Demystified CEH Module 10: Denial-of-Service Attack
Denial-of-Service (DoS) attacks are a critical concern in cybersecurity, aiming to disrupt network services by overwhelming traffic. CEH Module 10 focuses on these attacks, exploring techniques like volumetric, protocol, and application-layer attacks. By studying real-world incidents, such as the 2016 Dyn and 2018 GitHub DDoS attacks, learners gain insights into the scale and complexity of these threats. This module emphasizes proactive detection, robust DDoS mitigation strategies, and network defense mechanisms, preparing cybersecurity professionals to safeguard against these potent disruptions and ensure continuous service availability.

What is Denial-of-Service (DoS) Attack?
In a Denial of Service (DoS) attack, the attacker typically generates an overwhelming number of requests to the target system from a single source. Imagine it like one person constantly refreshing a webpage so aggressively that the server gets bogged down, and legitimate users can’t access it. This overwhelming number of requests overwhelms the server’s resources, including bandwidth, memory, and processing capabilities, rendering it incapable of responding to authorized user requests. As the attack comes from a single source, it is generally easier to identify and block compared to the more complex Distributed Denial of Service (DDoS) attack, which involves multiple sources. The primary goal is to overwhelm and disrupt the system rather than to steal data.
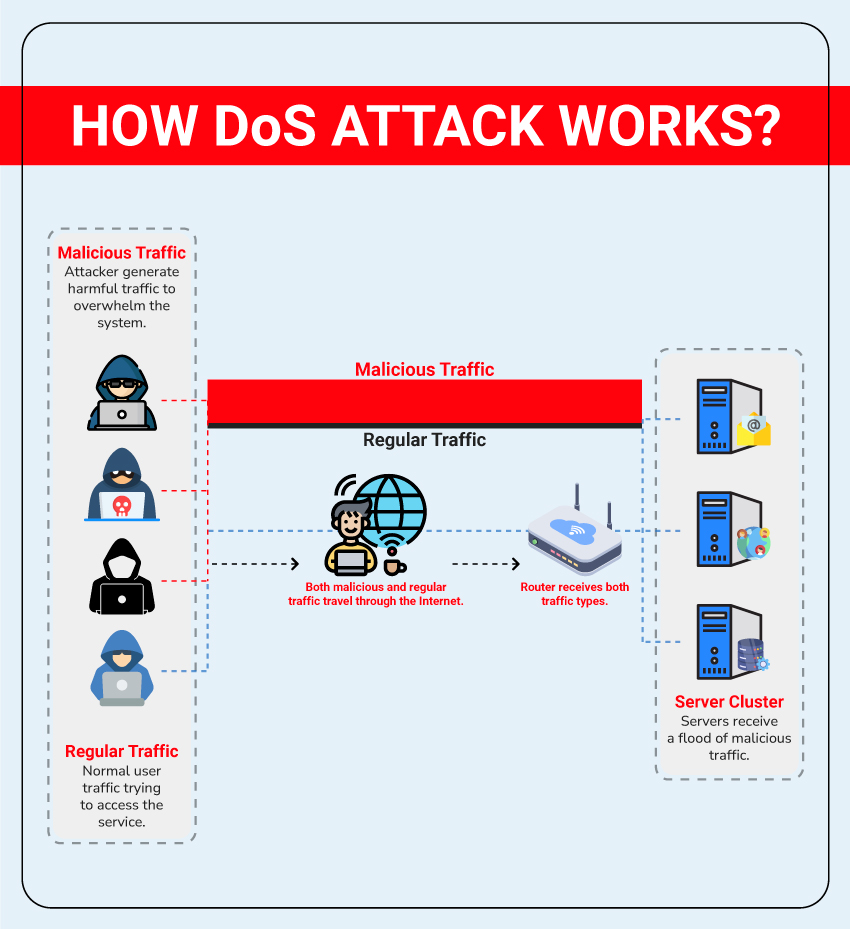
Understanding the Tactics of a DoS Attack: How Attackers Disrupt Systems
- Traffic Flooding: Attackers send an enormous number of requests to a target website or server from a single source. This deluge of traffic exhausts the system’s bandwidth and processing power, causing it to crash. It’s akin to a narrow street jammed with so many cars that nothing can move, leaving legitimate users unable to access the site.
- Service Overload: In this method, attackers overwhelm a specific service, like an Internet Relay Chat (IRC) server, by sending far more requests or messages than it can handle. This results in the service failing or becoming unresponsive, effectively locking out genuine users.
- Corrupt Packets: Attackers send a stream of corrupted data packets to the target system. These packets are designed to exploit vulnerabilities in the system’s TCP/IP stack, causing it to crash or freeze. Think of it as someone sending files to your computer that, when opened, force it to shut down.
- Unexpected Interactions: Here, attackers interact with the target system in unconventional or unanticipated ways, taking advantage of software bugs. This is like pressing all the buttons on an elevator simultaneously, causing it to malfunction and disrupt its intended operation.
- Infinite Loop: By sending commands or requests that exploit specific vulnerabilities, attackers can cause the target system to enter an infinite loop. This consumes its resources and renders it unresponsive, akin to a program stuck in a task it can never complete.
What is DDoS Attack?
A Distributed Denial of Service (DDoS) attack is a large-scale, coordinated effort to disrupt the availability of services on a target’s system or network. This is done by overwhelming the target with a flood of traffic, using many compromised computers (called botnets) connected to the internet.
How Does a DDoS Attack Work?
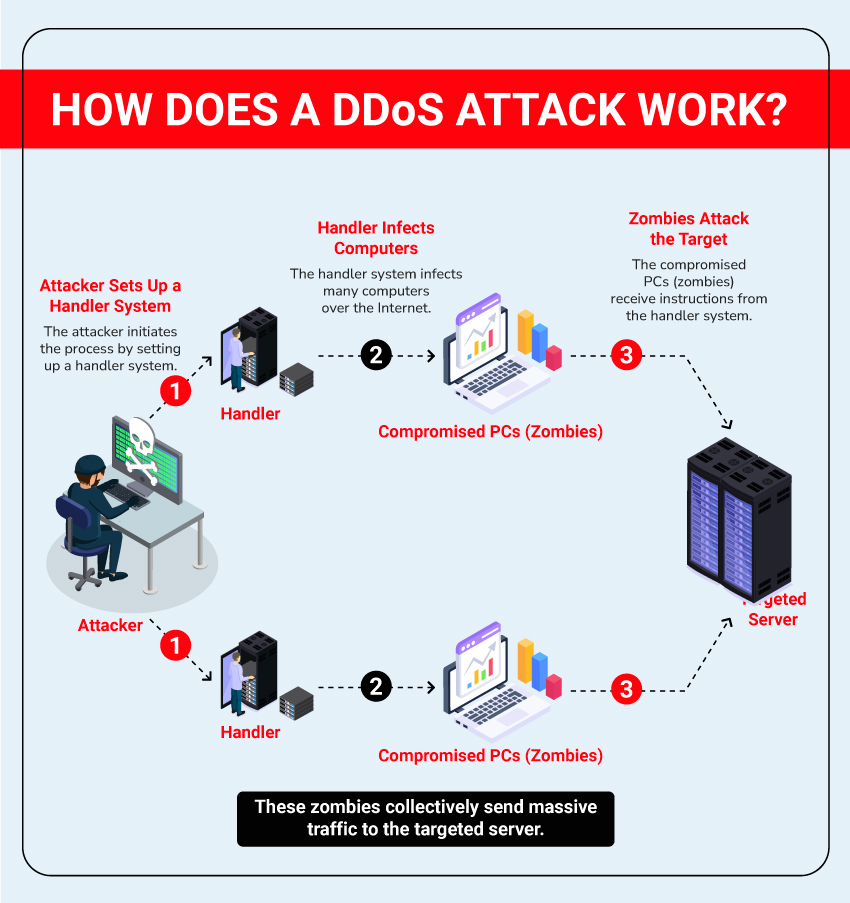
- Using Multiple Computers: A DDoS attack employs many computers to launch a coordinated attack against one or more targets. These computers, often unknowingly controlled by the attacker, are used to send an overwhelming amount of traffic to the victim’s system.
- Harnessing Resources: By using the resources of multiple computers, the attacker can significantly amplify the effectiveness of the attack. These computers act as platforms from which the attack is launched.
- Overloading the System: The flood of incoming traffic overwhelms the target system, consuming its resources and forcing it to shut down or become unresponsive. This denies service to legitimate users trying to access the system.
What are Botnets?
Bots are compromised servers or systems that attackers can control remotely to perform malicious activities. When multiple bots are grouped together under the control of a single attacker, they form what is known as a botnet. A botnet is not the hidden network itself but is controlled through a covert channel, often managed by a Command & Control (C&C) server. This C&C infrastructure enables attackers to coordinate and execute large-scale cybercrimes remotely.
Botnets significantly amplify cybercriminal operations by facilitating activities such as malware distribution, phishing campaigns, and launching massive Denial of Service (DoS) or Distributed Denial of Service (DDoS) attacks. Cybercriminals deploy malicious software like Trojans, viruses, or keyloggers to compromise systems and recruit them into botnets, often without the system owners’ knowledge. These covert networks are challenging to detect and dismantle, as the Command & Control servers obscure the original attacker’s identity and intentions.
The rise of botnets highlights the critical need for robust cybersecurity defenses, as they play a pivotal role in enabling malware development, bulletproof hosting services, and other elements of the cybercriminal economy.
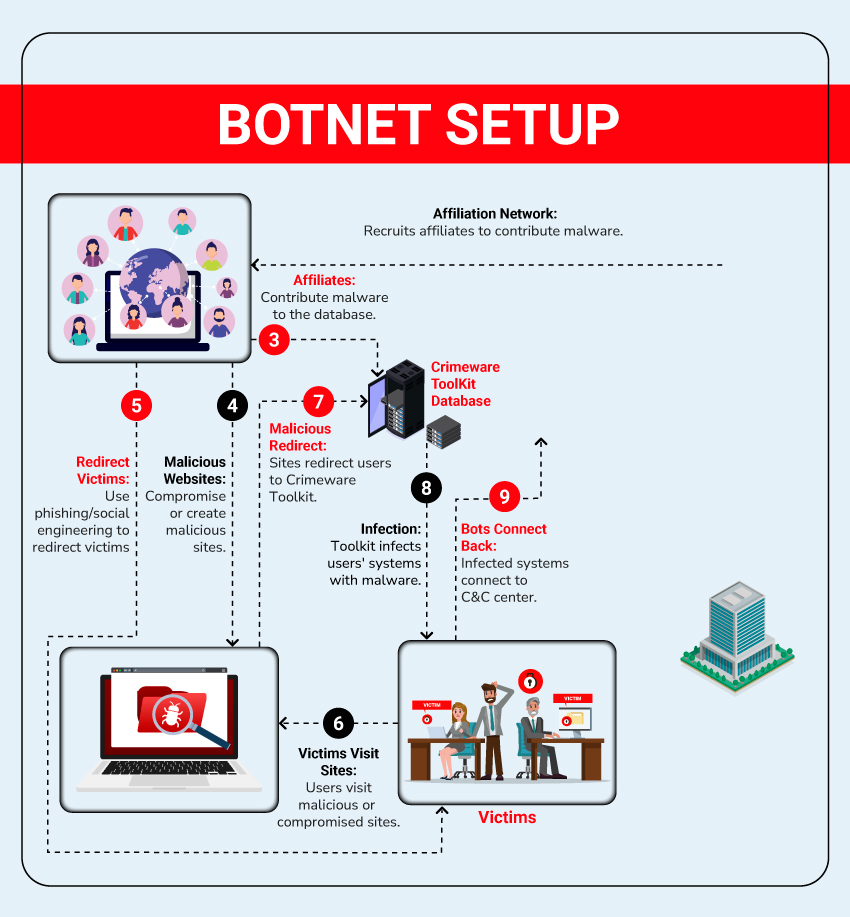
Attackers use botnets for various malicious activities, including:
- DDoS Attacks: Overloading a target’s system to consume its bandwidth and disrupt services.
- Spamming: Using infected computers to send a massive amount of unsolicited emails.
- Sniffing Traffic: Capturing sensitive data like credit card numbers and passwords from compromised machines.
- Keylogging: Recording keystrokes to steal sensitive information such as passwords and account details.
- Spreading New Malware: Distributing additional malicious software through infected computers.
- Installing Ad Add-ons: Conducting click fraud by automatically clicking on ads to generate revenue.
DoS/DDoS Techniques
Basic categories of DoS/DDoS attack vectors influence:
Volumetric Attacks
- Purpose: To overwhelm the bandwidth of a target network or service, making it unavailable.
- Measurement: These attacks are measured in bits-per-second (bps).
- Types:
- Flood Attacks: Sending massive amounts of data to flood the network.
- Amplification Attacks: Using small requests that generate large responses, overwhelming the target.
- Techniques:
- UDP Flood Attack: Overloading the network with User Datagram Protocol packets.
- ICMP Flood Attack: Overloading the network with Internet Control Message Protocol packets.
- Ping of Death and Smurf Attack: Sending malformed or large packets to crash the system.
- Pulse Wave and Zero-Day Attack: Using new or unpatched vulnerabilities to attack.
Protocol Attacks
- Purpose: To exhaust resources like connection state tables in network infrastructure components (e.g., load balancers, firewalls, application servers).
- Measurement: These attacks are measured in packets-per-second (pps).
- Types:
- SYN Flood Attack: Exploiting the TCP handshake process to consume resources.
- Fragmentation Attack: Sending fragmented packets that cannot be reassembled.
- Spoofed Session Flood Attack: Sending fake session requests to exhaust server resources.
- ACK Flood Attack: Flooding the server with acknowledgement packets.
- TCP SACK Panic Attack: Exploiting vulnerabilities in TCP Selective Acknowledgment.
Application Layer Attacks
- Purpose: To consume resources or services of an application, making it unavailable to legitimate users.
- Measurement: These attacks are measured in requests-per-second (rps).
- Types:
- HTTP GET/POST Attack: Overloading the server with HTTP requests.
- Slowloris Attack: Holding connections open with partial HTTP requests to exhaust resources.
- UDP Application Layer Flood Attack: Overloading the application layer with UDP packets.
- DDoS Extortion Attack: Demanding ransom to stop the attack.
DoS/DDoS Countermeasures
- Protect Secondary Victims: Safeguard the computers that could be hijacked and used to launch attacks.
- Detect and Neutralize Handlers: Find and disable the control systems that manage the attack.
- Prevent Potential Attacks: Implement measures to stop attacks before they happen.
- Deflect Attacks: Redirect the attack traffic away from the target to minimize impact.
- Mitigate Attacks: Reduce the severity and impact of the attack once it has started.
- Post-Attack Forensics: Analyze the attack after it occurs to understand its details and implement measures to prevent future incidents.
Master CEH with InfosecTrain
Understanding and mitigating Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks is essential to ensuring network security and service availability. These increasingly sophisticated attacks demand proactive detection, robust defense mechanisms, and effective mitigation strategies, as emphasized in CEH Module 10.
InfosecTrain’s Certified Ethical Hacker (CEH) training course equips cybersecurity professionals with the skills to identify vulnerabilities, detect attacks, and defend against threats like DoS and DDoS. Through theoretical insights and real-world case studies, this course provides hands-on experience in building resilient security architectures.
With InfosecTrain’s CEH training, you gain the expertise to secure networks, protect assets, and ensure service availability against evolving cyber threats.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 26-Apr-2025 | 01-Jun-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Close ] | |
| 11-May-2025 | 28-Jun-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 31-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 07-Jun-2025 | 13-Jul-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 21-Jun-2025 | 27-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |


 1800-843-7890 (India)
1800-843-7890 (India)