(ISC)² ® CSSLP Domain 4: Secure Software Implementation (14%)

Domains of (ISC)² ® CSSLP
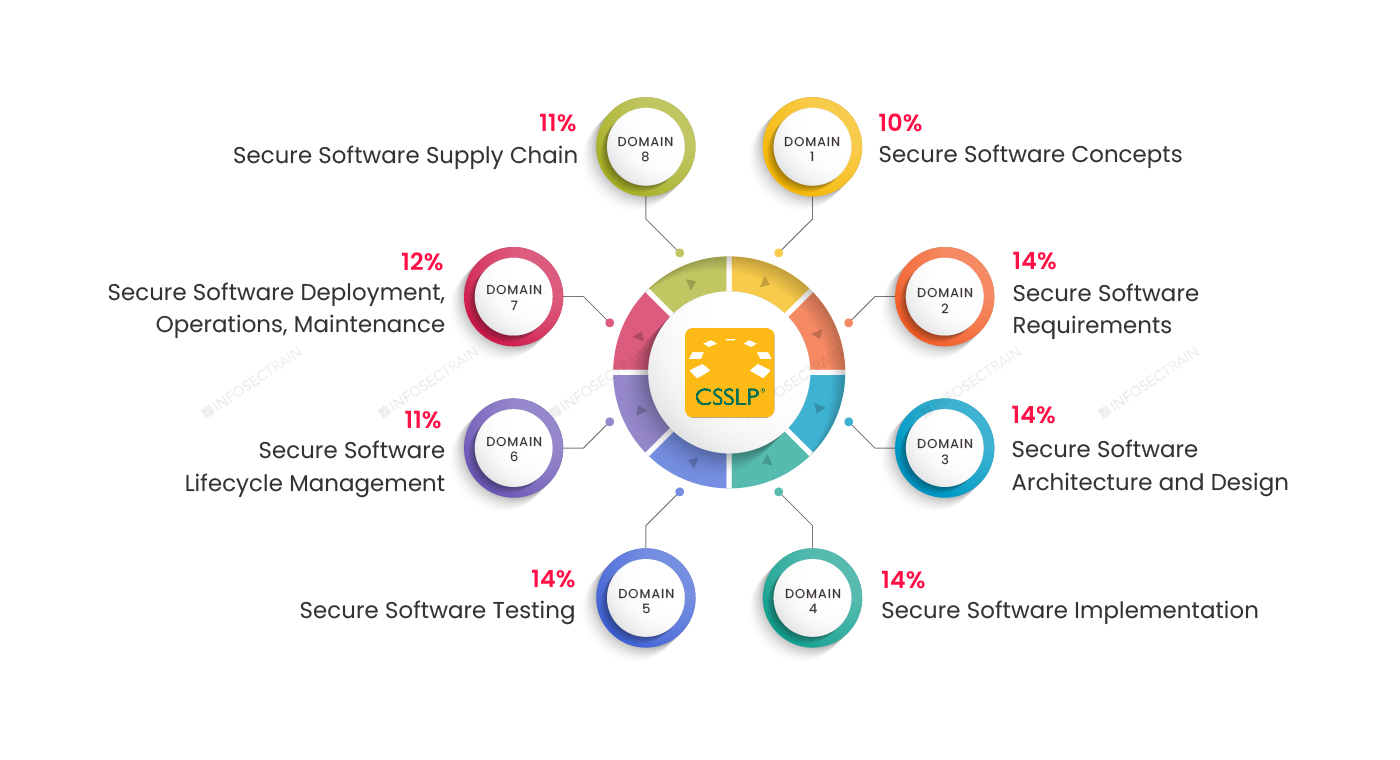
Domain 1: Secure Software Concepts (10%)
Domain 2: Secure Software Requirements (14%)
Domain 3: Secure Software Architecture and Design (14%)
Domain 4: Secure Software Implementation (14%)
Domain 5: Secure Software Testing (14%)
Domain 6: Secure Software Lifecycle Management (11%)
Domain 7: Secure Software Deployment, Operations, Maintenance (12%)
Domain 8: Secure Software Supply Chain (11%)
This article provides an overview of (ISC)² ® CSSLP Domain 4: Secure Software Implementation (14%).
Domain 4: Secure Software Implementation (14%)
The fourth domain of the CSSLP certification exam is a secure software implementation, and the domain comprises 14% exam weightage. This domain covers the most significant security challenges and concerns for developers to consider while writing code. This domain explains declarative vs. mandatory (programmatic) security, Sanitization of output (encoding, obfuscation), Auditing and logging in a secure manner, Dynamic Application Security Testing (DAST), and Interactive Application Security Testing (IAST), Compiler switches, and address compiler warnings.
The CSSLP certification exam’s fourth domain covers the following subtopics:
- Adhere to relevant secure coding practices
- Analyze code for security risks
- Implement security codes
- Address security risks
- Securely reuse third-party code or libraries
- Securely integrate components
- Apply security during the build process
1.Adhere to relevant secure coding practices
This subtopic explains that there are best practices for each component of an application that must be followed throughout the development lifecycle. You will learn why it is critical to validate and sanitize user input, handle errors and exceptions effectively, and design a secure logging and auditing mechanism. This subtopic also introduced you to Application Programming Interfaces (APIs) and trusted and untrusted libraries, resource management, secure configuration management, tokenization, isolation, cryptography, Dynamic Application Security Testing (DAST), etc.
2. Analyze code for security risks
This subtopic emphasizes the need to reuse secure code during the development lifecycle to implement secure code. You’ll learn that reusing code rather than writing new code is the best practice because it might lead to proper security controls. You’ll discover that code should be examined for vulnerabilities utilizing Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), manual code review, and Interactive Application Security Testing (IAST) during the development process.
3. Implement security codes
This CSSLP domain 4 subtopic describes why security code implementation is critical for the development lifecycle. It discusses how changing the code of an application might affect the application’s security and the security of its users. File integrity monitoring (FIM), watchdogs, and anti-malware solutions are used to address this issue.
4. Address security risks
An application’s security flaws may be discovered throughout the secure software lifecycle. These vulnerabilities are analyzed, remediated, neutralized, translated, and accepted in this part in accordance with industry security standards.
5. Securely reuse third-party code or libraries
The reuse of third-party code or libraries is the subject of this section. Every secure development process necessitates vulnerability assessment via Software Composition Analysis (SCA) when using secure external code.
6. Securely integrate components
A piece of software comprises various system components brought together through an interface. This section explains how these components should be safely integrated using trust contracts and security testing and analysis.
7. Apply security during the build process
During the code build process, code tampering, improper compiler switches, and other factors affect the security of the final software development process. So this section explains how to use anti-tampering techniques (code signing, obfuscation), compiler switches, and address compiler warnings.
CSSLP with InfosecTrain
When it comes to software development, it’s no longer just about coding; it’s about building secure code to minimize software development weaknesses. The CSSLP certification validates your advanced expertise in designing, developing, and implementing security processes throughout the SDLC. InfoSecTrain’s CSSLP course is spread out and covers all eight domains of the CSSLP certification. So, take a look at InfosecTrain.







 1800-843-7890 (India)
1800-843-7890 (India)