Domain 3 of AZ-204: Implement Azure Security

Table of Contents
Features of Azure Security
Azure Developer AZ-204 certification comprises a total of five domains
Domain 3 of AZ-204: Implement Azure Security
Implement user authentication and authorization
Implement secure cloud solutions
As we all know, all of our applications are now hosted in the cloud; thus, security is crucial. As a result, Microsoft takes steps to guarantee that our workload, data, and applications are all secure. Every IT organization or company that uses the cloud is concerned about the safety and security of data and its apps in the cloud. Every organization’s security requirements are unique, necessitating numerous adaptations to assure the safety of each workload. Security is critical since every enterprise uses it from one way to another. Protection must be incorporated at every layer of your application stack, starting with computing, storage, and networking and progressing to application-specific controls and identity and access management.
Features of Azure Security
- End-to-End Encryption
- Cost-Effective Compliance
- Segmented Resources Access
- Simple Cloud Migration
- Actionable Intelligence
- Secure Remote Access
Azure Developer AZ-204 certification comprises a total of five domains:
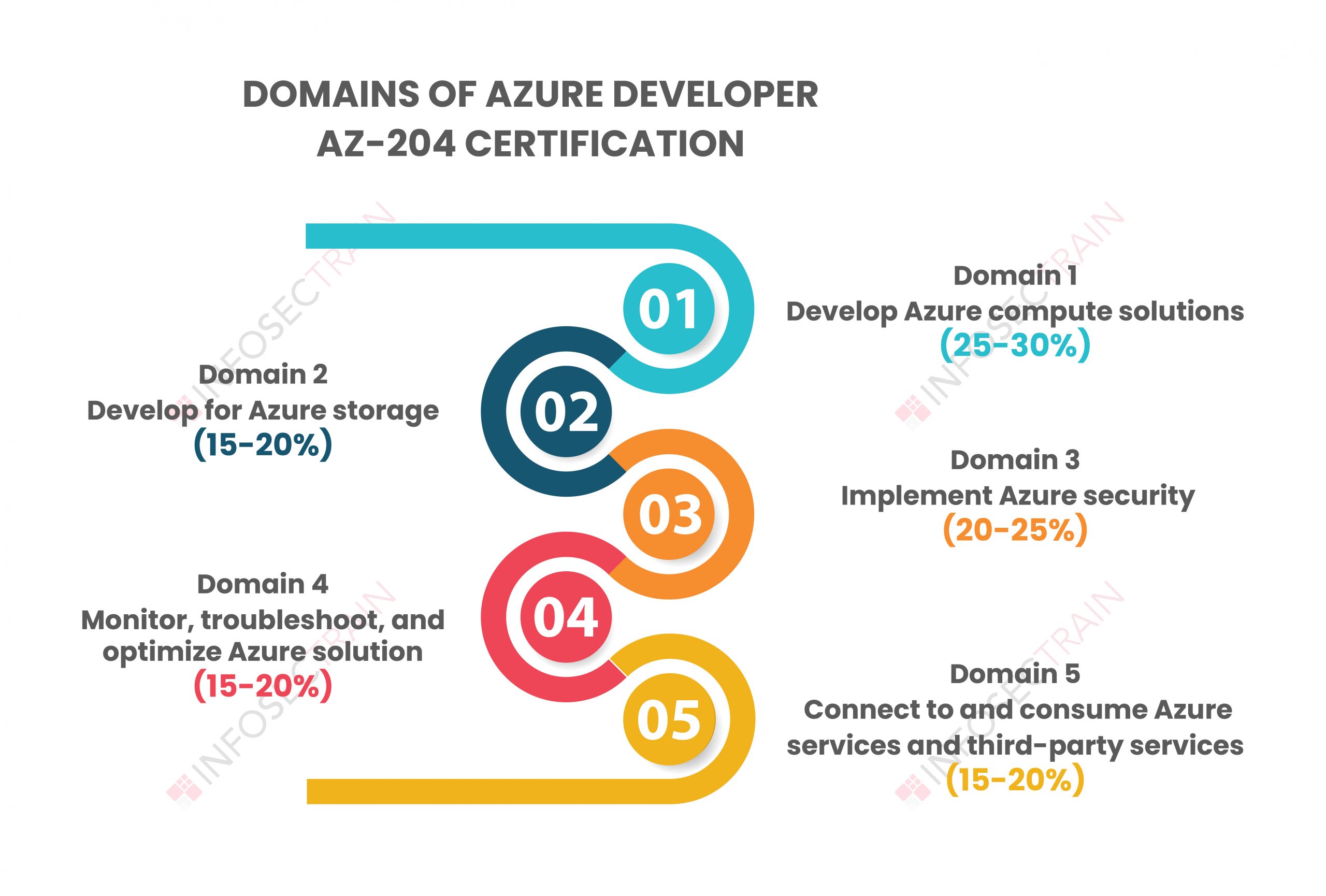
- Domain 1: Develop Azure compute solutions (25-30%)
- Domain 2: Develop for Azure storage (15-20%)
- Domain 3: Implement Azure security (20-25%)
- Domain 4: Monitor, troubleshoot, and optimize Azure solutions (15-20%)
- Domain 5: Connect to and consume Azure services and third-party services (15-20%)
In this article, we will discuss the third domain of AZ-204, “Implement Azure Security.”
Domain 3 of AZ-204: Implement Azure Security
With our cloud solution, Azure Security is more effective, as it allows for monitoring across all of your resources, protecting even the most insignificant data. This domain comprises (20-25%) weightage. This domain will teach you how to design our Azure Security solution with multi-layered protection to simplify businesses to secure their Microsoft Azure cloud settings. Azure offers a wide range of applications and services that you may use and benefit from, as well as security tools and other features. In the cloud, advanced threat vectors necessitate a zero-trust security strategy, in which nothing is trusted by default and must confirm everything. The AZ-204, “Implement Azure Security” certification exam’s third domain includes the following subtopics:
- Implement user authentication and authorization
- Implement secure cloud solutions
Implement user authentication and authorization
This section will teach you the directions of modern identification, how the Microsoft Identity Platform implements them, and how to secure Azure storage in various methods. The Microsoft identity platform is a collection of unified, connected services that developers may utilize to create apps that authenticate a wide range of user accounts. In this section, you’ll learn about the many facilities provided by Azure storage to authenticate and authorize your requests, as well as how the Microsoft Identity Platform with Azure AD extends those capabilities. Microsoft’s cloud-based identity, Azure Active Directory, manages authorization and authentication for internal and external resources. Finally, you’ll learn how to create and implement shared access signatures to grant access to resources, as well as SAS recommended practices. After completing this section, you will have the necessary skills and knowledge to establish authentication and permission.
Implement secure cloud solutions
This section will teach how to use Azure Key Vault, managed identities, and Azure App Configuration to deploy apps more securely in Azure. First, you will learn how to secure your app configuration data by using App Configuration Azure Key Vault. Azure App Configuration is an Azure tool that allows you to consolidate all of your application settings in one place. You will also learn to develop code that uses keys, secrets, and certificates stored in Azure Key Vault. Azure Key Vault is an Azure service that allows you to manage and save your secrets, such as your access token, password, or keys, such as cryptography keys and encryption keys. It also allows you to manage and store your certifications, such as TLS and SSL certificates. Lastly, you will learn to implement solutions that interact with Microsoft Graph. Microsoft Graph is a RESTful web API that allows you to access resources from Microsoft Cloud services.
| Related Article: How to Prepare for the AZ-204 |
AZ-204 Developing Solutions with InfosecTrain
If you prefer to study for this certification, I highly recommend InfosecTrain, which will offer you the examination procedure for the AZ-204 Developing Solutions for Microsoft Azure exam. Obtaining this certification will enable learners to explore and receive access to Azure’s different technical job options. This online course will accompany you on your journey from start to finish.






 1800-843-7890 (India)
1800-843-7890 (India)