(ISC)² ® CSSLP Domain 3: Secure Software Architecture and Design (14%)

Domains of (ISC)² ® CSSLP
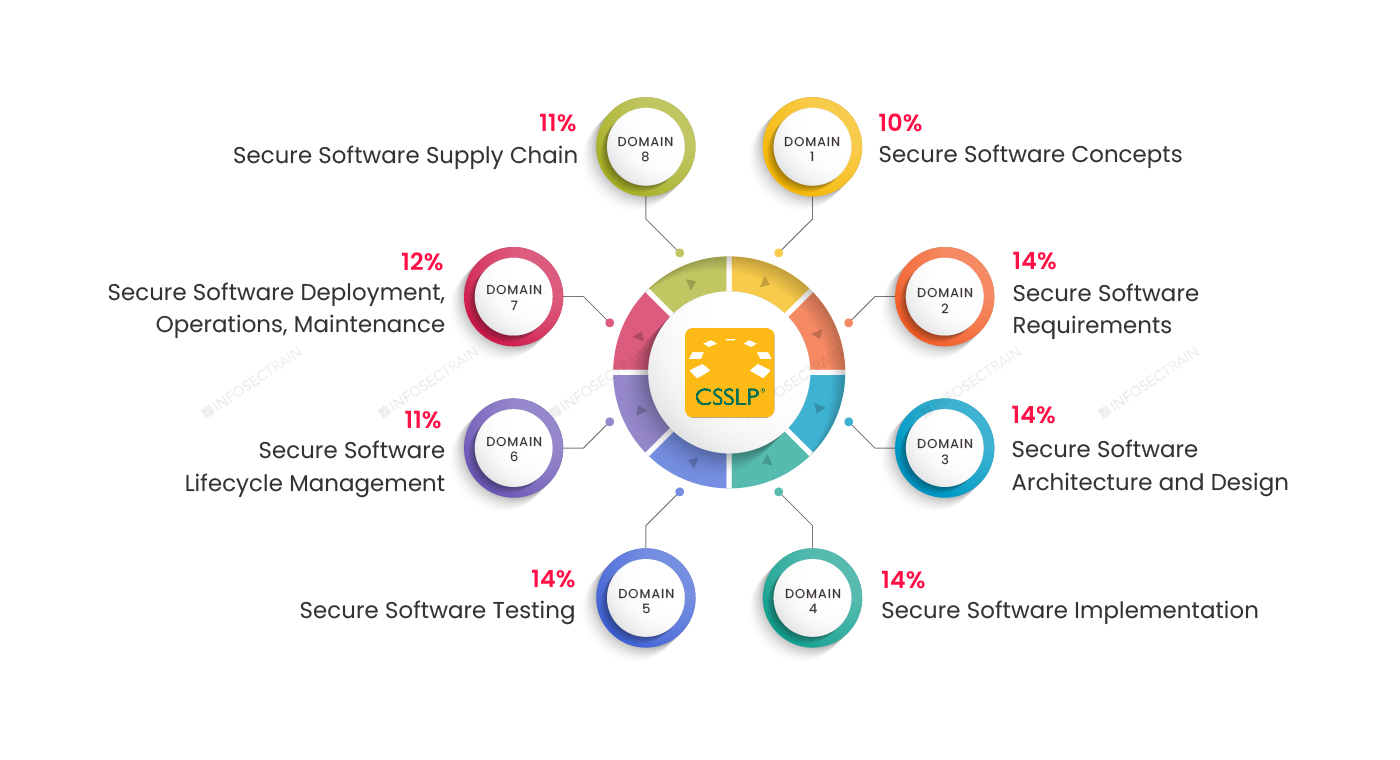
Domain 1: Secure Software Concepts (10%)
Domain 2: Secure Software Requirements (14%)
Domain 3: Secure Software Architecture and Design (14%)
Domain 4: Secure Software Implementation (14%)
Domain 5: Secure Software Testing (14%)
Domain 6: Secure Software Lifecycle Management (11%)
Domain 7: Secure Software Deployment, Operations, Maintenance (12%)
Domain 8: Secure Software Supply Chain (11%)
This article provides an overview of (ISC)² ® CSSLP Domain 3: Secure Software Architecture and Design (14%).
Domain 3: Secure Software Architecture and Design (14%)
This domain contains 14% weightage of the CSSLP exam. This domain focuses on secure software architecture and design. It explains the importance of secure architecture and design, identifying and managing security risks to an application. It explains the risk management and implementation of software design and architecture. It walks you through the various software architectures available and explains the security benefits. The following are the main aspects of this domain:
- Perform threat modeling
- Define the security architecture
- Performing secure interface design
- Performing architectural risk assessment
- Model (non-functional) security properties and constraints
- Model and classify data
- Evaluate and select reusable secure design
- Perform security architecture and design review
- Define secure operational architecture
- Use secure architecture and design principles, patterns, and tools
1.Perform threat modeling
The process of threat modeling entails identifying potential software security threats. This subsection explains common threats like insider threats, Advanced Persistent Threats (APT), and common malware. This section defines the attack surface evaluation and threat intelligence and determines which dangers are credible and relevant.
2. Define the security architecture
This section delves into the process of security control identification and prioritization. The security measures are meant to prevent the vulnerabilities identified during threat modeling, which is included in the software’s security architecture. These measures also depend on the software’s work situation and its threats. This section covers service-oriented architecture (SOA), distributed computing, Radio Frequency Identification (RFID), etc. This section also discusses Field-Programmable Gate Array (FPGA) security features and microcontroller security in embedded systems.
3. Performing secure interface design
A secure interface means connecting software to the user safely; also, interfaces are a common source of security weaknesses. These interfaces must be created in accordance with software security best practices (such as input validation and sanitization) and make proper use of any requirements. This subsection will learn about different security management interfaces like Out-of-Bond (OOB) management and log interfaces. Also, the section covers concepts like upstream/downstream dependencies (key data sharing between applications) and protocol design choices (Application Programming Interfaces APIs), and different weaknesses, states, and models.
Additionally, when designing any user-facing interface, even elements like design logos play a role in ensuring users can easily identify secure and authentic services, reducing potential security risks like phishing.
4. Performing architectural risk assessment
This section delves into the ideas behind the software architectural risk assessment approach. Any software’s design and architecture, as well as its security, introduce vulnerabilities and consequences. Before initiating software development, an architectural risk assessment process evaluates and detects those vulnerabilities, allowing them to be managed and controlled.
5. Model (non-functional) security properties and constraints
Non-functional security features and restrictions cannot be assessed and tested during the development process. These non-functional models must ensure that the current security procedures adequately control the risk. This section explains the process of the model (non-functional) security properties and its constraints.
6. Model and classify data
The model and classified data domain underline the security risk and potential data leaks in the software development process. When software processes any kind of data or information, it exposes the user to various security concerns. As a result, you’ll learn in this section that the data or information processed by the software must be modeled and categorized to facilitate future testing and ensure that critical data is protected safely and effectively.
7. Evaluate and select reusable secure design
This CSSLP domain 3 subtopic will teach you how to use X.509 certificates for credential management in software-defined infrastructures, such as flow controls (firewalls, protocols, queuing), Data Loss Prevention (DLP), and virtualization. Also, identify and integrate the appropriate security technologies for the solution after creating the application and security architecture.
8. Perform security architecture and design review
This subtopic explains that after the security architecture design is completed, the design is subjected to a design review. This aids in ensuring that the architecture and design comply with software security requirements and that all detected security threats are adequately addressed and resolved.
9. Define secure operational architecture
The secure operational architecture, such as deployment topologies and operational interfaces, is discussed in this section. This indicates the program will be used in operational settings, which has security implications. In this context, the deployment topology and operational interface ensure that the program integrates securely.
10. Use secure architecture and design principles, patterns, and tools
When an application software is designed and developed, the essential thing to consider is that it follows security best practices and uses available tools to identify and correct any potential vulnerability errors. In this section, you’ll learn how to develop application software using secure architecture and design principles, patterns, and tools.
CSSLP with InfosecTrain
When it comes to software development, it’s no longer just about coding; it’s about developing secure code to minimize weaknesses. The CSSLP certification verifies that you have the advanced skills to design, develop, and implement security processes across the SDLC. The CSSLP course from InfoSecTrain is spread out and covers all eight domains of the CSSLP certification. So, check out InfosecTrain.







 1800-843-7890 (India)
1800-843-7890 (India)