Encryption vs. Encoding
Encryption and encoding are the two distinct processes used for data or information transformation, and they serve different purposes. This article will explain these processes in detail and highlight their differences.

What is Encryption?
Encryption is the process of transforming data or information into a secret code that is unintelligible and unreadable to unauthorized individuals and can only be unlocked with a key. It involves using mathematical algorithms and a secret key to transform plaintext (the original, readable data) into ciphertext (the encrypted, unreadable data). It ensures the confidentiality and privacy of sensitive information, making it difficult for unauthorized parties to understand or access the data.
The purpose of encryption is to secure data during data at rest, data in transit, or communication.
- Data at Rest: Encryption protects data that is stored on a computer or other devices, such as a USB drive, hard drive, or cloud storage.
- Data in Transit: Encryption is used to secure data that is transmitted between two devices, such as a laptop and a printer.
- Secure Communication: Encryption is used to protect data that is shared over a network, like email, web browsing, and file transfers.
There are different types of encryption algorithms, such as symmetric and asymmetric encryption.
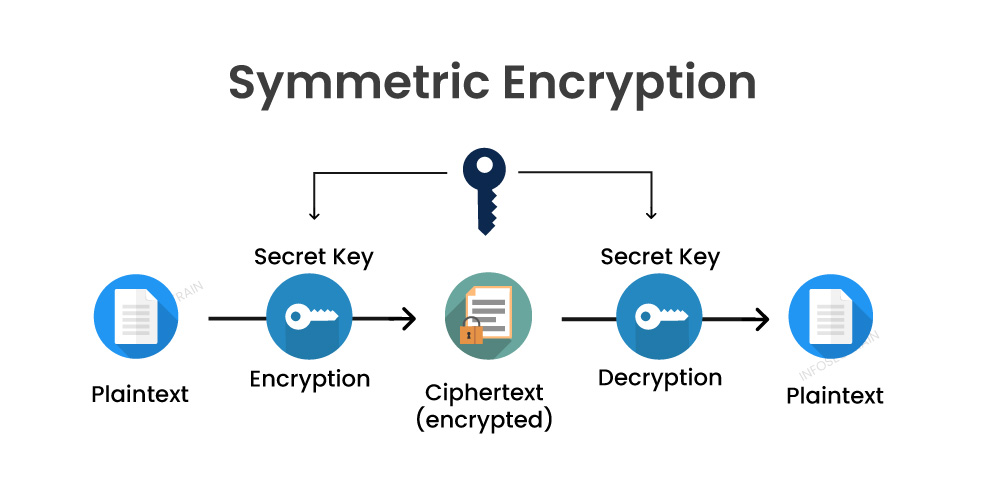
Symmetric Encryption Algorithm
- Advanced Encryption Standard (AES): Widely adopted for security and efficiency.
- Triple DES: Applies DES three times for enhanced security.
- Blowfish: Known for its flexibility and speed.
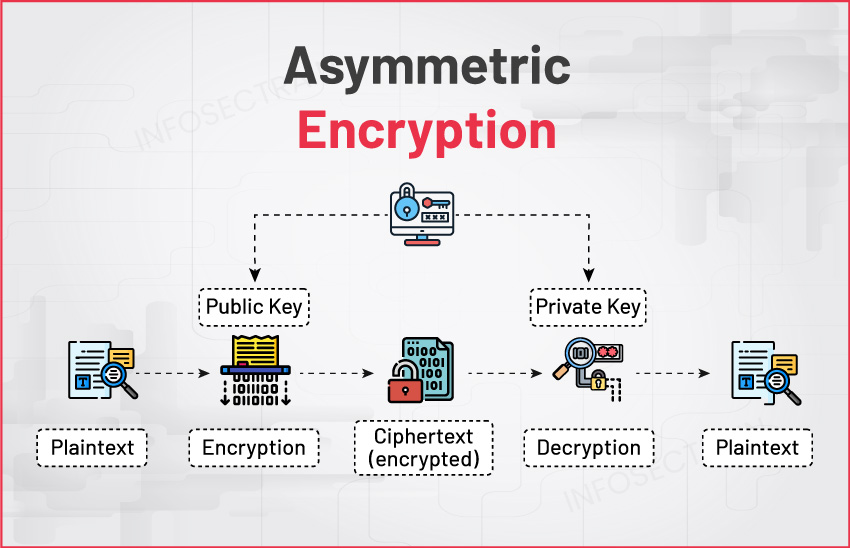
Asymmetric Encryption Algorithm
- Elliptic Curve Cryptography (ECC): Based on elliptic curves, offering strong security with shorter key lengths.
- RSA (Rivest-Shamir-Adleman): Used for key exchange and digital signatures.
- Diffie-Hellman Key Exchange: Secure key exchange protocol without prior communication.
What is Encoding?
Encoding is the process of converting data or information into a specific format or code that can be easily stored, transmitted, or processed by a computer or another entity. It involves the use of specific rules, algorithms, or standards to transform data into a format better suited for a particular purpose or medium.
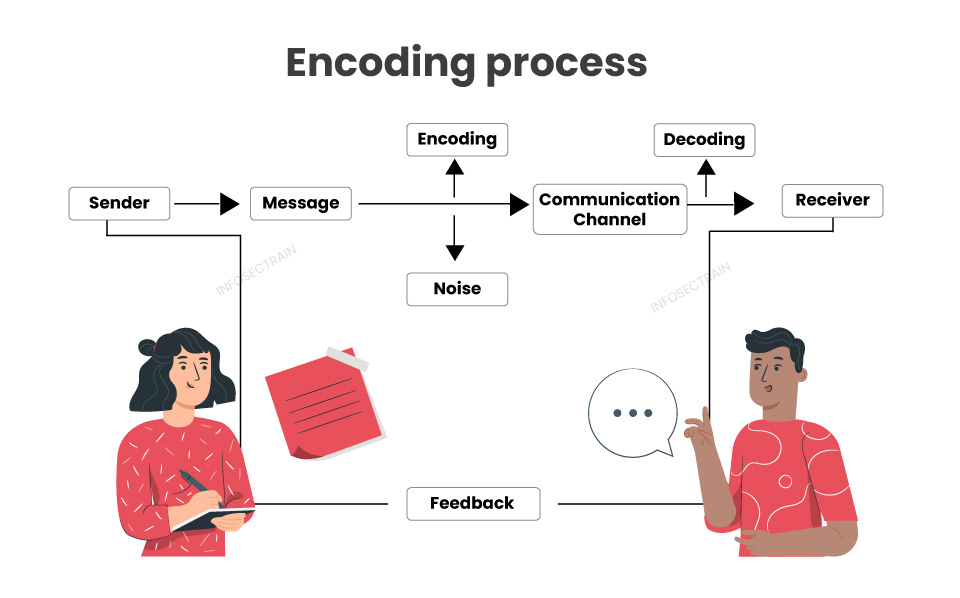
There are many different types of encoding, each with its purpose. Some common types of encoding include:
- Character Encoding: Converts characters and symbols from the character set to unique code. ASCII, UTF-8, and UTF-16 are popular character encodings.
- Image Encoding: Transforms images into a digital format. JPEG, GIF, and PNG are popular image encodings.
- Video Encoding: Converts video signals into a digital format. MPEG-4, H.264, and HEVC are popular video encodings.
- Audio Encoding: Converts sound waves into a digital format. MP3, WAV, WMA, and AAC are popular audio encodings.
Encoding Algorithms
- Base64: Converts binary data into a string of ASCII characters.
- URL Encoding (Percent-encoding): Encodes special characters in a URL.
- Binary: Represents data using a binary representation.
- HTML: Represent special characters and reserved symbols in HTML documents.
- UTF-8: Encodes characters from the Unicode character set.
- UTL: Encodes special characters for safe URL transmission.
Difference Between Encryption and Encoding
Encryption and encoding are both ways of transforming data into a different format. However, they have different purposes and use different methods.
| Basis | Encryption | Encoding |
| Objective | It transforms data or information in such a way that it remains confidential and secure. | It represents or converts data into a specific format or representation to another. |
| Used For | It is used to maintain data confidentiality by converting it into an unreadable form using cryptographic algorithms. | It is used for character representation, multimedia compression, or data format conversions to maintain compatibility, efficiency, or data integrity. |
| Security | Very secure; it can only be decoded with the correct key. | Not secure; it can be easily decoded. |
| Reversibility | It is reversible, but only with the correct decryption key. | It is reversible. |
| Method | It uses an encryption algorithm and a key. | It uses a conversion algorithm. |
| Key Usage | It requires the use of secret keys. | It does not involve the use of secret keys. |
How can InfosecTrain Help?
Enroll in InfosecTrain’s Certified Ethical Hacker (CEH) and Certified Encryption Specialist (ECES) training and certification course. In these online training and certification programs, you will get in-depth knowledge and practical skills in cryptography, encryption, encryption algorithms, and more. ECES training and certification course is suitable for individuals seeking professional certification in encryption. Our experienced and knowledgeable instructors provide the training programs. They are subject-matter experts who can give you in-depth understanding, practical examples, and real-world scenarios to enhance your learning experience.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 11-May-2025 | 28-Jun-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 31-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 07-Jun-2025 | 13-Jul-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 21-Jun-2025 | 27-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 06-Jul-2025 | 16-Aug-2025 | 09:00 - 23:00 IST | Weekend | Online | [ Open ] |







 1800-843-7890 (India)
1800-843-7890 (India)