(ISC)² ® CSSLP Domain 8: Secure Software Supply Chain (11%)
Today every part of our digital world is affected by data breaches, hacks, and other security incidents. It is critical to incorporate security into every aspect of the software life cycle to prevent these incidents, and this is what the CSSLP certification from (ISC)² ® accomplishes.

The Certified Secure Software Lifecycle Professional (CSSLP) certification was introduced by the International Information System Security Certification Consortium (ISC)² ® in 2008. It is a vendor-independent certification. The CSSLP certification validates the certified professional’s ability to apply best security practices, auditing, and authorization to all phases of the SDLC or Software Development Lifecycle. The SDLC includes software design, implementation, testing, and deployment phases.
Domains of (ISC)² ® CSSLP
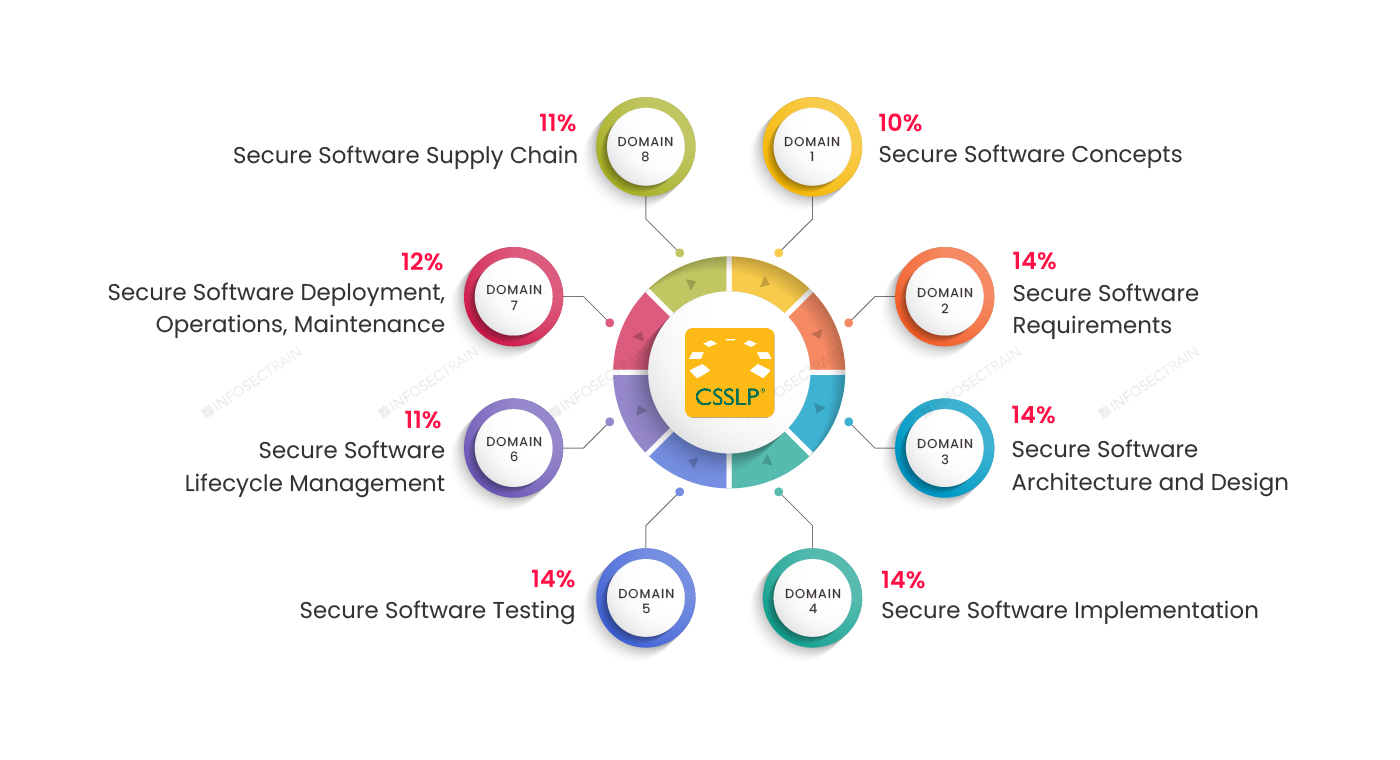
Domain 1: Secure Software Concepts (10%)
Domain 2: Secure Software Requirements (14%)
Domain 3: Secure Software Architecture and Design (14%)
Domain 4: Secure Software Implementation (14%)
Domain 5: Secure Software Testing (14%)
Domain 6: Secure Software Lifecycle Management (11%)
Domain 7: Secure Software Deployment, Operations, Maintenance (12%)
Domain 8: Secure Software Supply Chain (11%)
This article provides an overview of (ISC)² ® CSSLP Domain 8: Secure Software Supply Chain (11%).
Domain 8: Secure Software Supply Chain (11%)
This domain of CSSLP contains 11% exam weightage. It discusses implementing software supply chain risk management and assesses third-party software security. It also explains how to guarantee supplier security criteria are met during procurement.
- Open-source software (OSS)
- Commercial off-the-shelf (COTS) software
- SaaS, PaaS, and IaaS are examples of as-a-service providers.
This domain aims to concentrate on supply chain stakeholders who may impact your software or application in the future.
This domain is further divided into:
- Implement software supply chain risk management
- Analyze the security of the third-party software
- Verify pedigree and provenance
- Ensure supplier security requirements in the acquisition process
- Support contractual requirements
1. Implement software supply chain risk management
Risk management in the software supply chain is critical to creating a secure software supply chain. This section describes how to carry out the processes of software supply chain risk management processes, which include identifying, assessing, responding, and monitoring.
2. Analyze the security of the third-party software
It is practically impossible to avoid using third-party software in the secure software development lifecycle, as it analyzes security third-party software security.
3. Verify pedigree and provenance
Provenance and Pedigree Identify the origin and the chain of evidence to control system risk if either the origin or the chain of evidence is breached. This section covers secure transfer (e.g., interdiction mitigation), system sharing/interconnections, code repository safety, build environment security, cryptographically hashed, digitally-signed components, and audit rights.
4. Ensure supplier security requirements in the acquisition process
This section ensures third-party software security requirements during the acquisition process, including an audit of security policy compliance (e.g., secure software development practices), vulnerability/incident, response, notification, reporting, and coordination, security track record, and maintenance and support structure (e.g., community versus commercial, licensing).
5. Support contractual requirements
This section delves into the contractual agreements involved in the secure software development lifecycle. In this section, you will learn how to support contractual agreements that may have an influence on the software supply chain and, if necessary, explain them.
CSSLP with InfosecTrain
If you’ve decided to advance your career, InfosecTrain’s CSSLP certification training course can help. This course will provide you with professional skills as well as a complete understanding of the Software Development Life Cycle. The course will be led by highly skilled and experienced trainers. The CSSLP certification training courses will help you enhance your software development security profession and improve your abilities.







 1800-843-7890 (India)
1800-843-7890 (India)