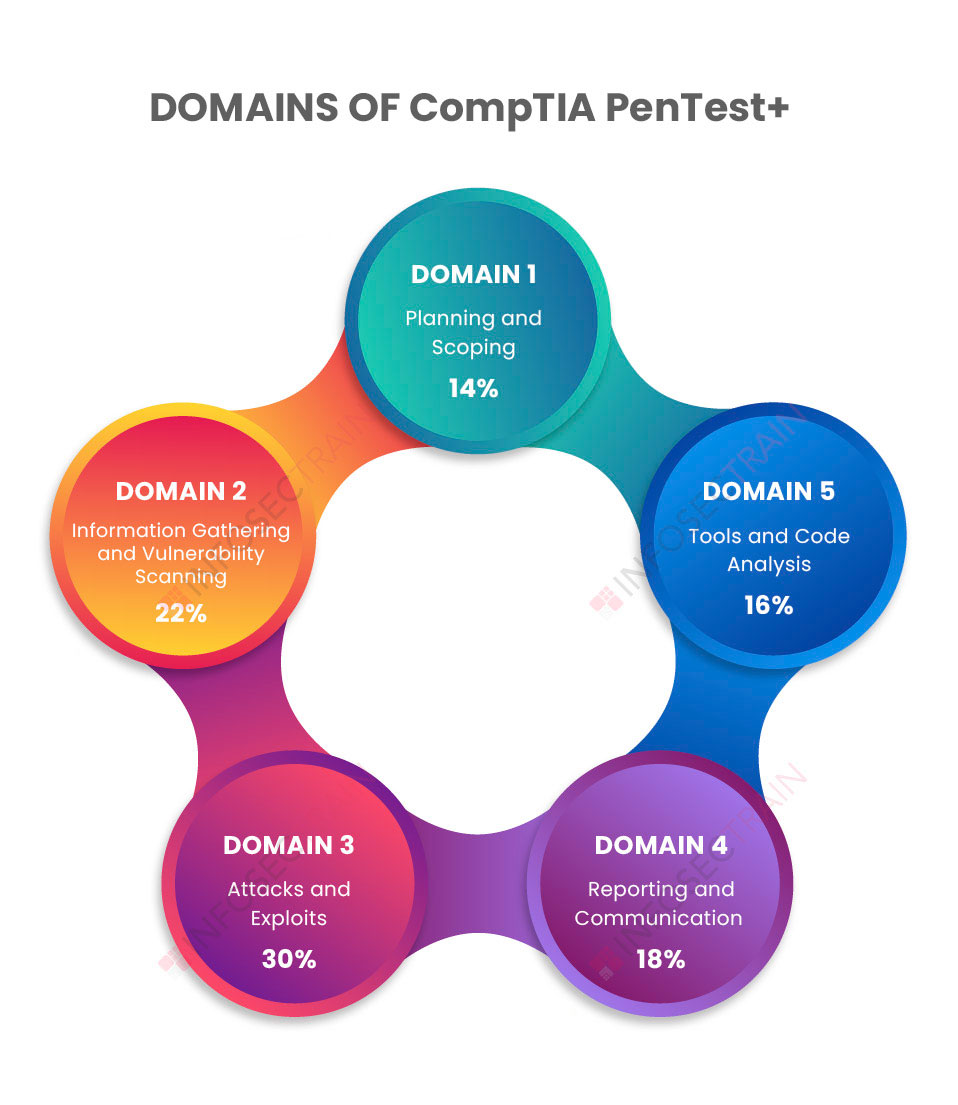
- Domain 1: Planning and Scoping (14%)
- Domain 2: Information Gathering and Vulnerability Scanning (22%)
- Domain 3: Attacks and Exploits (30%)
- Domain 4: Reporting and Communication (18%)
- Domain 5: Tools and Code Analysis (16%)
This article explores domain 5 of CompTIA PenTest+ certification, which is Tools and Code Analysis.
CompTIA PenTest+ Domain 5: Tools and Code Analysis
“Tools and Code Analysis” is one of the essential domains of the penetration testing process. This CompTIA PenTest+ certification exam domain covers a weightage of 16%, and the domain will cover numerous code analysis methodologies and penetration testing tools.
The ability to adapt to the ever-changing digital environment distinguishes a good Penetration Tester from a mediocre one. The ability to create, expand, and manipulate scripts and codes encountered in the field is one component of this adaptability. This domain delves into a variety of code and scripting languages that a Penetration Tester might come across when doing penetration testing.
Penetration Testers should know how and when to use penetration testing tools to detect potential vulnerabilities and security holes and protect the organizations and cyber world from these security issues. The domain will further delve into the tools used in various phases of the penetration test.
The domain is further divided into three sections:
- Explain basic concepts of scripting and software development
- Given a scenario, analyze the script or the code sample for use in the penetration test
- Explain the use cases of the following tools during various phases of a penetration test
1. Explain the basic concepts of scripting and software development
Penetration Testers may need to write scripts to automate certain parts of the penetration test, and they may come across exploit code that they must analyze. A Penetration Tester must have a solid grasp of software development concepts. This section covers the fundamentals of software development and coding, and the section includes the knowledge of logic constructs such as loops, conditionals, Boolean operators, string operators, and arithmetic operators.
The data structure is a method of storing and organizing data in order to make it more useful. This section covers the knowledge of many types of data structures, such as JavaScript Object Notation (JSON), key-value, arrays, dictionaries, Comma-Separated Values (CSV), lists, and trees. This section will also cover many common programming concepts, such as libraries, classes, procedures, and functions.
2. Given a scenario, analyze the script or the code sample for use in the penetration test
During a penetration test, the Penetration Tester may be required to read and write code samples. Shells, automation, programming languages, and a Penetration Tester’s capacity to analyze attack code written for various reasons are all covered in this section. It will look at shell coding and scripting, and this will cover the multiple shells as well as how to develop scripts in various scripting languages.
Therefore, this section develops code writing skills in programming languages such as Python, Ruby, Perl, and JavaScript. It includes Bash and PS, and other common shells and scripts. It improves a Penetration Tester’s capacity to examine exploit code written for various reasons, including downloading files, launching remote access, and enumerating users and assets.
By automating processes like replicating tests several times, Penetration Testers may stay on top of security and vulnerability issues in the system at all times. They can also check the effectiveness of functionality whenever a modification is made to the system. As a result, this section delves into the strategies required to automate penetration testing tasks, such as scripting to change IP addresses throughout a test and Nmap scripting to enumerate ciphers and generate reports.
3. Explain the use cases of the following tools during various phases of a penetration test
A Penetration Tester’s ability to build and use tools in several scripting languages is critical, whether tools exist to fulfill a task or one needs to be created to take advantage of a new vulnerability.
The section will go over the tools and how to use them in various phases of penetration testing, highlighting their capabilities. This section will teach how to use the tools for reconnaissance in order to find exploitable or vulnerable targets. This section will go over a variety of tools and their capabilities at different stages of a penetration test. It will also discuss how to use the tools for vulnerability analysis, exfiltration, and, eventually, persistence.
It includes tools in the categories of scanners, credential testing tools, debuggers, wireless tools, web application tools, social engineering tools, cloud tools, steganography tools, networking tools, and a few miscellaneous tools.
CompTIA PenTest+ with InfosecTrain
Penetration testing techniques require the use of tools and code analysis. You can enroll in InfosecTrain’s CompTIA PenTest+ certification training course to learn how to read and write codes to find vulnerabilities and security gaps in a penetration test using various tools. After completing this course, you will have the expertise necessary for a Penetration Tester in terms of code analysis and tools.






 1800-843-7890 (India)
1800-843-7890 (India)