Everything You Need to Know About Microsoft Sentinel
Going to the cloud does not imply that you are free of security concerns. Organizations have a SIEM solution for which they must plan for complexity in the on-premises world, and they must ensure that the hardware is in good working order, among other things. In Azure, they now offer a service called Microsoft Sentinel that does just that. It is a SIEM that is hosted in the cloud, and we can quickly scale it; it contains AI and connects to Azure Active Directory (Azure AD), Office 365, and other systems. This is a fascinating, new, and forward-thinking approach to using what we commonly refer to as a SIEM solution.
Table of Contents
What is Microsoft Sentinel?
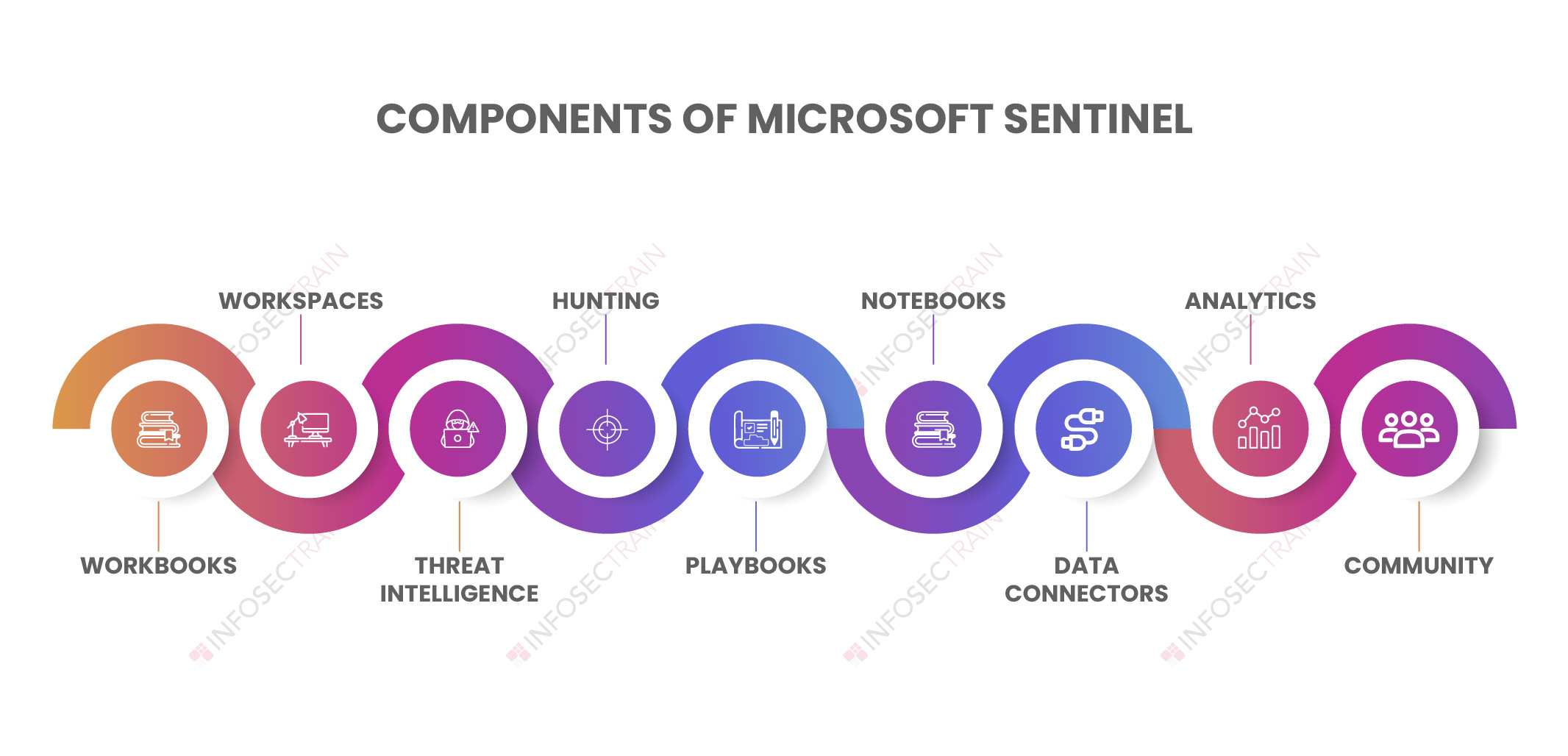
Stages of Microsoft Sentinel
Why is Microsoft Sentinel so vital for a company to think about deploying?
How to deploy Microsoft Sentinel?

We will tell you all there is to know about Microsoft Sentinel in this article. We will go through what it is, why you might need it, and, most importantly, how to use it.
What is Microsoft Sentinel?
Microsoft Azure has a lot of fascinating features and services. Have you ever wondered what the thing is with Microsoft Sentinel? Is it keeping a close watch on your company?
Microsoft Sentinel (formerly known as Azure Sentinel) assists you in promptly detecting, alerting on, investigating, and resolving security events. It can gather data from a variety of sources and analyze it for security concerns and occurrences. It includes tools for analyzing data, creating alarms, and mitigating security risks.
To know more about Microsoft Sentinel you can visit the link below:
Stages of Microsoft Sentinel:
When you consider security, threat, and risk, you think about all the bad things that could happen in your company. These days, the organizational members are likely to be dispersed across the cloud, most likely in a hybrid solution that includes both on-premises and cloud-integrated services, similar to the Azure platform. Any of those places are constantly under attack by a variety of wicked people who wish to seize our possessions.
There are four stages of Microsoft Sentinel:
- Collect
- Detect
- Investigate
- Respond
At the heart of Microsoft Sentinel is our capacity to collect, detect, investigate, and respond to threats, incidents, and cyber attacks. When we consider Microsoft Sentinel, we focus on the fact that it provides us with a cloud-based SIEM (Security Information Event Management) solution that works at scale. SIEM gives us the ability to collect data from a variety of sources, including on-premises, in the cloud, and anywhere else. We can imagine a device or system producing logs, which we want to be aware of and pay attention to as security, threat, and risk management professionals.
We should know what is going on with these systems and be able to create compelling tales about what is going on that the organization should be concerned about. As a result, we receive all of that information and, through the collection, detection, and investigation, we are able to respond. We think of the Microsoft Sentinel product’s lifecycle as a flow, not as something that happens linearly.
Beginning with a grasp of what information is available to us, we can then examine and evaluate the various systems in which that information may reside. We can explore when we see evidence of things that may or may not be unusual but are frequently problematic for us. Finally, we can generate a response to that research, potentially leading us back to engage in more gathering.
Why is Microsoft Sentinel so vital for a company to think about deploying?
It is a complex technology that scales across our business, allowing us to collect and comprehend information and manage events at scale, allowing us to integrate the two and have a lifecycle linked with activity management. What is the significance of this? It is significant because of each of the lifecycle factors we just discussed. When we discuss collecting, we indicate that we could acquire data from a variety of systems, end-points, devices, servers, mobile platforms, and our on-premises, cloud-based infrastructure. It includes not just Azure’s cloud-based infrastructure but multi-cloud infrastructure as well.
Today, the majority of our enterprises rely on cloud systems. Using Microsoft Sentinel and connectors, we can reach out and combine those cloud platforms and pull information in. A true cloud SIEM solution with a worldwide reach that allows us to collect data from wherever and comprehend what we are collecting. Using artificial intelligence, machine learning, and the advanced analytics capabilities that these technologies bring to bear for us, we can detect millions of different events taking place across that landscape in real-time or near real-time. We can integrate the ability to collect and detect and the ability to investigate it.
Again, across that operational picture, Microsoft’s platform has access to artificial intelligence and machine learning and the integrated knowledge and information assessment capabilities that Microsoft’s platform has internationally through threat intelligence aggregation. Not just from organizations’ systems but from every client system that Microsoft supports across the world. In other words, we will reap the advantages of all of the data that Microsoft collects on a daily basis and applies to make sense of our world and teach us how to understand our systems and, when there is a problem, what we need to do to treat, mitigate, and minimize its impact potentially.
Not only can we accomplish this using industry-standard technology, but we can also do it with industry-standard log capabilities. So, syslog and all of the other typical solutions are fed into this platform, which allows us to merge old systems and cloud-native technologies into a single holistic solution. So, when we consider what it is and why we want to use it, it is really all about bringing everything we want to see together, and by the way, it let us minimize those false positives as well, eliminating and filtering out the issues that traditionally cause us to chase them down when they are not all that important.
Artificial intelligence, machine learning capabilities, and large-scale threat assessment capabilities assist us in filtering out false alerts and focusing on the ones that may be a mystery to us but that we must pursue.
How to deploy Microsoft Sentinel?
Let us look at how we get Microsoft Sentinel installed, up and operating, and finally configured. The background services that are necessary to run Microsoft Sentinel are relatively simple to set up. The difficult part is setting Microsoft Sentinel and connecting it to all of the data sources that we would wish to monitor. Let us look at how we are going to get started.
From the portal, we will choose Microsoft Sentinel. We arrive at a section labeled Microsoft Sentinel workspaces.
- Open Microsoft Sentinel
- Build a new Sentinel
- Create Microsoft Sentinel workspace
- Fill in all the details
- Check the information you have entered and then click “Create”
Microsoft Sentinel with InfosecTrain
Microsoft Sentinel is a sophisticated cloud-native SIEM platform that combines SIEM and SOAR capabilities. If you want to learn more about it, you can enroll in InfosecTrain’s Microsoft Sentinel training course. You will be able to master the Microsoft Sentinel service after completing the course. This course explains how to monitor Microsoft 365 security with Microsoft Sentinel. We will go through Microsoft Sentinel, what it can do, and how to use it. It will also discuss how to integrate Microsoft Sentinel with Microsoft 365.







 1800-843-7890 (India)
1800-843-7890 (India)