Everything about the Certified Information Security Auditor

Information security is a process of protecting an organization’s data from unauthorized access or modification to ensure its confidentiality, integrity, and availability.
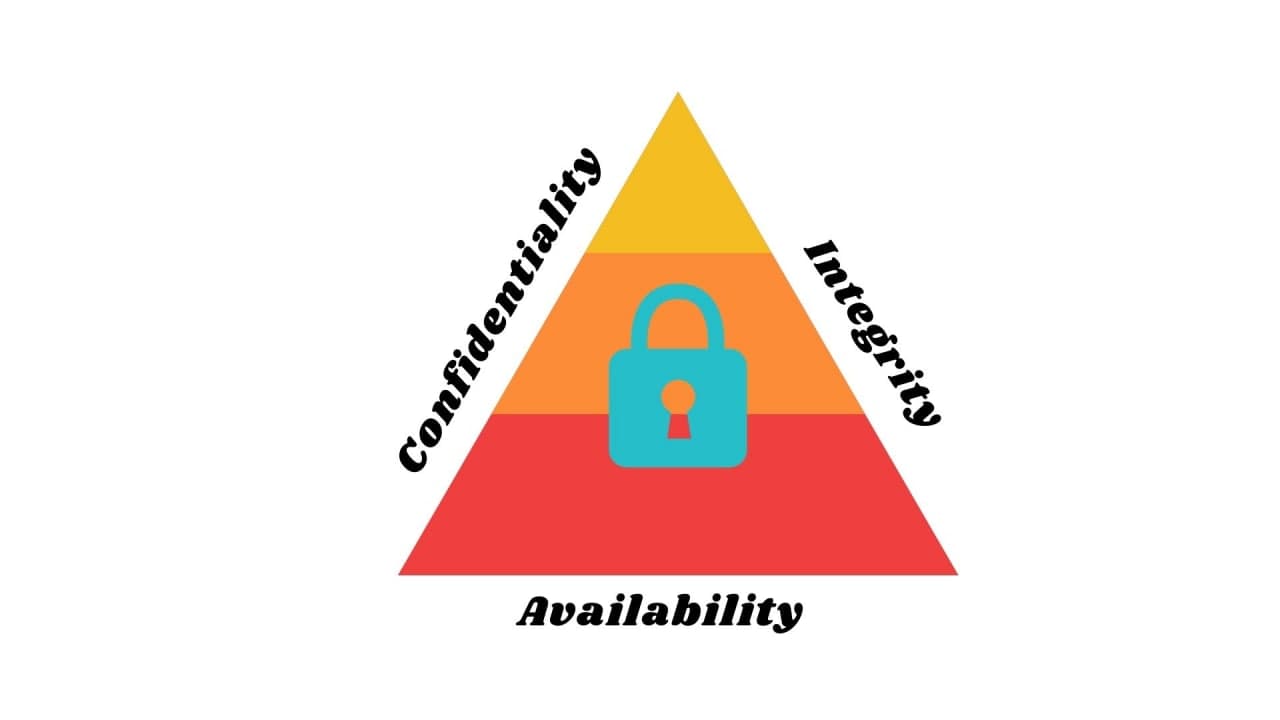
Confidentiality: Confidentiality assures that information assets are confined only to the people with authorized access. Confidentiality also includes Data Encryption, steganography, and access control.
Integrity: Integrity needs all information to be intact, complete, and accurate. Integrity helps to maintain the trustworthiness of company data.
Availability: Availability makes sure systems and services are ready for use as intended for all authorized users, maintaining hardware, and completing repairs immediately.
All the above goals must be considered when developing procedures and policies to protect company data and computer systems.
In this blog, let us discuss how to become a Certified Information Security Auditor and the roles and responsibilities of a Certified Information Security Auditor.
How to become an Information Security Auditor
Below are the few basic steps that one has to follow to become a CISA professional.
Education: To become a successful Information Security Auditor, you must have a degree in IT. It is preferable if you have a degree in the information security side or any equivalent area. But there are many situations where Information Security Auditors aren’t asked for any technical background. So, if you have the correct skills, then your degree can be exempted.
Gain work experience: In addition to audit internships, it is extremely valuable to gain first-hand expertise in related fields (e.g., IT, IT security, and risk management).
Get certified: Getting certified is one of the best options. These days, recruiters are searching for certified professionals because getting a certificate itself takes a lot of knowledge, experience, and hard work. And to get certified, you need training. Try InfosecTrain, the best Information Security Auditor training.
With the above steps, you must possess dedication and passion for your work.
Advantages of hiring a Certified Information Security Auditor
Attack Surfaces can be identified: Certified Information Security Auditors can identify the open ports(Surfaces that are more vulnerable), and their knowledge and experience can be beneficial in closing those ports.
Passwords: Security audits check your company’s password policy. The safety audit trials evaluate all these elements if the passwords follow their strength, change duration, and other criteria.
Open shares: An additional advantage of performing information security audits is exposing open shares. They should be closed if they are no longer needed.
User accounts: Employees who left the organization leave their accounts unused quite often. These accounts are not useful, and it is better to delete them since they may invite ill-intentioned people to take them over.
Applications: As part of a security audit, current applications will be identified, and any potentially dangerous ones will be identified and removed.
Roles and Responsibilities of a Certified Information Security Auditors
CISA professionals are typically highly qualified individuals who are efficient and professional. The Certified Information Security Auditor (CISA) credential gives companies credibility in the compliance auditing process by following best practices and having qualifications in information security.
They must understand standards, practices, and organization processes to understand the organization’s business requirements. By doing so, they understand why some procedures and processes are structured the way they are, which will lead to a greater understanding of the business’s operational needs.
To implement a network audit, the network environment needs to be inspected systematically and methodically so that the audit and reports will be coherent and logical. The auditor should rationalize his or her decisions based on the recommended standards and practices.
The goal is to be aware of any deviations from standards and practices and explain them appropriately. In the planning phase, auditors typically outline the steps they will take to conduct the investigation, so they are unlikely to make any considerable changes to that plan.
About the CISA exam
Anyone interested in IS auditing, control, and security is eligible to take the CISA exam. The test is for four hours and includes 150 multiple-choice questions based on five job practices:
- The Information Systems Auditing Process
- Governance and Management of IT
- Information System Acquisition, Development, and Implementation
- Information Systems Operations and Business Resilience
- Protection of Information Assets
Passing the exam requires a score of 450 (on a scale of 200 to 800). Testing locations are available worldwide; candidates can also take the test remotely online. There are nine exam languages available: English, Chinese Mandarin Simplified, Chinese Traditional, German, Italian, Japanese, Korean, Spanish, and Turkish.
Information Security with InfosecTrain
InfosecTrain is the leading provider of consultancy services, certifications, and training in information technology and cyber safety. Our accredited and skilled trainers will help you understand cybersecurity and information security and improve the skills needed. Not only do they give you the best training, but they will also expose you to new challenges that will be very helpful to you in the coming future. Join InfosecTrain to get the best Information Security training.






 1800-843-7890 (India)
1800-843-7890 (India)