DNS Protocols and Attacks
The Domain Name System, or DNS, is the backbone of the internet, translating human-readable domain names into numerical IP addresses that computers use to locate services and devices worldwide. Despite DNS’s importance, it is susceptible to cyber attacks due to its weaknesses. The purpose of this article is to explain the fundamentals of DNS protocols. It will also go into detail about the most common DNS attacks, along with effective mitigation strategies.

Overview of DNS Protocols
DNS operates as a distributed database hierarchy organized into a tree-like structure. The key components of DNS include:
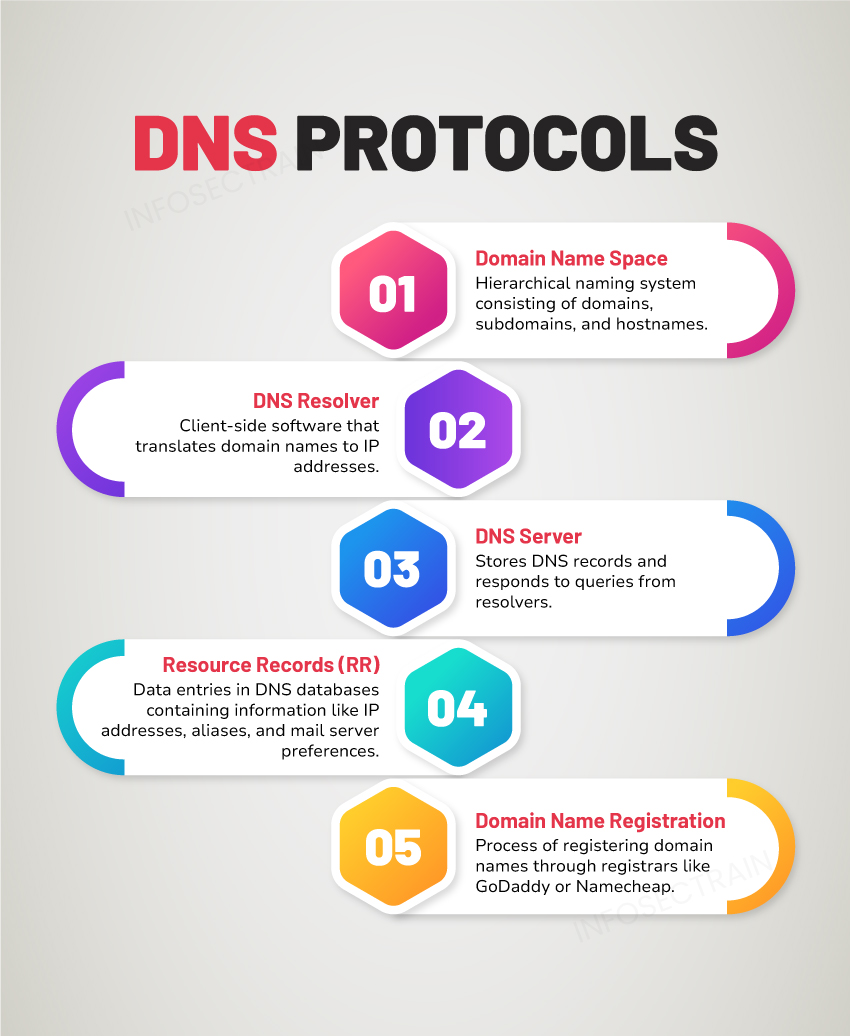
- Domain Name Space: Hierarchical naming system consisting of domains, subdomains, and hostnames.
- DNS Resolver: Client-side software that translates domain names to IP addresses.
- DNS Server: Stores DNS records and responds to queries from resolvers.
- Resource Records (RR): Data entries in DNS databases containing information like IP addresses, aliases, and mail server preferences.
- Domain Name Registration: Process of registering domain names through registrars like GoDaddy or Namecheap.
The DNS resolution process involves iterative and recursive queries between resolvers and authoritative DNS servers until the desired IP address is obtained.
Types of DNS Attacks

1. DNS Spoofing (DNS Cache Poisoning):
Working: DNS spoofing, also known as DNS cache poisoning, involves attackers manipulating the DNS cache of a DNS resolver to redirect users to malicious websites. Attackers exploit vulnerabilities in DNS software or intercept DNS queries to inject false DNS records into the cache. These false records may map legitimate domain names to malicious IP addresses, effectively redirecting users to attacker-controlled servers.
Potential Impacts: DNS spoofing can lead to users unknowingly visiting malicious websites, resulting in various consequences such as phishing attacks, malware distribution, or theft of sensitive information. By poisoning DNS caches, attackers can undermine the trust in the DNS infrastructure and compromise the integrity and confidentiality of data transmitted over the network.
Mitigation Strategies: Implementing DNSSEC (Domain Name System Security Extensions) can help authenticate DNS data and prevent tampering, thus mitigating the risk of DNS spoofing. Additionally, organizations can configure secure DNS resolver settings, regularly monitor and update DNS cache contents, and deploy intrusion detection systems to detect and block spoofed DNS traffic.
2. DNS Amplification:
Working: DNS amplification attacks exploit open DNS servers to generate large volumes of traffic directed towards a target victim. Attackers send small DNS queries to these open DNS servers with spoofed source IP addresses belonging to the victim. The DNS servers then respond with much larger responses, effectively amplifying the volume of traffic directed toward the victim’s network.
Potential Impacts: DNS amplification attacks can overwhelm network bandwidth, leading to service degradation or complete unavailability for legitimate users. The massive influx of traffic can exhaust network resources, causing downtime, financial losses, and damage to reputation.
Mitigation Strategies: To mitigate DNS amplification attacks, organizations can implement ingress filtering to prevent IP address spoofing, configure DNS servers to limit the size of query responses, and deploy traffic scrubbing solutions capable of filtering out malicious DNS traffic. Additionally, maintaining up-to-date DNS server configurations and monitoring DNS traffic for anomalous patterns can aid in detecting and mitigating DNS amplification attacks.
3. DNS Tunneling:
Working: DNS tunneling is a technique used by attackers to bypass network security controls by encapsulating unauthorized data within DNS queries and responses. Attackers exploit DNS protocol features to establish covert communication channels between compromised hosts and external servers, enabling data exfiltration, command and control, or malware propagation without detection.
Potential Impacts: DNS tunneling enables attackers to evade traditional network defenses and establish unauthorized communication channels, facilitating various malicious activities such as data exfiltration, command and control, or malware propagation. By leveraging DNS for covert communication, attackers can bypass network monitoring and detection mechanisms.
Mitigation Strategies: Mitigating DNS tunneling requires implementing DNS traffic monitoring and analysis tools capable of detecting anomalous patterns indicative of tunneling activity. Organizations can enforce DNS query and response size limitations, deploy intrusion detection and prevention systems (IDPS) to detect and block suspicious DNS traffic, and employ DNS firewall solutions to filter and inspect DNS traffic for signs of tunneling activity.
4. Distributed Denial of Service (DDoS) Attacks:
Working: DDoS attacks targeting DNS infrastructure aim to overwhelm DNS servers with a flood of malicious traffic, rendering them inaccessible and disrupting DNS resolution services. Attackers may exploit vulnerabilities in DNS software, abuse misconfigured DNS servers, or utilize botnets to generate massive volumes of DNS queries, leading to service degradation or complete unavailability.
Potential Impacts: DDoS attacks targeting DNS infrastructure can have severe consequences, including disruption of critical online services, financial losses, reputational damage, and regulatory compliance violations. The inability to resolve domain names effectively can result in service downtime and negatively impact user experience.
Mitigation Strategies: Mitigating DNS-based DDoS attacks involves deploying dedicated DDoS mitigation solutions capable of detecting and mitigating volumetric attacks targeting DNS infrastructure. Organizations can leverage distributed DNS infrastructure to distribute query loads and absorb attack traffic, collaborate with Internet Service Providers (ISPs) to implement traffic filtering and rate limiting measures, and maintain redundancy and failover mechanisms to ensure service availability during DDoS attacks. Regularly updating DNS server configurations and monitoring DNS traffic for signs of abnormal behavior can also help detect and mitigate DDoS attacks targeting DNS infrastructure.
Impacts of DNS Attacks
- DNS attacks can render websites, applications, or entire networks inaccessible, leading to financial losses and reputational damage.
- Attackers may redirect traffic to spoofed websites, leading to data theft, credential harvesting, or malware infections.
- DNS attacks erode user trust in online services, impacting customer loyalty and brand reputation.
- Organizations may face penalties for failing to protect sensitive data or maintain uptime standards.
Common Mitigation Strategies:
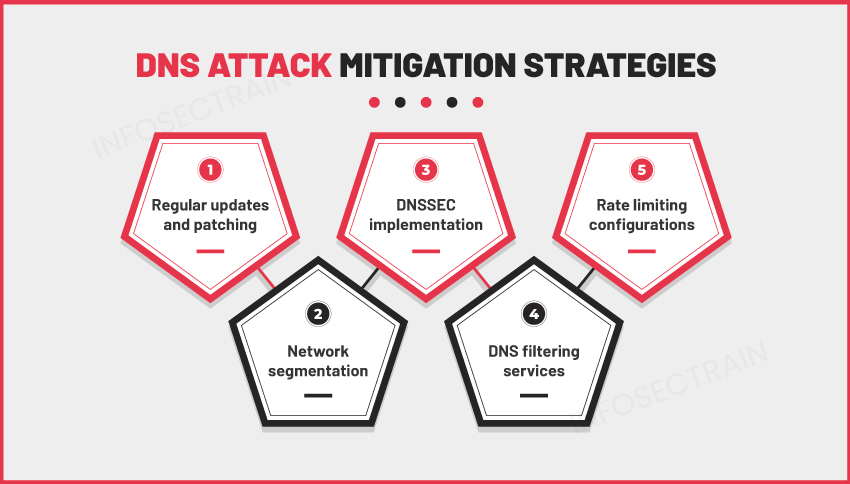
- Regular Updates and Patching: Keeping DNS software and systems updated with security patches to address known vulnerabilities.
- Network Segmentation: Isolating DNS servers from critical network segments to contain the impact of potential attacks.
- DNSSEC (Domain Name System Security Extensions): Implements cryptographic authentication to verify DNS data integrity and prevent DNS spoofing attacks.
- DNS Filtering: Implementing DNS filtering services to block access to malicious domains and prevent malware infections.
- Rate Limiting: Configuring DNS servers to limit the number of queries from individual IP addresses, mitigating DNS amplification and DDoS attacks.
CEH with InfosecTrain
The Domain Name System is a fundamental component of internet infrastructure, but its vulnerabilities expose it to various cyber threats. Understanding the DNS protocol and the diverse array of attacks targeting it is crucial for organizations to implement effective mitigation strategies. By adopting robust security measures and staying vigilant against emerging threats, businesses can safeguard their online presence and protect against potentially devastating DNS attacks.
You can enroll in InfosecTrain’s CompTIA Security+ and CEH certification training courses to learn more about DNS protocols and DNS attacks.
TRAINING CALENDAR of Upcoming Batches For Security+ SY0-701
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 16-Aug-2025 | 28-Sep-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 13-Sep-2025 | 26-Oct-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |







 1800-843-7890 (India)
1800-843-7890 (India)